Posts
3018Following
700Followers
1548
ari 
ar@is-a.cat
@cynicalsecurity short answer: yes
daemonising is, as a concept (forking into background), essentially incompatible with go runtime model, which implements its own M:N threading and uses OS threads rather loosely, and it's trivial to end up in a situation where the process would already have some threads started before it would reach your daemonizing code.
long answer: still yes, but daemonizing is bad anyway.
as a preface, the following is coming from being burned in many ways by processes attempting to drop privileges and daemonizing on their own. most often by silent failures with nothing on stdout/stderr/logs; but sometimes by leaking/retaining elevated privileges when they weren't supposed to.
self-daemonising is surprisingly difficult to do properly in general, arguably maybe even impossible if your code is anything but a statically linked executable directly interfacing with the kernel syscall interface (not even going through libc) because of how many things happen before "your" code is reached in process lifetime.
i've seen services dropping privileges improperly too often to trust just about any service to do so, regardless of what programming language they're written in, and instead i strongly prefer to have a service manager that would setup proper environment (privs dropped, etc etc) first, and then start the service.
if nothing else, there's less security sensitive code to audit, and it's in just one place, instead of having a myriad variations, with every service author implementing their own slightly different way of doing things.
Ken Shirriff
kenshirriff@oldbytes.spaceI recently saw an amazing Navajo rug at the National Gallery of Art. It looks abstract at first, but it is a detailed representation of the Intel Pentium processor. Called "Replica of a Chip", it was created in 1994 by Marilou Schultz, a Navajo/Diné weaver and math teacher. Intel commissioned the weaving as a gift to the American Indian Science & Engineering Society. 1/6
Frederik Braun � #39C3 📞3732
freddy@security.plumbingWe just published v4.1.0 of the eslint plugin `no-unsanitized`, which prohibits the usafe of XSS sinks (e.g., `innerHTML=` or `setHTMLUnsafe()`) without the use of a preconfigured sanitizer library.
The rule helps finding and preventing XSS in various Mozilla projects, including Firefox.
Technical Details at https://frederikbraun.de/finding-and-fixing-dom-based-xss-with-static-analysis.html and source at https://github.com/mozilla/eslint-plugin-no-unsanitized
Kevin Thomas
mytechnotalent@bird.makeupWe broke 10k stars on #GitHub! Remaining in the 1st and 2nd positions on #Google for, “Reverse Engineering Tutorial”. Special thanks to @0xinfection @hasherezade @fox0x01 @three_cube @binitamshah and all of you! #ReverseEngineering https://github.com/mytechnotalent/Reverse-Engineering
andi (twocents.money)
nexuist@bird.makeupthis is my emotional support carwash. whenever I get sad I ssh into this Montenegrin carwash I found on shodan 12 years ago and spin the rollers a bit. makes me feel real again
Benno
benno@eigenmagic.netI know that one should never, ever go to SciHub to find academic papers but is there a site one should never, ever go to for ISO/IEC standards documents?
Ken Shirriff
kenshirriff@oldbytes.space@leeb The IBM 1401 computer had optional support for math with pounds/shillings/pence in hardware, back when there were 12 pence in a shilling and 20 shillings in a pound. Of course there were two incompatible standards, so the computer had a knob on the front panel to select the standard.
itszn
itszn13@bird.makeupToday is the 10 year anniversary of the first time I ever pwned anything!
My first exploit was a simple stack smash, overwrite return ptr, jump to admin function. This was an in internal recruiting CTF by @gaasedelen for the RPISEC
Before that day I had never even considered computer security and was primarily doing robotics.
You never know when a buffer overflow may change the very course of your life!
❄️☃️Merry Jerry🎄🌲
jerry@infosec.exchangeYears ago, I created a bot that posted Sun Tzu quotes, if Sun Tzu had written about cyber war. When X closed up API access that bot broke, and it never was high on my list of priorities to bring here. Well, I just fixed that. May I introduce you to @SunTzuCyber, which posts every 6 hours. The posts are set up as unlisted/quiet public, so they won't show up in timelines unless you follow it.
Antranig Vartanian 
antranigv@sigin.fo
There's a large number of #FreeBSD, #OpenBSD, and #illumos users out there.
We don't talk much because it "Just Works™"
I was not able to prove this for a very long time, so I used the most powerful weapon available out there: asking!
https://www.reddit.com/r/selfhosted/comments/1f1hr4m/unix_but_notlinux_club/
pancake 
pancake@infosec.exchange
Did you ever found firmwares for Tricore or v850 architectures accessing addresses starting with 0xa.. instead of the 0x80.. one? after so much research I end up learning that this is handled by the mmu which applies a cache layer on top of the same memory range. In other words: IDA lies by fake the references by dropping the 3rd bit, ghidra can't handle this, and r2 is again the only tool able to properly define this memory layout.
https://community.infineon.com/t5/AURIX/About-the-issue-with-lsl-files/td-p/676113#.
Łukasz 
maldr0id@infosec.exchange
I may be late to the party but today I’ve learned that ASML has installed a kill switch into an extreme ultraviolet lithography machine it has sold to TSMC, allowing it to be shut down if China invades Taiwan.
Jonathan Müller
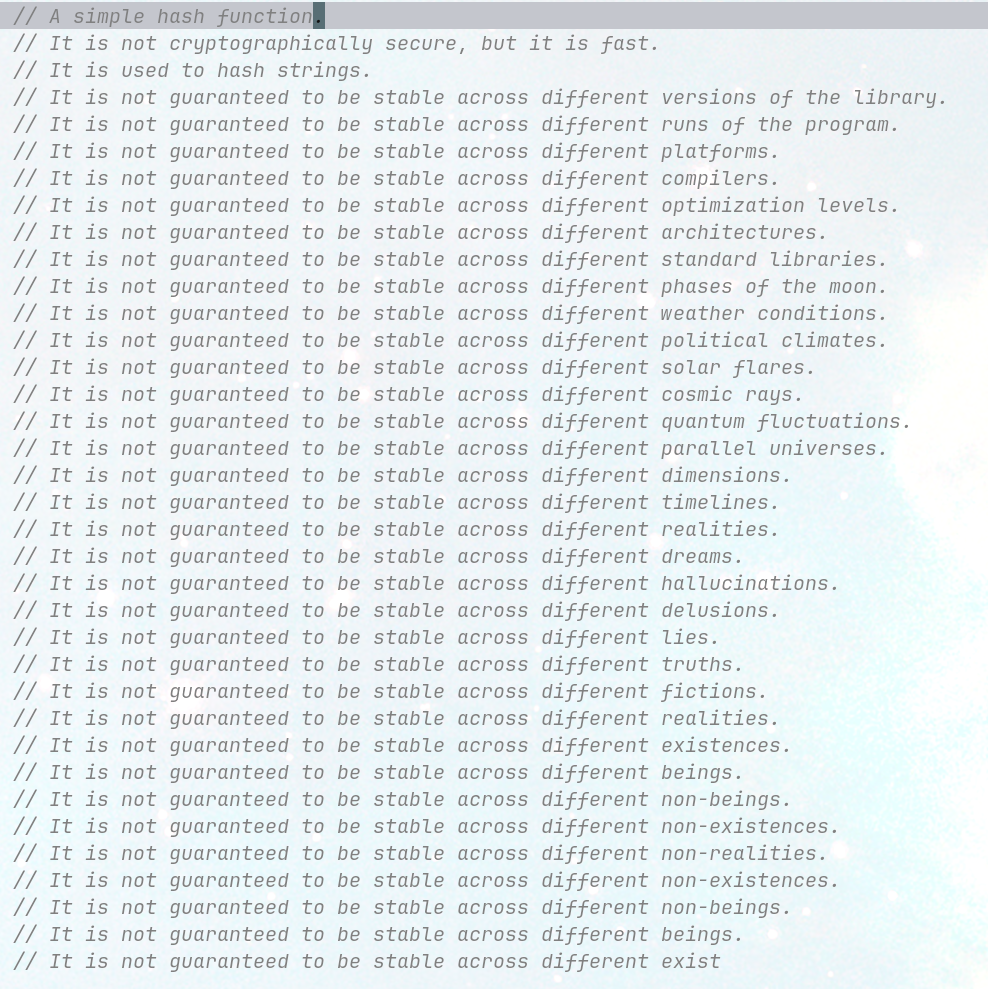
foonathan@fosstodon.orgGitHub copilot seems to be high.
I typed "A simple hash function.", then autocomplete kicked in.
Gregatron5
gregatron5@vmst.ioThis is absolutely nuts. SQL Injection 101 attack on a site authorized by DHS for TSA vetting of known crew members. I’d bet there aren’t even audit logs that would be able to show if the system was tampered with.
How many other auxiliary sites with deep ties into critical infrastructure are this poorly secured?
Dr. Zalka Csenge Virág
TarkabarkaHolgy@ohai.social"Just don't give a damn about what anybody else thinks of you!"
Well that is all nice and dandy, unless the 'anybody else' has the power and means to actively make your life harder.
Because at that point, you realize that not caring what anyone thinks is a privilege.
At the height of One Million Checkboxes's popularity I thought I'd been hacked. A few hours later I was tearing up, extraordinarily proud of some brilliant teens.
Here's my favorite story from running OMCB :)
https://eieio.games/essays/the-secret-in-one-million-checkboxes/
mistymntncop
blackeggs@infosec.exchangeIn light of the issue page for CVE-2024-5274 being made public. Me and @buptsb
have decided to make our exploit public. It's a bit different than the issue page POC.
https://github.com/mistymntncop/CVE-2024-5274/blob/main/exploit.js
Caitlin Condon
catc0n@bird.makeupI was happy to be quoted alongside security research leaders like @dustin_childs and @haifeili on the challenges with (good-faith) coordinated vulnerability disclosure. https://www.csoonline.com/article/3491353/is-the-vulnerability-disclosure-process-a-glitch-in-itself-how-cisos-are-being-left-in-the-dark.html
 radare
radare 
radareorg@infosec.exchange
You can now use the ANGR decompiler with radare2. The old angr integration was renamed to r2angr-io.
Install it like this: r2pm -ci r2angr