Posts
2987Following
697Followers
1545buherator
buheratorhttps://blog.deeb.ch/posts/avred-update/
buherator
buheratorhttps://cyberscoop.com/wordpress-two-factor-authentication-supply-chain/
buherator
buheratorI ordered it through Blackwell's, that is a UK company but ships @nostarch books to EU too, so you can avoid dealing with customs yourself. Order tracking needs improvement.
https://blackwells.co.uk/bookshop/product/Windows-Security-Internals-by-James-Forshaw/9781718501980
Sarah Jamie Lewis
sarahjamielewis@mastodon.socialI really try to like Firefox, but the last 5 minutes really captures the kind of papercut that happens often:
- I open a new tab and firefox informs me it has updated itself and needs to restart and won't allow any further operations until it does so.
- Fine, I close and restart.
- I reopen Firefox to find a brand new sponsored weather widget on my otherwise blank new tab page - from a source I would never otherwise visit.
Thanks for breaking my flow and the privacy breach, I guess.
Matthew Garrett
mjg59@nondeterministic.computerThe promised writeup of how I discovered that the Feeld dating app was protecting private data by doing client-side filtering: https://mjg59.dreamwidth.org/70061.html
screaminggoat
screaminggoat@infosec.exchangeBleeping Computer: Adobe fixes Acrobat Reader zero-day with public PoC exploit
References:
- APSB24-70 Security update available for Adobe Acrobat and Reader (10 September 2024)
- APSB24-57 Security update available for Adobe Acrobat and Reader (13 August 2024)
Okay I already have an EXPMON thread here (see parent toots above) so I'll orphan the original Adobe September 2024 Patch Tuesday toot. It should be noted that CVE-2024-41869 (7.8 high) UAF to arbitrary code execution in Adobe Acrobat and Reader is a Zero Day (Proof of Concept exploit in the wild exists before the vulnerability was patched, unknown if actually exploited). Apparently the August patch wasn't sufficient for the vulnerability CVE-2024-39383 (7.8 high, which should also be considered a zero-day). Haifei Li wrote on the Bad Place: "We tested the (exactly the same) sample on the "patched" Adobe Reader version, it displayed additional dialogs, but if the user clicked/closed those dialogs, the app still crashed! Same UAF bug!"
In yesterday's Adobe Reader security advisory, Adobe didn't call attention to the fact that a Proof of Concept exploit exists in the wild, or however they would normally word it.
#expmon #adobe #proofofconcept #zeroday #vulnerability #CVE_2024_41869 #CVE_2024_39383
Trail of Bits
trailofbits@infosec.exchangeWe've completed a comparative security assessment of authorization policy languages: Cedar, Rego, and the OpenFGA modeling language.
If you are a language designer or a software developer, our AWS-sponsored assessment also provides recommendations for improving policy language design and for securing systems that use policy languages.
https://buff.ly/4cSO63s
DCoder 🇱🇹❤🇺🇦
dcoderlt@ohai.socialAustralia really looked at GDPR and said “those fines are rookie numbers, mate”.
(from https://twitter.com/troyhunt/status/1597841957526568966 )
bert hubert 🇺🇦🇪🇺🇺🇦
bert_hubert@fosstodon.orgAs @echo_pbreyer reminded us, EU member states have revived their effort to force-install a child pornography scanner on our phones again. This idea was rejected twice before, but they'll keep trying. Here's an English transcript of what I said about this in Dutch parliament last year: https://berthub.eu/articles/posts/client-side-scanning-dutch-parliament/
Piotr Bazydło
chudypb@infosec.exchangeMy SharePoint RCE got fixed: CVE-2024-38018. Site Member privs should be enough to exploit.
I also found a DoS vuln that got patched today: CVE-2024-43466.
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2024-38018
screaminggoat
screaminggoat@infosec.exchangeHappy #PatchTuesday from Microsoft: 79 new CVEs, 4 NEW EXPLOITED ZERO DAYS:
- CVE-2024-43491 (9.8 critical) Microsoft Windows Update Remote Code Execution Vulnerability (EXPLOITED)
- CVE-2024-38226 (7.3 high) Microsoft Publisher Security Feature Bypass Vulnerability (EXPLOITED)
- CVE-2024-38217 (5.4 medium) Windows Mark of the Web Security Feature Bypass Vulnerability (EXPLOITED and PUBLICLY DISCLOSED)
- CVE-2024-38014 (7.8 high) Windows Installer Elevation of Privilege Vulnerability (EXPLOITED)
EDIT: @BleepingComputer has mentioned that CVE-2024-38217 was marked publicly disclosed. Updated this to reflect it. See related reporting Microsoft September 2024 Patch Tuesday fixes 4 zero-days, 79 flaws
#microsoft #vulnerability #zeroday #eitw #activeexploitation #cve
Anderson Nascimento
andersonc0d3@infosec.exchangeMeasuring non-determinism in the Linux kernel
https://shape-of-code.com/2024/09/08/measuring-non-determinism-in-the-linux-kernel/
screaminggoat
screaminggoat@infosec.exchangeCitrix security advisory: Citrix Workspace app for Windows Security Bulletin CVE-2024-7889 and CVE-2024-7890
Happy #PatchTuesday from Citrix.
- CVE-2024-7889 (CVSSv4: 7.0 high) LPE
- CVE-2024-7890 (CVSSv4: 5.4 medium) LPE
Fixed in Citrix Workspace app for Windows 2405 and later versions, Citrix Workspace app for Windows 2402 CU1 LTSR and later versions. No mention of exploitation.
screaminggoat
screaminggoat@infosec.exchangeIvanti security advisory: September 2024 Security Update
Happy #PatchTuesday from Ivanti. There are some serious vulnerabilities. I want to emphasize that Ivanti stated they "have no evidence of these vulnerabilities being exploited in the wild." See the following advisories:
- Security Advisory EPM September 2024 for EPM 2024 and EPM 2022
- Security Advisory Ivanti Cloud Service Appliance (CSA) (CVE-2024-8190)
- Security Advisory Ivanti Workspace Control (IWC)
The big ones:
- CVE-2024-29847 (perfect 10.0 critical 🥳 cc: @cR0w) deserialization in the agent portal of Ivanti EPM before 2022 SU6/September 2024 update allows unauth RCE
- CVE-2024-32840, CVE-2024-32842, CVE-2024-32843, CVE-2024-32845, CVE-2024-32846, CVE-2024-32848, CVE-2024-34783, CVE-2024-34785: unspecified SQL injection in Ivanti EPM before 2022 SU6/September 2024 update allow remote authenticated attacker with admin privileges to RCE
Melanie Imming ✅
meliimming@akademienl.socialIt is shocking that after moving from Google workspace to Proton as the back office for our professional email adresses etc, all the major Dutch institutions are blocking us as spam. All our contacts have to whitelist us individually. So I think we are forced to go back to Google, where we had this problem occasionally but not as massively as now. It seems the reason is that Microsoft, used by almost all institutions in NL, simply blocks all Proton mail .😈 ( DNS=OK configured)
abadidea
0xabad1dea@infosec.exchangeI would like to impress upon product managers that a code security review does not consist of me sitting down with the files in alphabetical order and reading each and every line exactly once in order and checking off whether it is or isn’t secure
hanno
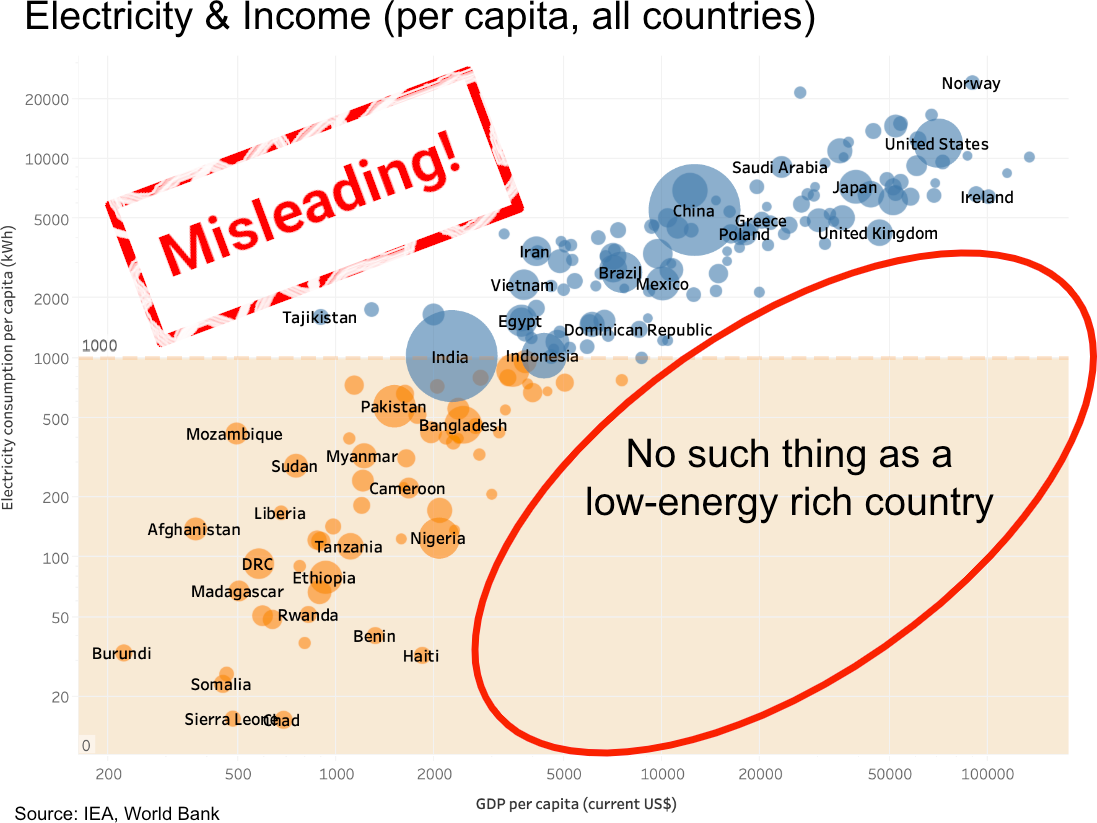
hanno@mastodon.socialThis widely shared infographic uses a trick to make its message appear much stronger than it actually is. It seems to show a strong correlation between energy consumption and the wealth of a country. By using a logarithmic scale, the correlation appears much stronger than it actually is. I covered this before in articles, and now have also uploaded a short video ⚡💸🎥 https://www.youtube.com/watch?v=2xZ6CihdKu0 🧵
Solarbird 
moira@mastodon.murkworks.net
@mcc (In short, as "AI summaries" corrupt more and more material, I think we're going to end up seeing more and more arguments where people are not reading the article, but instead are just the broken AI paraphrase, and starting fights based on what the LLM got wrong.)
Cassandra is only carbon now
xgranade@wandering.shop@mcc This, this, this. Whether or not LLMs "work" (they don't), whether or not they can be ethically trained (they can't), whether or not they can be reduced to an energy and CPU scale that's reasonable to run locally (they can't), LLMs still fundamentally invert the relationship we have with written language.