Posts
2704Following
681Followers
1504DCoder 🇱🇹❤🇺🇦
dcoderlt@ohai.socialfuck yeah, another ghidra feature that I could never find in IDA 😎
You can make a typedef for an offset pointer, as in, “this is a pointer to offset 0x4 within a FooClass object”. And then the decompiler sees code like `SUB dword ptr [ESP + 0x8], 4` and figures out “ah, this turns it into a normal FooClass*” and makes things readable. Quite nice for inspecting C++ inheritance forests.
Viss
Viss@mastodon.social@LinuxAndYarn @zackwhittaker if i was elon musk rich, i'd never have let thinkgeek go away
Zack Whittaker
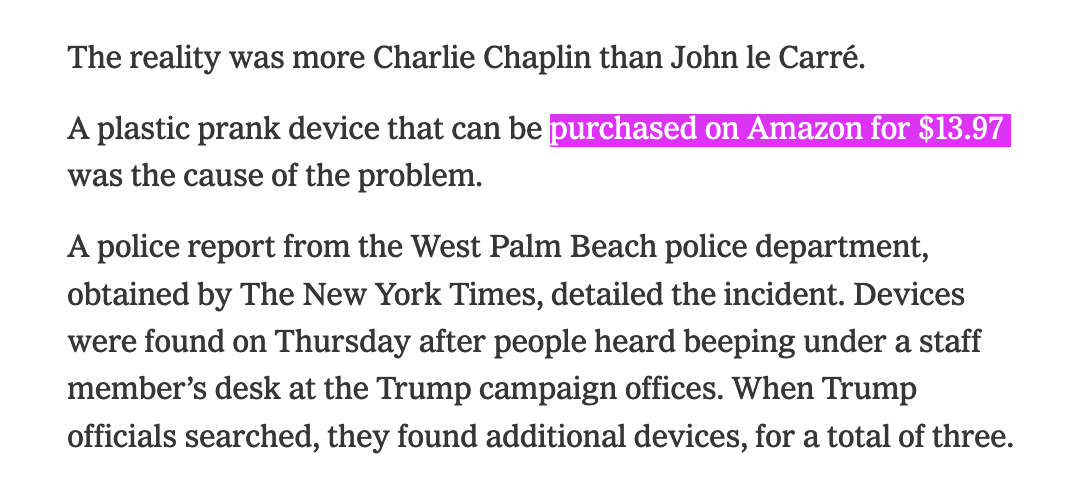
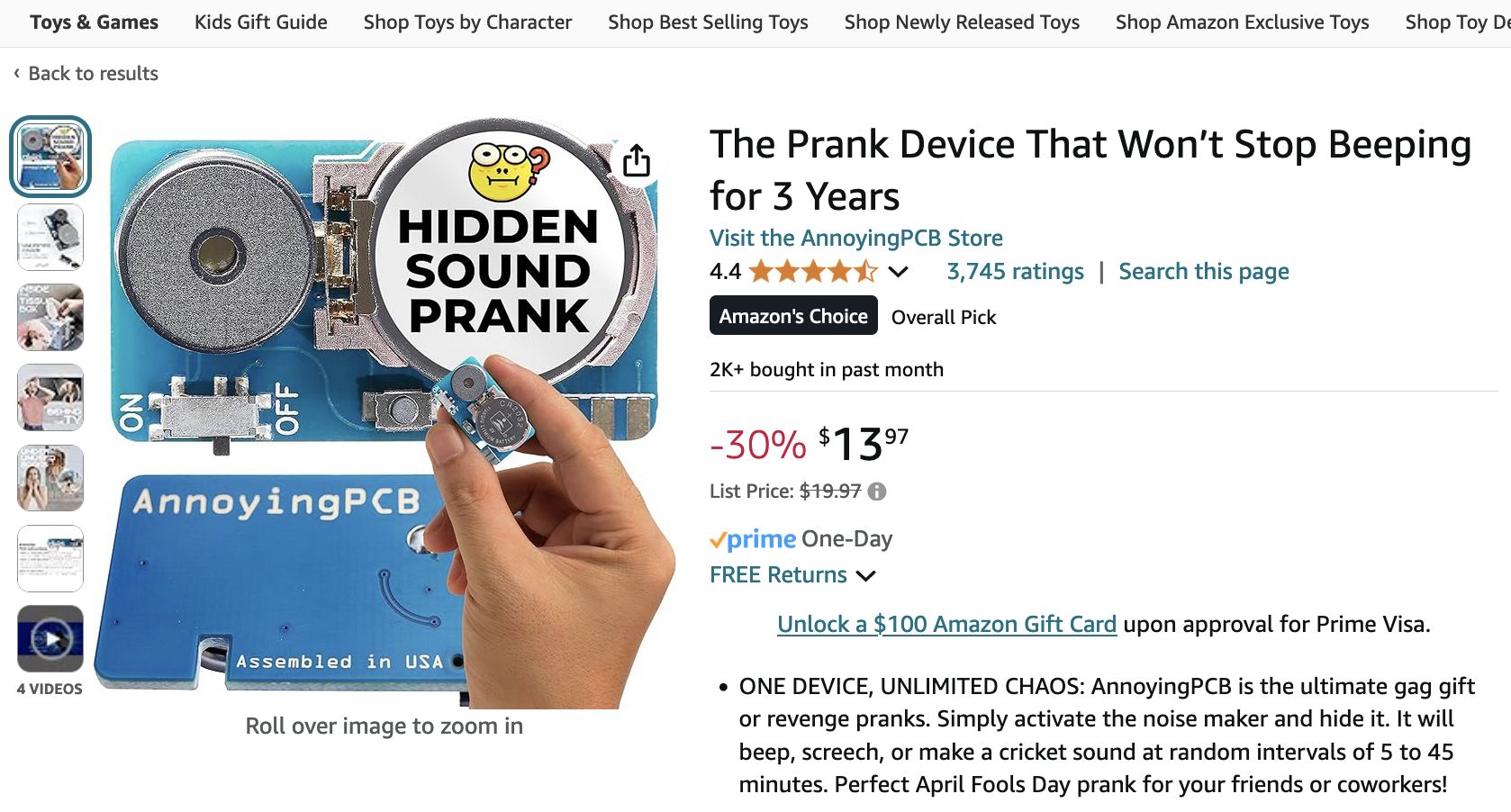
zackwhittaker@mastodon.socialThis is a real story. https://www.nytimes.com/2024/09/03/us/politics/trump-prank-devices.html
screaminggoat
screaminggoat@infosec.exchangeSecurity Week: CISA Warns of Avtech Camera Vulnerability Exploited in Wild
In yesterday's CISA ICS Advisory AVTECH IP Camera, CISA includes the following verbiage:
ATTENTION: Exploitable remotely/low attack complexity/public exploits are available/known public exploitation
Additionally, "An anonymous third-party organization confirmed Akamai's report and identified specific affected products and firmware versions." AVTECH SECURITY Corporation has not responded to requests to work with CISA to mitigate these vulnerabilities.
So there you have it CVE-2024-7029 (8.8 high) command injection vulnerability is likely an unpatched and exploited zero-day.
#CVE_2024_7029 #activeexploitation #zeroday #vulnerability #cve #avtech #cisa
Filippo Valsorda
filippo@abyssdomain.expertA couple notes about the Infineon timing side channel affecting most YubiKeys.
1. yubikey-agent is unaffected in the evil maid threat model as the attacker needs physical access *and PIN*
2. lol, Infineon
3. Go mitigates timing side-channels in ECDSA nonce inversion by not being clever and just using Fermat's little theorem, which is as simple as a constant time exponentiation by p - 2 (which can be optimized with @mbmcloughlin's addchain)
https://ninjalab.io/eucleak/
https://www.yubico.com/support/security-advisories/ysa-2024-03/
Will Smart
SmartAsABrick@techhub.social@tychotithonus Yubico advisory is up: https://www.yubico.com/support/security-advisories/ysa-2024-03/
Trend Zero Day Initiative
thezdi@infosec.exchangeWe've updated our blog on abusing file deletes to escalate privileges. We've also released PoC to demonstrate this. The exploit offers a high degree of reliability and eliminates all race conditions. It has been tested on the latest Windows 11 Enterprise. https://www.zerodayinitiative.com/blog/2022/3/16/abusing-arbitrary-file-deletes-to-escalate-privilege-and-other-great-tricks
BleepingComputer
BleepingComputer@infosec.exchangeD-Link is warning that four remote code execution (RCE) flaws impacting all hardware and firmware versions of its DIR-846W router will not be fixed as the products are no longer supported.
screaminggoat
screaminggoat@infosec.exchangeSecureLayer7: CVE-2024-37084: Spring Cloud Remote Code Execution
SecureLayer7 has been churning out zero-day vulnerabilities (publicly releasing information about vulnerabilities without a coordinated vulnerability disclosure with the impacted vendor or assigning CVEs) and proofs of concepts for vulnerabilities. According to Spring.io, Spring Cloud Data Flow is a microservices-based Streaming and Batch data processing platform deployed in Cloud Foundry and Kubernetes. CVE-2024-37084 (9.8 CRITICAL) is an arbitrary file write. SecureLayer7 used patch diffing to determine that it’s an insecure deserialization vulnerability that leads to remote code execution, and provides a proof of concept for it.
#vulnerability #CVE_2024_37084 #spring #cve #proofofconcept #poc
screaminggoat
screaminggoat@infosec.exchangeMozilla Foundation security advisories:
- 2024-39 Security Vulnerabilities fixed in Firefox 130
- 2024-40 Security Vulnerabilities fixed in Firefox ESR 128.2
- 2024-41 Security Vulnerabilities fixed in Firefox ESR 115.15
- 2024-42Security Vulnerabilities fixed in Focus for iOS 130
No mention of Firefox for iOS or Thunderbird (which would arrive in 2 separate advisories). Expect future advisories likely later today. No mention of exploitation.
Edited to include late advisory for Focus for iOS 130.
Silent Signal
silentsignal@infosec.exchangeThe recording of our @WEareTROOPERS presentation is now online, enjoy!
#TROOPERS24 - IBM i for Wintel Hackers
/r/netsec
_r_netsec@infosec.exchangeAnalysis of CVE-2024-37084: Spring Cloud Remote Code Execution https://blog.securelayer7.net/spring-cloud-skipper-vulnerability/
daniel:// stenberg://
bagder@mastodon.socialAI slide for the talk (work in progress):
AI does not save us
AI fools researchers think they found problems
AI assisted reports take longer to debunk
AI is an added burden for maintainers
/r/netsec
_r_netsec@infosec.exchangeTraceeshark: Deep Linux runtime visibility meets Wireshark https://github.com/aquasecurity/traceeshark
Frederik Borgesius
Frederik_Borgesius@akademienl.social'The Dutch Data Protection Authority imposes a fine of 30.5 million euro and orders subject to a penalty for non-compliance up to more than 5 million euro on Clearview AI... Clearview has built an illegal database with billions of photos of faces, including of Dutch people. The Dutch DPA warns that using the services of Clearview is also prohibited.' https://www.autoriteitpersoonsgegevens.nl/en/current/dutch-dpa-imposes-a-fine-on-clearview-because-of-illegal-data-collection-for-facial-recognition #Netherlands #clearview #law #tech #ai #privacy #dataprotection #surveillance
Marco Ivaldi
raptor@infosec.exchangeCome for the #OffensiveRust content, stay for the #ThrashMetal revival 🎸 https://infosec.exchange/@hnsec/113072354880406361
itszn
itszn13@bird.makeupMy v8 jit optimization exploit for 34c3 ctf:
https://gist.github.com/itsZN/9ae6417129c6658130a898cdaba8d76c
itszn
itszn13@bird.makeupBlazeFox firefox pwnable reference solution for BlazeCTF:
https://gist.github.com/itsZN/4dd40ff12d886e5b3984200a92c1a38a
itszn
itszn13@bird.makeupHere is my exploit for @plaidctf V8 exploit challenge. Bug was an n-day patched in chrome 66.0.3359.117
https://gist.github.com/itsZN/73cc299b9bcff1ed585e6206d1ade58e