Posts
3020Following
700Followers
1548Linux Kernel Security
linkersec@infosec.exchangeOngoing slab hardening efforts
Recently, there have been multiple efforts to make the exploitation of slab memory corruptions harder.
🧵[1/5]
tarakiyee
tarakiyee@mastodon.onlineI started a couple of forest fires to heat my burrito and I'm surprised by the results! It was still frozen in the middle by the end of the experiment, so it's far from perfect, but I think forest fires have a lot of potential and will revolutionize the burrito heating industry!
cynicalsecurity 
cynicalsecurity@bsd.network
@whitequark incidentally, there is a beautiful parallel which I always make when discussing security and "1st papers about an attack": the so-called "nth country problem".
This is an issue in nuclear proliferation which, in a few words, says that the nth country to become a nuclear power has the benefit of knowing that it works, and what works (unlike the Manhattan Project which started on the basis of pure theory).
The "nth country problem" was actually tested by the USA by giving three Physics PhD students access to all open literature on nuclear weapons and asking them to design a weapon. They did and analysis by LANL weapons designers actually showed that it would go b00m.
Hence, even if the 1st paper is extremely unlikely (compare to the Trinity test of the Pu implosion device - there was quite a bit of uncertainty that it would work) it does not mean that it cannot be done.
cynicalsecurity 
cynicalsecurity@bsd.network
@whitequark undeniably true. I'd also add that these attacks, while pretty niche, do attract the attention to a platform which was previously deemed "unbreakable".
In many ways this is similar to how work by people in the 90s (TESO, for example) drew my attention to µcode and John Heasman's work on ACPI to NIC firmware. Now look at the µcode panorama where you have an attack a day or firmware where there's an attack an hour (OK, sort of)
Nothing like breaking a myth.
❄️☃️Merry Jerry🎄🌲
jerry@infosec.exchangeI’ll reiterate what many others have said about the yubikey story - unless you’re the target of super sophisticated actors who do not want you to know they’ve stolen your yubikey*, this is a bit of a non-event and highlights the importance of keeping track of your yubikeys. Please don’t toss them, but do keep an eye out for further developments. Once an issue like this is identified, it attracts a lot of attention from many smart people and there may will be other findings in the future, but for now, yubikeys are good enough for most of us.
* I know there are a bunch of people convinced you’re being pursued by these advanced adversaries. I worry about you. For many reasons.
Patrick Lam
va2lam@discuss.systemsTired of using debuggers and manually exploring the program's state space? Too annoying to find the inputs you need to trigger the bug? Ever wanted to interactively see what your static analysis tool was really thinking?
With my collaborators from the University of Tartu (Karoliine Holter, Juhan-Oskar Hennoste, Simmo Saan, Vesal Vojdani), we have an Onward! paper about abstract debugging, where you can "step through" the abstract state of the program, as computed by a static analysis tool.
To appear at Onward! 2024: "Abstract Debuggers: Exploring Program Behaviors Using Static Analysis Results".
https://patricklam.ca/papers/24.onward.abs-debug.pdf
And a special thanks to the SIGPLAN-M mentoring program for matching me with these collaborators!
Kagi HQ
kagihq@mastodon.socialHello, Fediverse! We're Kagi, and we're on a mission to create a friendlier, more human-centric internet that has the users' best interest in mind.
Our core product is a search engine that is ad-free, tracking-free, and fully supported by our users. We've worked hard to deliver a high-quality, fast, and reliable search experience without compromising user privacy: https://kagi.com/
Excited to engage with the community here.
Marcus Hutchins 
malwaretech@infosec.exchange
Absolute funniest TikTok trend in history went down this weekend. Someone posted about this “ATM glitch” they found. They went on to explained that you can deposit checks into ATMs and some of the money becomes available for withdrawal immediately, so you can write fake checks, deposit them, then withdraw the money before the check clears.
They made it sound like some kind of life hack and I guess most of TikTok is too young to know what check fraud is, so they had like hundreds of people uploading videos of themselves writing and depositing fraudulent checks into their own bank accounts tied to their real identities 💀
str4d 🛡️
str4d@abyssdomain.expert@soatok @duxsco @filippo @mbmcloughlin The flaw was fixed in firmware 5.7, which is also the firmware that added Ed25519 support to PIV. So the mitigation for vulnerable YubiKeys can't be Ed25519 for the PIV applet as it doesn't exist there.
Between that and explaining the difference between ECC and ECDSA to users, I'm not surprised they just say "use RSA".
Jon Henshaw
jon@henshaw.socialSaying the quiet part out loud
https://futurism.com/the-byte/openai-copyrighted-material-parliament
Dan Goodin
dangoodin@infosec.exchangeThe YubiKey 5, the most widely used hardware token for two-factor authentication based on the FIDO standard, contains a cryptographic flaw that makes the finger-size device vulnerable to cloning when an attacker gains brief physical access to it, researchers said Tuesday.
The cryptographic flaw, known as a side channel, resides in a small microcontroller that’s used in a vast number of other authentication devices, including smartcards used in banking, electronic passports, and the accessing of secure areas. While the researchers have confirmed all YubiKey 5 series models can be cloned, they haven’t tested other devices using the microcontroller, which is SLE78 made by Infineon and successor microcontrollers known as the Infineon Optiga Trust M and the Infineon Optiga TPM. The researchers suspect that any device using any of these three microcontrollers and the Infineon cryptographic library contains the same vulnerability.
DCoder 🇱🇹❤🇺🇦
dcoderlt@ohai.socialfuck yeah, another ghidra feature that I could never find in IDA 😎
You can make a typedef for an offset pointer, as in, “this is a pointer to offset 0x4 within a FooClass object”. And then the decompiler sees code like `SUB dword ptr [ESP + 0x8], 4` and figures out “ah, this turns it into a normal FooClass*” and makes things readable. Quite nice for inspecting C++ inheritance forests.
Viss
Viss@mastodon.social@LinuxAndYarn @zackwhittaker if i was elon musk rich, i'd never have let thinkgeek go away
Zack Whittaker
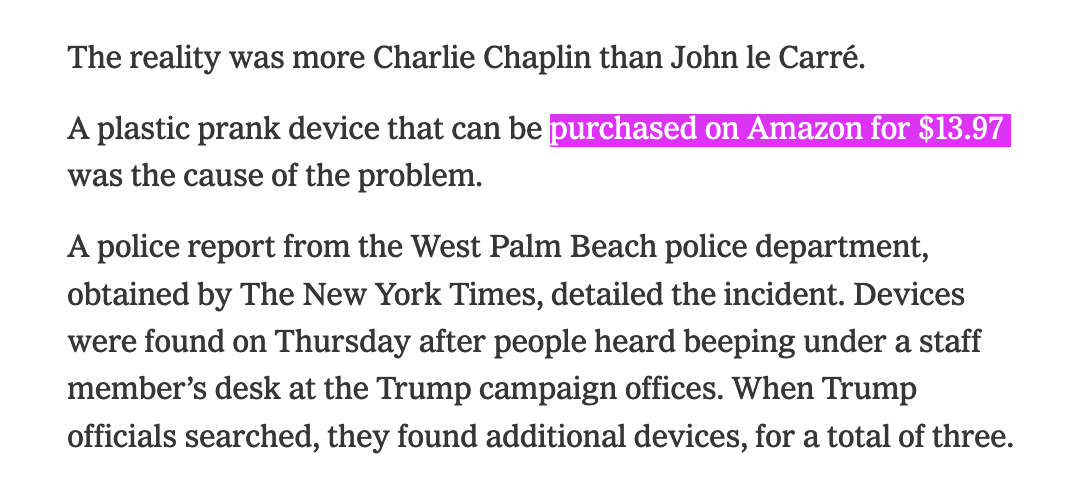
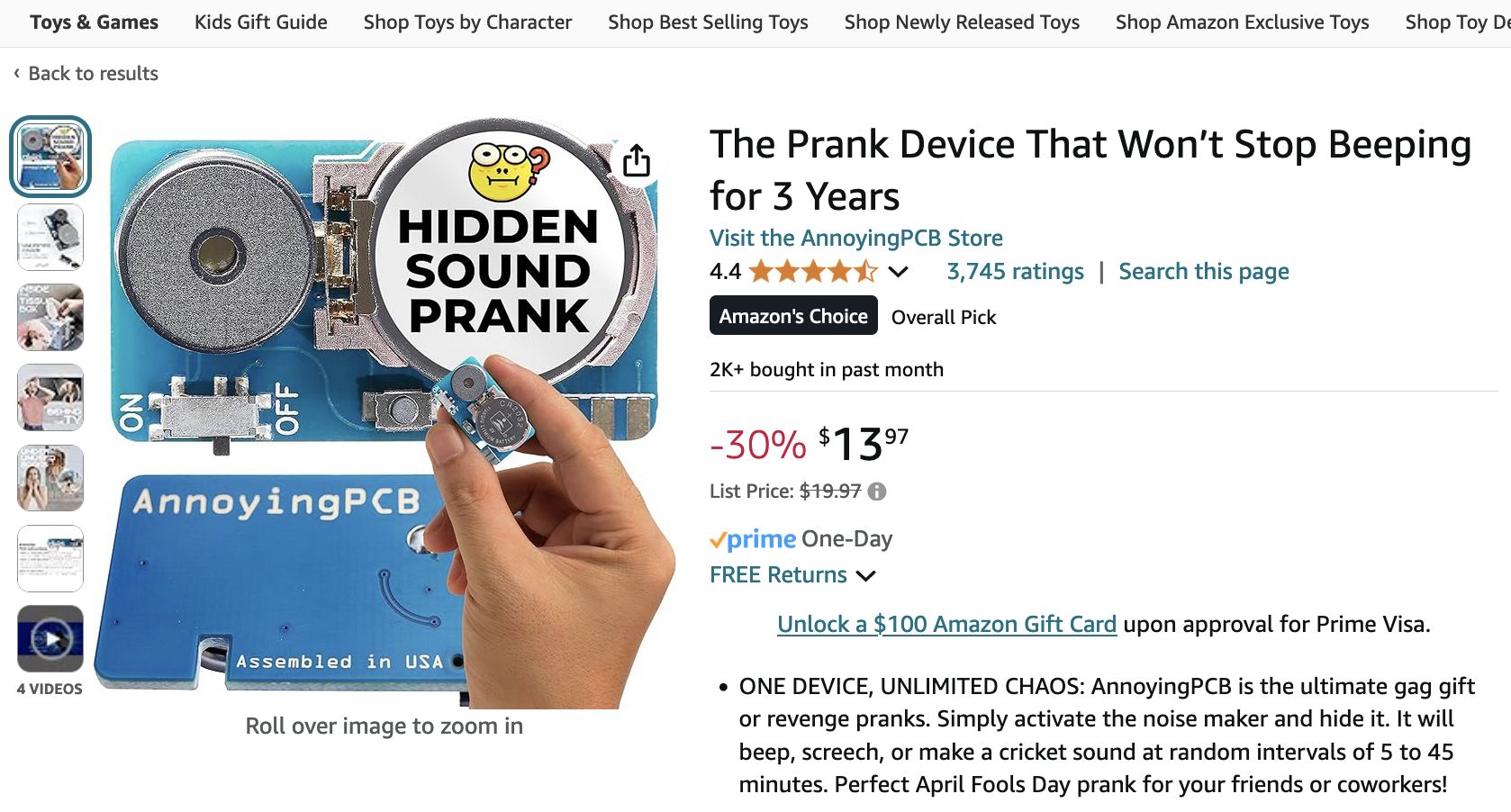
zackwhittaker@mastodon.socialThis is a real story. https://www.nytimes.com/2024/09/03/us/politics/trump-prank-devices.html
screaminggoat
screaminggoat@infosec.exchangeSecurity Week: CISA Warns of Avtech Camera Vulnerability Exploited in Wild
In yesterday's CISA ICS Advisory AVTECH IP Camera, CISA includes the following verbiage:
ATTENTION: Exploitable remotely/low attack complexity/public exploits are available/known public exploitation
Additionally, "An anonymous third-party organization confirmed Akamai's report and identified specific affected products and firmware versions." AVTECH SECURITY Corporation has not responded to requests to work with CISA to mitigate these vulnerabilities.
So there you have it CVE-2024-7029 (8.8 high) command injection vulnerability is likely an unpatched and exploited zero-day.
#CVE_2024_7029 #activeexploitation #zeroday #vulnerability #cve #avtech #cisa
Filippo Valsorda
filippo@abyssdomain.expertA couple notes about the Infineon timing side channel affecting most YubiKeys.
1. yubikey-agent is unaffected in the evil maid threat model as the attacker needs physical access *and PIN*
2. lol, Infineon
3. Go mitigates timing side-channels in ECDSA nonce inversion by not being clever and just using Fermat's little theorem, which is as simple as a constant time exponentiation by p - 2 (which can be optimized with @mbmcloughlin's addchain)
https://ninjalab.io/eucleak/
https://www.yubico.com/support/security-advisories/ysa-2024-03/
Will Smart
SmartAsABrick@techhub.social@tychotithonus Yubico advisory is up: https://www.yubico.com/support/security-advisories/ysa-2024-03/
Trend Zero Day Initiative
thezdi@infosec.exchangeWe've updated our blog on abusing file deletes to escalate privileges. We've also released PoC to demonstrate this. The exploit offers a high degree of reliability and eliminates all race conditions. It has been tested on the latest Windows 11 Enterprise. https://www.zerodayinitiative.com/blog/2022/3/16/abusing-arbitrary-file-deletes-to-escalate-privilege-and-other-great-tricks
BleepingComputer
BleepingComputer@infosec.exchangeD-Link is warning that four remote code execution (RCE) flaws impacting all hardware and firmware versions of its DIR-846W router will not be fixed as the products are no longer supported.
screaminggoat
screaminggoat@infosec.exchangeSecureLayer7: CVE-2024-37084: Spring Cloud Remote Code Execution
SecureLayer7 has been churning out zero-day vulnerabilities (publicly releasing information about vulnerabilities without a coordinated vulnerability disclosure with the impacted vendor or assigning CVEs) and proofs of concepts for vulnerabilities. According to Spring.io, Spring Cloud Data Flow is a microservices-based Streaming and Batch data processing platform deployed in Cloud Foundry and Kubernetes. CVE-2024-37084 (9.8 CRITICAL) is an arbitrary file write. SecureLayer7 used patch diffing to determine that it’s an insecure deserialization vulnerability that leads to remote code execution, and provides a proof of concept for it.
#vulnerability #CVE_2024_37084 #spring #cve #proofofconcept #poc