Posts
3150Following
707Followers
1555"No way to prevent this" say users of only language where this regularly happens
https://xeiaso.net/shitposts/no-way-to-prevent-this/CVE-2024-5535/
Trend Zero Day Initiative
thezdi@infosec.exchangeDuring #Pwn2Own Automotive, the team from @Synacktiv used 2 bugs to take over the #Autel Maxicharger. Our latest blog takes a brief look at how they did it, and how Autel patched it.
https://www.zerodayinitiative.com/blog/2024/8/22/from-pwn2own-automotive-taking-over-the-autel-maxicharger
Hrafn
hth@androiddev.socialSo Gartner is full of shit?
Color me not surprised.
Gartner does not do rigorous research. It is an MBA gospel cargo cult consultancy. They shouldn't be taken seriously.
https://www.economist.com/finance-and-economics/2024/08/19/artificial-intelligence-is-losing-hype
screaminggoat
screaminggoat@infosec.exchangeSolarWinds security advisory: Web Help Desk Hardcoded Credential Vulnerability (CVE-2024-28987)
Here we go again, another SolarWinds Web Help Desk vulnerability. I promise you this one is different:
CVE-2024-28987 (9.1 critical) The SolarWinds Web Help Desk (WHD) software is affected by a hardcoded credential vulnerability, allowing remote unauthenticated user to access internal functionality and modify data.
No mention of exploitation. Discovered by Zach Hanley, while not listed, is part of Horizon3. He indicated at the Bad Place that he will post a technical writeup next month. Stay tuned.
#SolarWinds #vulnerability #CVE_2024_28987 #cve #webhelpdesk
Thorsten Leemhuis (acct. 1/4)
kernellogger@fosstodon.orgI'd really like to read a well researched article that sums up how Linux distros reacted to the massive influx of #Linux #kernel CVE that started ~half a year – both for their #LinuxKernel packages and their live-patching offerings.
But I guess that is an enormous amount of work that no media outlet in this world is willing to pay anyone for writing. 😕
Slide taken from @gregkh's "Why are there so many kernel CVEs?" talk he gave at OSS China yesterday (https://social.kernel.org/objects/c9979d9f-399f-428b-ac56-c41598076dfa ) #LinuxKernel
lander
landaire@bird.makeupI wrote a blog post on my adventures in writing a PE loader for the Xbox One exploit chain by @carrot_c4k3
There's not really anything new and this post was mostly an excuse to document how I fixed thread-local storage, but you might learn something!
Javier Partido Rufo
javierprtd@bird.makeupI just released the blog explaining how I leveraged CVE-2022-22265 in the Samsung npu driver. Double free to achieve UAF over signalfd + cross cache + Dirty Page Table + code inject into http://libbase.so for execution by init. Hope you can enjoy it https://soez.github.io/posts/CVE-2022-22265-Samsung-npu-driver/
VictorV
vv474172261@bird.makeuphttps://v-v.space/2024/08/19/CVE-2024-38148/
Check my blog about Windows secure channel RCE analysis, though MSRC thought it's a DOS. By the way, I'm not the finder. Share for studying
vuln research is the act of downloading trials and encountering errors while installing them
Lin Tan
lin0tan@bird.makeupIntroducing ReSym (CCS'24): our binary analysis technique, an LLM+static analysis solution that recovers names, types, and layouts of variables and data structures from binaries https://tinyurl.com/resym24 @danning_x, @i2huer, @nanjiang719, @xiangzhex XiangyuZhang #LLM4code #CCS #LLM
Alex Plaskett
alexjplaskett@bird.makeupexploit developers reading yet another RFC to see how IPv6 option processing works
DEF CON
defcon@defcon.socialThe #defcon 32 Video Team videos are now up on https://media.defcon.org Enjoy!
Phrack
phrack@haunted.computerWe are planning a new issue (and hard copy) to celebrate Phrack's 40th anniversary next year, please check out http://phrack.org for more info on contributing!
screaminggoat
screaminggoat@infosec.exchangeGoogle Chrome Zero Day: Stable Channel Update for Desktop
This update includes 38 security fixes. (20 externally reported). CVE-2024-7971 (high severity) Type confusion in V8
Reported by Microsoft Threat Intelligence Center (MSTIC), Microsoft Security Response Center (MSRC) on 2024-08-19
Google is aware that an exploit for CVE-2024-7971 exists in the wild.
cc: @campuscodi @briankrebs @mttaggart @deepthoughts10 @cR0w @regnil @bschwifty @arinc629 @Cali @wvu @hrbrmstr @avoidthehack @bieberium @AAKL (make sure to remove all the mentions to avoid ReplyAll madness)
#Google #Chrome #zeroday #vulnerability #eitw #activeexploitation #CVE #CVE_2024_7971
charles aylward
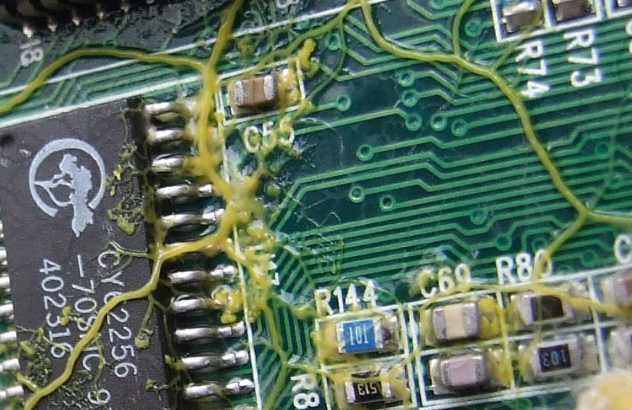
cda@malt.socialPhysarum wires: Self-growing self-repairing smart wires made from slime mould: https://arxiv.org/abs/1309.3583 a.k.a. super super gross wires. This is for sure how you end up with the backstory for the Borg.
Mr. Bitterness
wdormann@infosec.exchangeAside from those unfortunate souls who have a dual-boot system that both wasn't detected by Microsoft and also is out of date enough so that its boot bits are noncompliant, who else might be affected by this?
Ventoy will fail to work on a SecureBoot-enabled Windows system with August's updates. The current Ventoy doesn't have a "shim,4" compliant EFI bootloader.
You can fix this if you don't care to wait for Ventoy to fix this.
Or do what probably a lot of people do, which is disable SecureBoot and forget to ever turn it back on again.
https://github.com/ventoy/Ventoy/issues/2692#issuecomment-2031412234
Stefan Bohacek
stefan@stefanbohacek.onlineThis won't likely surprise anyone, but "a prompt injection vulnerability in Slack AI makes it possible to fetch data from private Slack channels".
https://www.theregister.com/2024/08/21/slack_ai_prompt_injection/