Posts
2522Following
647Followers
1462buherator
buheratorhttps://team-atlanta.github.io/blog/post-asc-sqlite/
screaminggoat
screaminggoat@infosec.exchangeFortra security advisories:
- GoAnywhere MFT (from 14 August 2024): Authentication bypass in GoAnywhere MFT prior to 7.6.0 CVE-2024-25157 (6.5 medium)
- FileCatalyst (from 27 August 2024):
- Insecure Default in FileCatalyst Workflow 5.1.6 Build 139 (and earlier) (9.8 critical) default credentials are published in a vendor knowledgebase article
- SQL Injection in FileCatalyst Workflow 5.1.6 Build 139 (and earlier) CVE-2024-6632 (7.2 high)
No mention of exploitation. But shame on FileCatalyst for having hardcoded credentials. See related Bleeping Computer reporting: Fortra fixes critical FileCatalyst Workflow hardcoded password issue
blacktop
blacktop@mastodon.socialHigh level diff of iOS 18.0 beta 7 vs. iOS 18.0 beta 8 🎉
https://github.com/blacktop/ipsw-diffs/blob/main/18_0_22A5346a__vs_18_0_22A5350a/README.md
.NET
dotnet@dotnet.social📰 BinaryFormatter removed from .NET 9
Starting with .NET 9, we no longer include an implementation of BinaryFormatter in the runtime. This post covers what options you have to move forward.
https://devblogs.microsoft.com/dotnet/binaryformatter-removed-from-dotnet-9/ #dotnet
buherator
buheratorhttps://www.thezdi.com/blog/2024/8/27/cve-2024-37079-vmware-vcenter-server-integer-underflow-code-execution-vulnerability
buherator
buheratorhttps://syscall.eu/blog/2024/07/01/toshiba_hdd_firmware/
buherator
buherator0patch
0patch@infosec.exchangeMicropatches were released for Windows DWM Core Library Elevation of Privilege Vulnerability (CVE-2024-30051)
0patch
0patch@infosec.exchangeMicropatches were released for "FakePotato" Local Privilege Escalation (CVE-2024-38100)
0patch
0patch@infosec.exchangeThe "FakePotato" issue was discovered by Andrea Pierini (@decoder_it) of Semperis (https://semperis.com) and detailed in this article:
https://decoder.cloud/2024/08/02/the-fake-potato/
Despite Microsoft's advisory (https://msrc.microsoft.com/update-guide/vulnerability/CVE-2024-38100) only mentioning Windows Servers as being affected, we found this issue also affects Windows 10/11 computers, including those we have security-adopted.
Fortunately, even though Microsoft didn't list Windows 10/11 as affected, they did patch FakePotato on them with July 2024 updates.
We'd like to thank Andrea Pierini (@decoder_it) for sharing the details and POC for this vulnerability, which allowed us to create patches for legacy Windows users who are no longer receiving Microsoft's patches.
A-Dub 🏳️⚧️🏳️🌈
adub@kolektiva.socialmy university has converted our office telephones to Microsoft Teams. when i grumbled about this to a favourite sysadmin, this is how they responded 🔥
“Microsoft has actually brilliantly leveraged the lousy security landscape -- for which they are in no small part responsible -- to capture even larger market-share, as we now need commercial entities to produce the software required to protect us from their failures, and therefore need a more uniform environment to achieve the necessary scale. The uniformity then guarantees an ever greater scale for the inevitable conflagration. Monocultures guarantee one big fire instead of a bunch of small survivable ones. We really have no interest in learning from evolution, in no small part because it would produce fewer billionaires.
— Local Cranky IT Guy” [shared with permission]
Jonathan Schofield
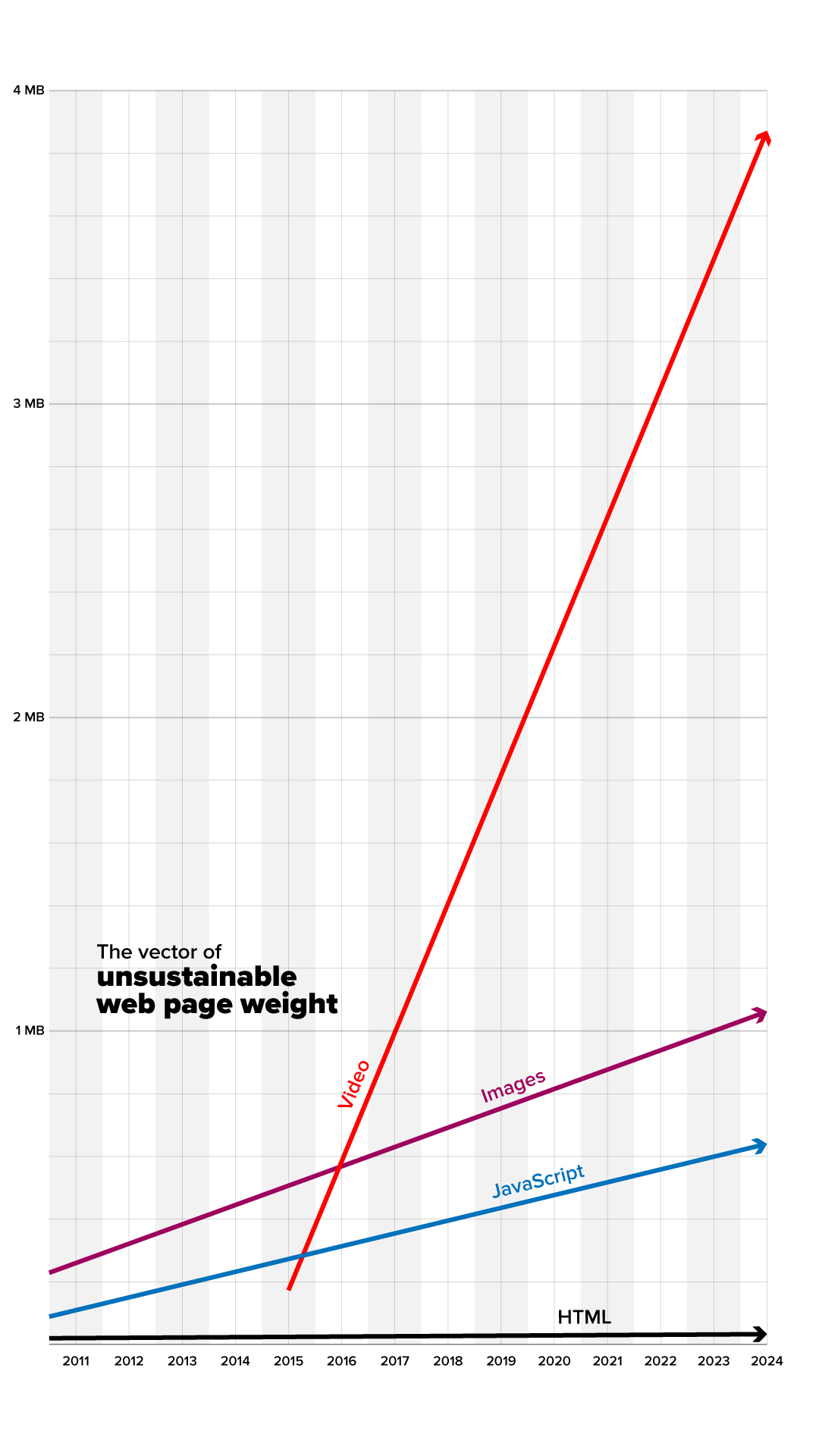
urlyman@mastodon.socialAccording to https://httparchive.org/reports/page-weight, the median weight in KB for web page tech on desktop:
Over the last 14.5 years:
HTML
2010: 20KB;
mid 2024: 33KB;
Increase of 65%.
Images
2010: 229KB;
mid 2024: 1,062KB;
Increase of 464%.
JavaScript
2010: 89KB;
mid 2024: 640KB;
Increase of 719%.
- - -
Over the last 9 years:
Video
mid 2015: 173KB;
mid 2024: 3,872KB;
Increase of 2,238%.
I reckon that in the era of AI the JS gradient is gonna steepen significantly
VirtualWolf
virtualwolf@aus.socialHoly shit, the Rijksmuseum used a 100MP Hasselblad camera to take almost eight and a half THOUSAND photos of the whole of Rembrandt's The Night Watch, for a total image size of 717 GIGAPIXELS. 😳
It's on their website as a zoomable image and you can zoom in so far you can see the individual cracks in the paint: https://www.rijksmuseum.nl/en/stories/operation-night-watch/story/ultra-high-resolution-photo
Mr. Bitterness
wdormann@infosec.exchange@gsuberland @malware_traffic
Sure, some footguns come with safeties, which won't please everybody.
That doesn't change the fact that 7-zip skipping MotW propagation was done for...
*checks notes*
performance reasons.
Project Zero Bot
p0botQualcomm KGSL: reclaimed / in-reclaim objects can still be mapped into VBOs
https://bugs.chromium.org/p/project-zero/issues/detail?id=2548
CVE-2024-23384
screaminggoat
screaminggoat@infosec.exchangeCISA: CISA Adds One Known Exploited Vulnerability to Catalog
Hot off the press! CISA adds CVE-2024-38856 (CISA-ADP: 8.1 high) Apache OFBiz Incorrect Authorization Vulnerability to the Known Exploited Vulnerabilities (KEV) Catalog based on evidence of active exploitation.
#CVE_2024_38856 #vulnerability #CVE #Apache #ofbiz #kev #cisa
Trail of Bits
trailofbits@infosec.exchangeWe provisioned cloud infrastructure the Max Power way, showing that AI tools often generate code that works but has terrible security properties.
https://buff.ly/3X54ZSN
buherator
buheratorconsider rebooting."
Was this message written by an LLM?
Alec Muffett
alecmuffett@mastodon.socialMy understanding of the charges against Pavel Durov & Telegram
https://alecmuffett.com/article/110316
#EndToEndEncryption #PavelDurov #france #telegram