Posts
2469Following
662Followers
1486Royce Williams
tychotithonus@infosec.exchangeGoogle's removal of the estimated number of search results is particularly user-hostile.
And it's me. I'm "user".
There's a specific kind of searching where you know that there shouldn't be a ton of results, and you are adding exclusions until your search matches the expected result space.
And now that's impossible (without scrolling to the bottom to see how many pages of results there are).
sha1lan
sha1lan@infosec.exchangeSome thoughts on memory safety
https://pacibsp.github.io/2024/some-thoughts-on-memory-safety.html
This post briefly describes some theoretical aspects of memory safety that feel important to me but that aren't always obvious from how I see memory safety being discussed:
1. Memory unsafety is a specific instance of a more general pattern of handle/object unsafety
2. Memory unsafety is relative to a particular layer in a stack of abstract machines
3. Memory unsafety matters because it violates local reasoning about state
4. Safe languages use invariants to provide memory safety, but these invariants do not define memory safety
Also, not sure what was up with the embed in my last post, hopefully this one works.
cynicalsecurity 
cynicalsecurity@bsd.network
Another SolarWinds RCE vulnerability…
… I instantly had the image from Hunt for Red October when the Soviet ambassador tells the US SecState that they needed help and SecState says "Don't tell me you lost _another_ submarine!"

Mr. Bitterness
wdormann@infosec.exchangeI have some words for the developers who decided that it was completely reasonable to expect a user to be able to precisely hit a single pixel to be able to resize a window.
I've seen this on both Windows and Linux. 🤦♂️
Trammell Hudson
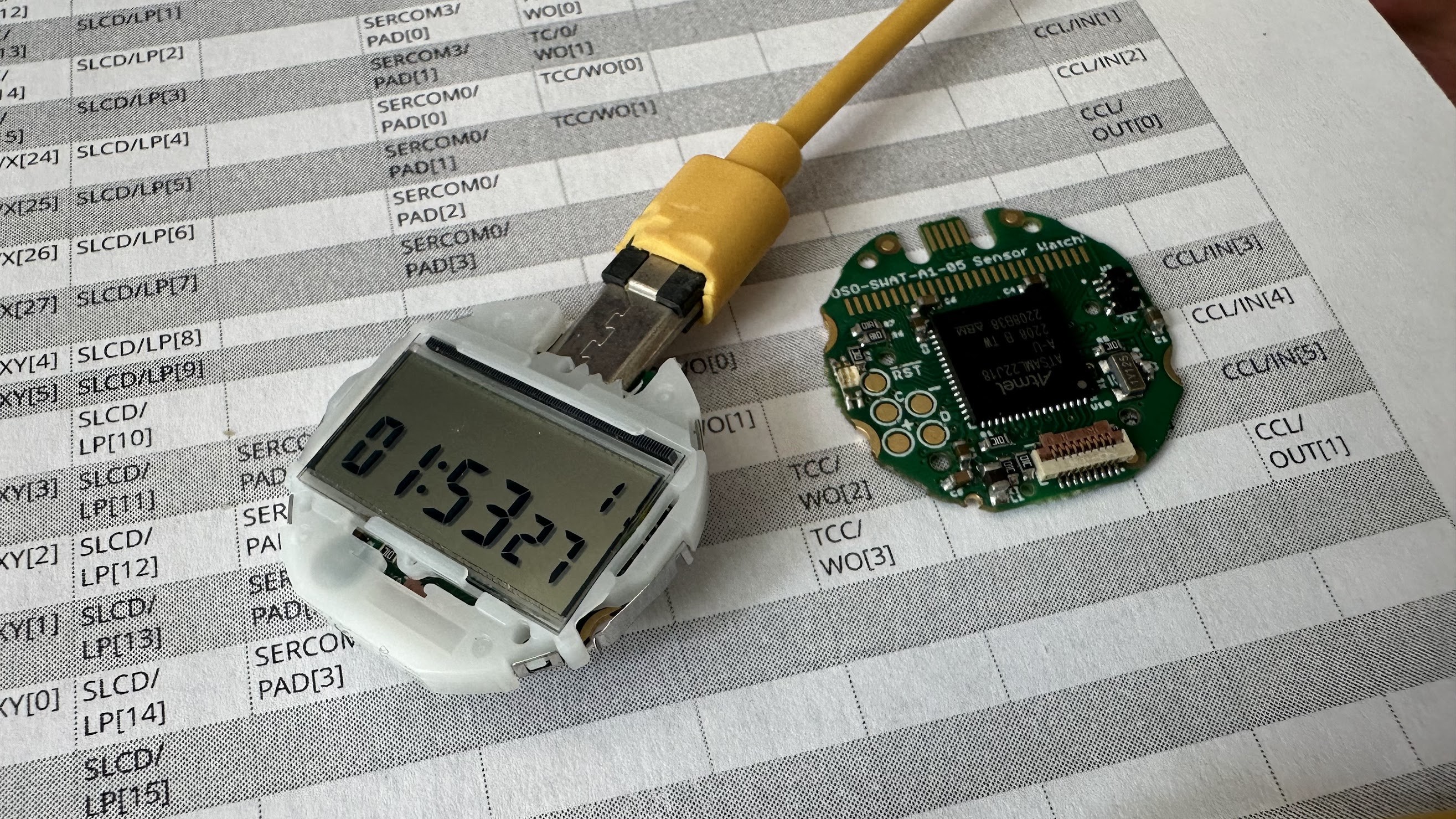
th@v.stThe SensorWatch LCD works from Micropython! https://github.com/osresearch/micropython/tree/sensorwatch
screaminggoat
screaminggoat@infosec.exchangeVersa security advisory: Versa Security Bulletin: Update on CVE-2024-39717 – Versa Director Dangerous File Type Upload Vulnerability
See parent toot above for CISA adding CVE-2024-39717 to the KEV Catalog. Here is some notable information:
- CVE-2024-39717 affects all Versa SD-WAN customers using Versa Director, that have not implemented the system hardening and firewall guidelines.
- The impacted users were Managed Service Providers
- "This vulnerability has been exploited in at least one known instance by an Advanced Persistent Threat actor."
- The threat actors had Provider-Data-Center-Admin or Provider-Data-Center-System-Admin privileges, in order to upload malicious files.
- Impacted customers failed to implement system hardening and firewall guidelines, with an internet-exposed management port.
Versa released a patch to address CVE-2024-39717, and provided Firewall Guidelines and System Hardening guidance.
Note: A CISA joint cybersecurity advisory from 2022 states that “threat actors can use a vulnerable MSP as an initial access vector to multiple victim networks, with globally cascading effects.” This security advisory was published today while all of the other URLs in NVD/Mitre are behind a loginwall.
cc: @ntkramer
#CVE_2024_39717 #vulnerability #CVE #Versa #cyberespionage #apt #KEV #KnownExploitedVulnerabilitiesCatalog #eitw #activeexploitation
/r/netsec
_r_netsec@infosec.exchangeGNU/Linux Sandboxing - A Brief Review https://hardenedlinux.org/blog/2024-08-20-gnu/linux-sandboxing-a-brief-review/
rostiger
rostiger@merveilles.townMost mirrors of libgen are now down. Anna's Archive is fighting to keep the lights on.
https://annas-archive.org/
daniel:// stenberg://
bagder@mastodon.socialLast year on this day the bogus #curl CVE arrived that triggered a series of events that subsequently made #curl become a CNA.
https://daniel.haxx.se/blog/2023/08/26/cve-2020-19909-is-everything-that-is-wrong-with-cves/
0xor0ne
0xor0ne@infosec.exchangeBrief intro on how to use eBPF for syscalls tracing
Carnage4Life
carnage4life@bird.makeupAndy Jassy talks about the benefits Amazon is seeing from their AI coding assistant. It’s widespread that devs are more productive with these tools.
The question is whether this is like accountants and Excel where it creates jobs or travel agents & the web where it kills them.
Linux Kernel Security
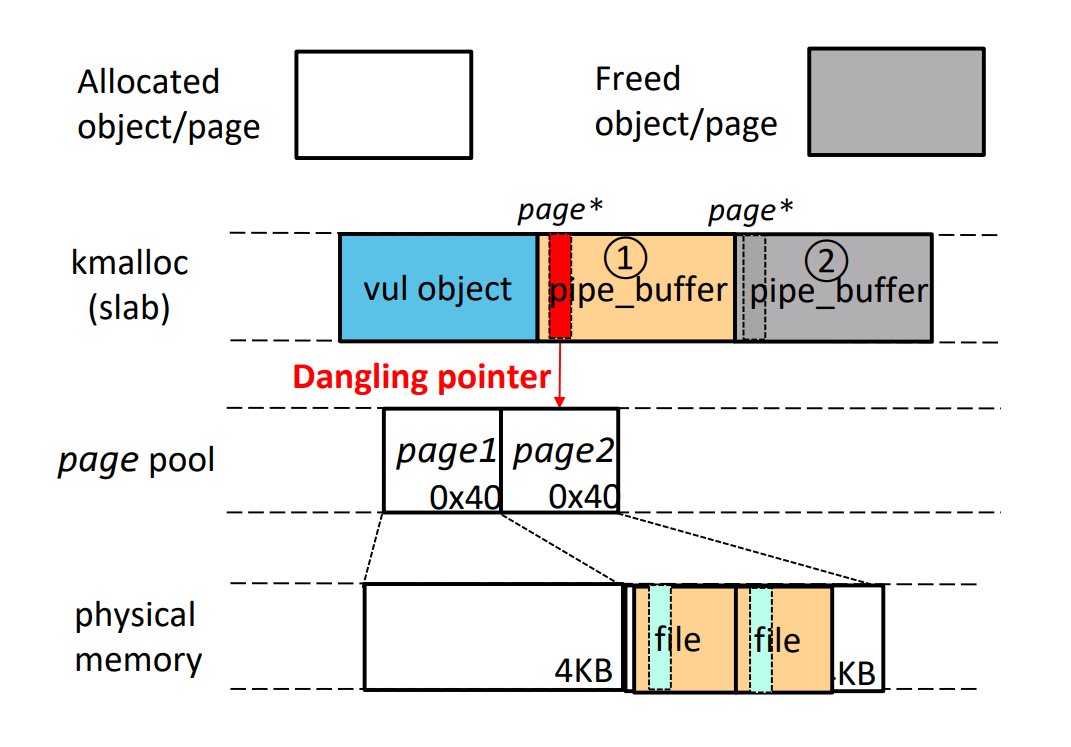
linkersec@bird.makeupPageJack: A Powerful Exploit Technique With Page-Level UAF
A talk by @pkqzy888 et al. about overwriting slab objects containing a `struct page *` field to achieve arbitrary read/write in physical memory.
Jiří Vinopal
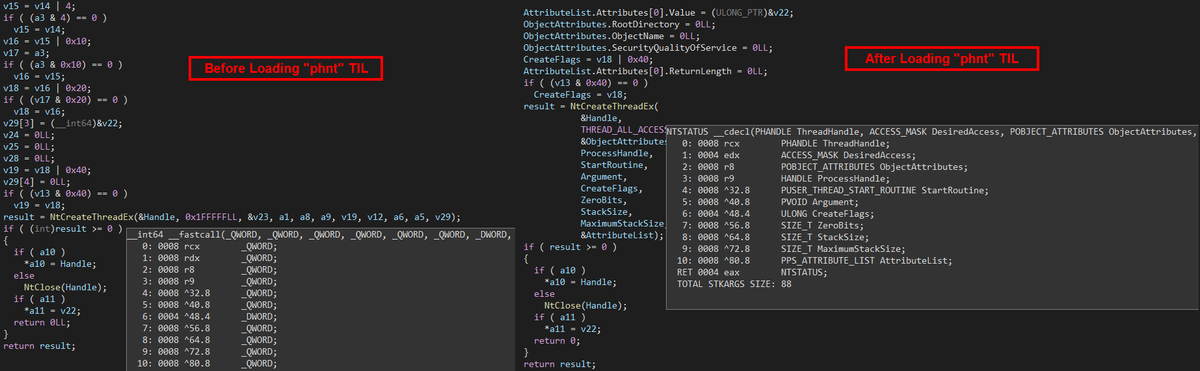
vinopaljiri@bird.makeupSo I made a thing ☺️
Converted #phnt (Native API header files from the System Informer project) to #IDA TIL, IDC.
To import "phnt" types and function definitions to IDA and help with Reverse Engineering.
@hexrayssa @mrexodia
Introducing #IDA_PHNT_TYPES:
https://github.com/Dump-GUY/IDA_PHNT_TYPES
Display Name
Teufelchen@hal9.oooBeing a C programmer in 2024 is so ridiculous, look what I need to do! Every (!) evening I have to charge my sacrifice cats, complete the ritual and pray to the gods just to be as memory safes as Ru^\x00
Programm terminated with signal SIGSEGV, Segmentation fault
Stefano Marinelli
stefano@bsd.cafeHappy Birthday, Linux! 
From: torvalds@klaava.Helsinki.FI (Linus Benedict Torvalds)
Newsgroups: comp.os.minix
Subject: What would you like to see most in minix?
Summary: small poll for my new operating system
Message-ID:
Date: 25 Aug 91 20:57:08 GMT
Organization: University of Helsinki
Hello everybody out there using minix -
I'm doing a (free) operating system (just a hobby, won't be big and
professional like gnu) for 386(486) AT clones. This has been brewing
since april, and is starting to get ready. I'd like any feedback on
things people like/dislike in minix, as my OS resembles it somewhat
(same physical layout of the file-system (due to practical reasons)
among other things).
I've currently ported bash(1.08) and gcc(1.40), and things seem to work.
This implies that I'll get something practical within a few months, and
I'd like to know what features most people would want. Any suggestions
are welcome, but I won't promise I'll implement them :-)
Linus (torvalds@kruuna.helsinki.fi)
PS. Yes - it's free of any minix code, and it has a multi-threaded fs.
It is NOT protable (uses 386 task switching etc), and it probably never
will support anything other than AT-harddisks, as that's all I have :-(.
Matthew Green
matthew_d_green@ioc.exchangeApropos Pavel Durov’s arrest, I wrote a short post about whether Telegram is an “encrypted messaging app”. https://blog.cryptographyengineering.com/2024/08/25/telegram-is-not-really-an-encrypted-messaging-app/
kravietz 🦇
kravietz@agora.echelon.pl#Telegram is a tricky ecosystem from security perspective, because it’s quite diverse and complex:
- Public groups and chats are widely used by both #Russia and #Ukraine. These include both publicly available and “private” (invite-only) chats neither can be really considered secret because…
- …group chats can’t be end-to-end encrypted (E2EE), so their contents are readable to at least Telegram operators, probably as easily as running a single SQL query.
- Telegram bots don’t support E2EE either.
So here’s an important distinction: while Telegram is great and highly usable for disseminating public or semi-public information (unencrypted public or invite-only groups), it’s quite poor for highly confidential communications. Yet, especially the Russian side uses it a lot for just that - there are reports of “secret groups” used for front-line command or control, correction of fire or as a channel for communication with spies and collaborators in Ukraine. Except these “secret groups” really aren’t, at least not in OPSEC and cryptographic sense (groups can’t use E2EE in Telegram).
This is one purely marketing win for Telegram, because even mainstream journalists notoriously confuse these concepts.
Yes, it is technically possible that a Russian operator opens an actual “secret chat” with each of his collaborator, but it’s highly impractical and I doubt majority of them do it.
Which is further confirmed by the panic caused by detention of Durov in Russian military channels 🤷
In any case, France taking over Telegram infrastructure is still highly speculative - the main point of the arrest is almost complete lack of moderation in Telegram, even for the most severe CSAM (child abuse) content.
While in Russia arrest of Durov would likely lead to his genitals being connected to a field telephone in order to convince him to hand over the infrastructure (that’s why he ran away from Russia in the first place), in #France he will be likely just subject to a regular, boring law enforcement process that ends with a trial and suspended sentence, at best, if he agrees to improve content moderation. Part of the panic in Russia is that Russian routinely project the practices of their own law enforcement onto everyone else.
Kevin Rothrock
kevinrothrock@infosec.exchangeCSAM = child sexual abuse material. Telegram implicitly allows it in private groups and direct messages. Telegram won't work with the police even if it's found on public channels. https://cyber.fsi.stanford.edu/io/news/addressing-distribution-illicit-sexual-content-minors-online
Ivan Kwiatkowski
justicerage@infosec.exchangeAccording to @AFP, @durov was arrested at a 🇫🇷 airport a few hours ago. Sources say he will most likely be jailed.
He is basically being held responsible for all the illegal activities taking place on Telegram and failing to cooperate with law enforcement to make it stop.
Key takeaway for software companies: E2EE protects you just as much as it protects users.
Durov can only be accused of not cooperating insofar as he technically could, if he wanted to.
Like it or don't, this could never happen with Signal.