Posts
3471Following
717Followers
1584Vignesh Rao
sherl0ck__@bird.makeupMy talk on Webkit's JIT compilation at Off-By-One con is up! https://www.youtube.com/watch?v=9rt9ErQKnf8
Shawn Webb
lattera@bsd.networkIDA Pro is moving to a subscription model on 30 Sep 2024.
NOW is the time to obtain or renew your perpetual (non-subscription) license.
IDA Pro 8.x will be the last non-subscription version.
Jan Wildeboer 😷
jwildeboer@social.wildeboer.net
Had to verify. And yes. Kernighan and Ritchie really did this. TIL :)
Molly White
molly0xfff@hachyderm.ioThe Internet Archive lost its appeal in the Hachette case. What a huge, devastating loss for all of us.
Tamir Bahar
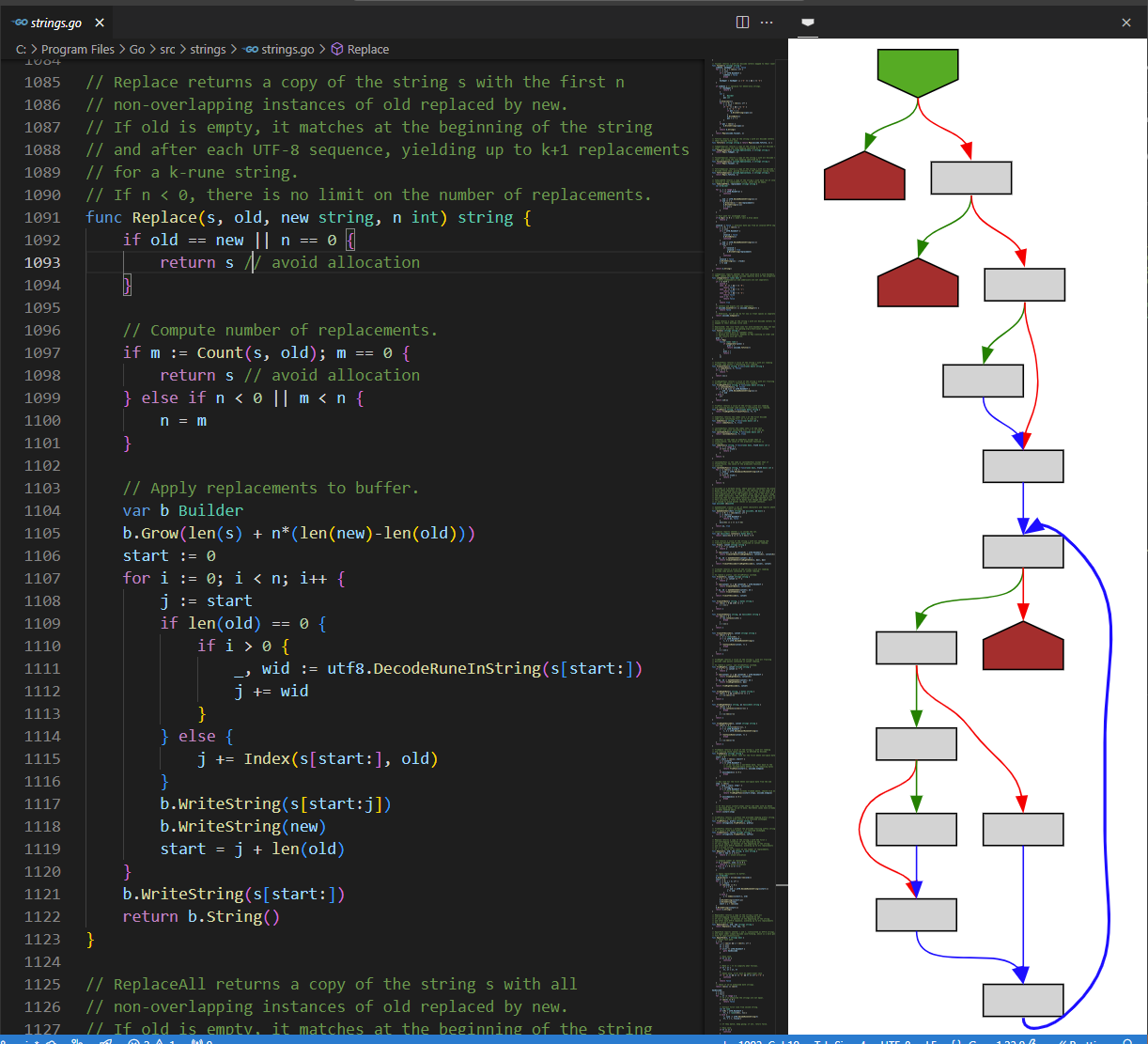
tmr232@mastodon.socialI always wanted to have IDA's graph-overview for source-code.
So I created a small VS-Code extension to do that for me.
https://marketplace.visualstudio.com/items?itemName=tamir-bahar.function-graph-overview
It currently supports Go and C; adding more languages should be relatively straightforward.
Eddie Chan
maded2@oldbytes.spaceThis must be the ultimate #C64
Dual SID chips, tube amp, full mechanical keyboard.
screaminggoat
screaminggoat@infosec.exchangeCisco security advisories includes a zero-day:
- Cisco Meraki Systems Manager Agent for Windows Privilege Escalation Vulnerability
CVE-2024-20430 (7.3 medium) incorrect handling of directory search paths (CWE-427: Uncontrolled Search Path Element) to EoP - Cisco Smart Licensing Utility Vulnerabilities
- CVE-2024-20439 (9.8 critical) Cisco Smart Licensing Utility Static Credential Vulnerability
- CVE-2024-20440 (9.8 critical) Cisco Smart Licensing Utility Information Disclosure Vulnerability
- Cisco Identity Services Engine Command Injection Vulnerability
CVE-2024-20469 (6.0 medium) insufficient validation of user-supplied input to authenticated command injection (the attacker must have valid Administrator privileges)- The Cisco PSIRT is aware that proof-of-concept exploit code is available for the vulnerability that is described in this advisory.
- Cisco Expressway Edge Improper Authorization Vulnerability
CVE-2024-20497 (4.3 medium) inadequate authorization checks for Mobile and Remote Access (MRA) users could allow an attacker to intercept calls or make phone calls spoofing another phone number - Cisco Duo Epic for Hyperdrive Information Disclosure Vulnerability
CVE-2024-20503 (5.5 medium) improper storage of an unencrypted registry key could allow an authenticated, local attacker to view sensitive information in cleartext
EDIT: What @BleepingComputer took away out of this is that CVE-2024-20439 is a backdoor admin account: Cisco warns of backdoor admin account in Smart Licensing Utility
#zeroday #cisco #patchtuesday #vulnerability #CVE_2024_20469 #cve #CVE_2024_20439
✧✦Catherine✦✧
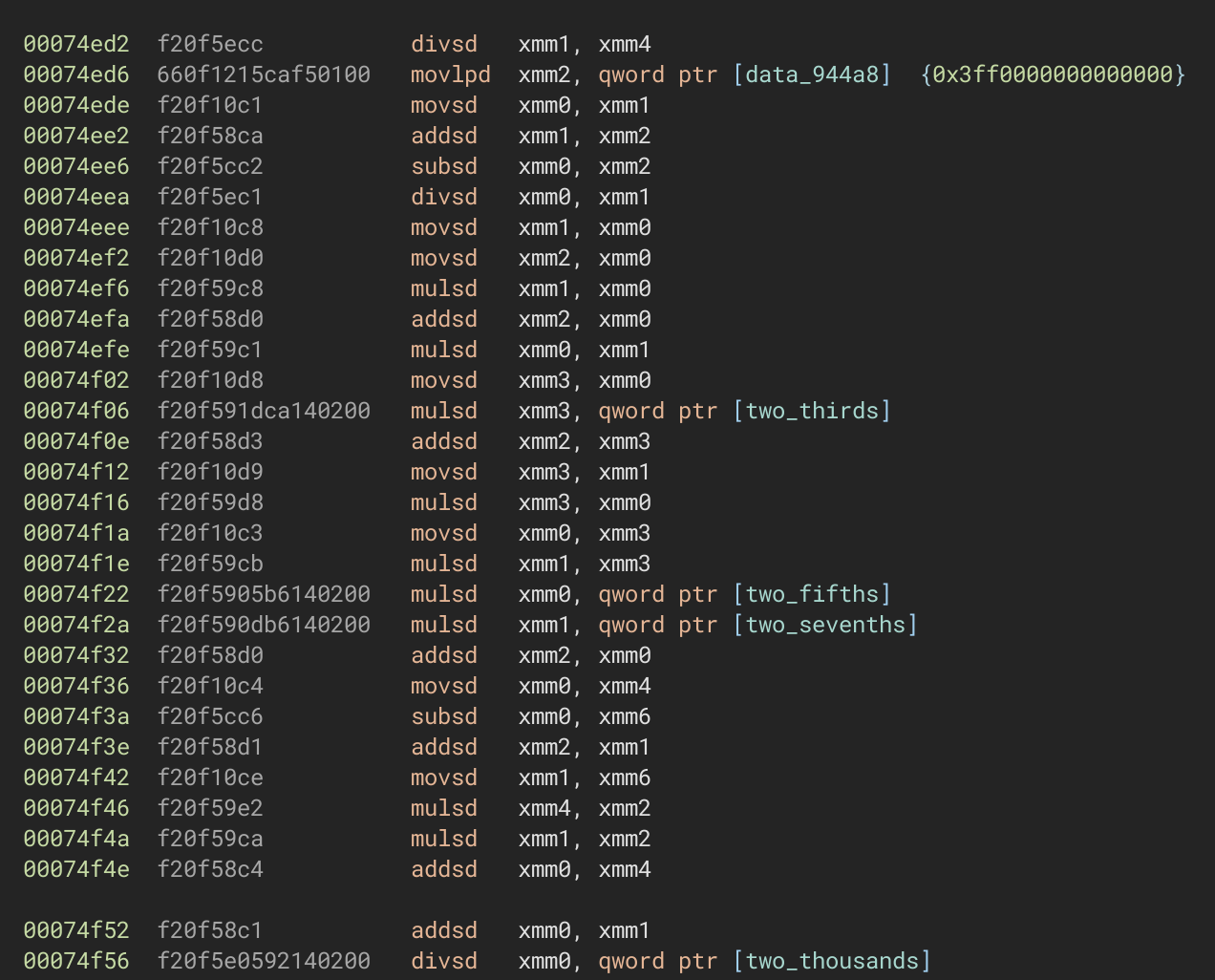
whitequark@mastodon.social(indistinctly yelling at the computer)
this is a series expansion of a natural logarithm
JA Westenberg
Daojoan@mastodon.social‘Everything happens for a reason’ sounds less comforting when the reason is very fucking poor planning
Trail of Bits
trailofbits@infosec.exchangeWe want your old GPUs that were destined to become e-waste.
We're repurposing outdated GPUs to tackle challenging computer security and program analysis problems. https://buff.ly/3XsbdgJ
Jeff Cutsinger
jeffcutsinger@tenforward.socialIn light of the Internet Archive losing its appeal to hachette, I just wanted to point out some websites you should avoid:
* https://annas-archive.li/
* https://downmagaz.net/
* https://ebook-hunter.org/
* https://forcoder.net/
* https://freemagazines.top/
* https://liber3.eth.limo/
If you were to download books from these websites, you might cut into hachette's more than three billion dollars of annual revenue. So make sure to avoid those websites and the following:
* https://libgen.is/
* https://oceanofpdf.com/
* https://pdfroom.com/
* https://pdfstop.com/
* https://pdfdrive.to/
* https://pdfmagazines.club/
* https://sci-hub.se/
* https://singlelogin.re/
* ... or any of the other sites listed at https://rentry.co/megathread-books
DEY!
dey@mastodon.socialFucking @buherator trying to kill me with this home made Palinka
Even Rouault
EvenRouault@mastodon.social@bagder To put in perspective:
- JPEG: libjpeg 6b encoder+decoder: 24,200 lines of C
- JPEG: libjpeg-turbo encoder+decoder: 127,000 of C and ASM (multi architectures)
- JPEG2000: openjpeg encoder+decoder: 50,000 lines of .C
- JPEG2000: Kakadu commercial encoder+decoder: 214,000 lines of C++ (only coresys component)
- libjxl: 150,000 lines for the core library, encoder+decoder (deps excluded)
(All above includes blank lines + inline doc)
So this is pretty much standard for a modern codec
quarkslab
quarkslab@infosec.exchange⚡ Operator Fabric is an open source platform built by the LF Energy Foundation (https://lfenergy.org/) for use in electricity, water and other utility operations.
Last May we did a security audit sponsored by the Open Source Technology Improvement Fund (https://ostif.org) 🙏
Read a summary of our findings and find the full report here:
Linux Kernel Security
linkersec@infosec.exchangeOngoing slab hardening efforts
Recently, there have been multiple efforts to make the exploitation of slab memory corruptions harder.
🧵[1/5]
Tara Tarakiyee
tarakiyee@mastodon.onlineI started a couple of forest fires to heat my burrito and I'm surprised by the results! It was still frozen in the middle by the end of the experiment, so it's far from perfect, but I think forest fires have a lot of potential and will revolutionize the burrito heating industry!
cynicalsecurity 
cynicalsecurity@bsd.network
@whitequark incidentally, there is a beautiful parallel which I always make when discussing security and "1st papers about an attack": the so-called "nth country problem".
This is an issue in nuclear proliferation which, in a few words, says that the nth country to become a nuclear power has the benefit of knowing that it works, and what works (unlike the Manhattan Project which started on the basis of pure theory).
The "nth country problem" was actually tested by the USA by giving three Physics PhD students access to all open literature on nuclear weapons and asking them to design a weapon. They did and analysis by LANL weapons designers actually showed that it would go b00m.
Hence, even if the 1st paper is extremely unlikely (compare to the Trinity test of the Pu implosion device - there was quite a bit of uncertainty that it would work) it does not mean that it cannot be done.
cynicalsecurity 
cynicalsecurity@bsd.network
@whitequark undeniably true. I'd also add that these attacks, while pretty niche, do attract the attention to a platform which was previously deemed "unbreakable".
In many ways this is similar to how work by people in the 90s (TESO, for example) drew my attention to µcode and John Heasman's work on ACPI to NIC firmware. Now look at the µcode panorama where you have an attack a day or firmware where there's an attack an hour (OK, sort of)
Nothing like breaking a myth.
Jerry 🦙💝🦙
jerry@infosec.exchangeI’ll reiterate what many others have said about the yubikey story - unless you’re the target of super sophisticated actors who do not want you to know they’ve stolen your yubikey*, this is a bit of a non-event and highlights the importance of keeping track of your yubikeys. Please don’t toss them, but do keep an eye out for further developments. Once an issue like this is identified, it attracts a lot of attention from many smart people and there may will be other findings in the future, but for now, yubikeys are good enough for most of us.
* I know there are a bunch of people convinced you’re being pursued by these advanced adversaries. I worry about you. For many reasons.
Patrick Lam
va2lam@discuss.systemsTired of using debuggers and manually exploring the program's state space? Too annoying to find the inputs you need to trigger the bug? Ever wanted to interactively see what your static analysis tool was really thinking?
With my collaborators from the University of Tartu (Karoliine Holter, Juhan-Oskar Hennoste, Simmo Saan, Vesal Vojdani), we have an Onward! paper about abstract debugging, where you can "step through" the abstract state of the program, as computed by a static analysis tool.
To appear at Onward! 2024: "Abstract Debuggers: Exploring Program Behaviors Using Static Analysis Results".
https://patricklam.ca/papers/24.onward.abs-debug.pdf
And a special thanks to the SIGPLAN-M mentoring program for matching me with these collaborators!