Posts
3473Following
717Followers
1584GrapheneOS
GrapheneOS@grapheneos.socialGrapheneOS has publicly posted about the carrier apps included on Pixels and their privileged permissions on numerous occasions. We talked about the ones which get enabled automatically based on using a SIM from a carrier rather than a disabled demo without an automatic trigger.
Trammell Hudson
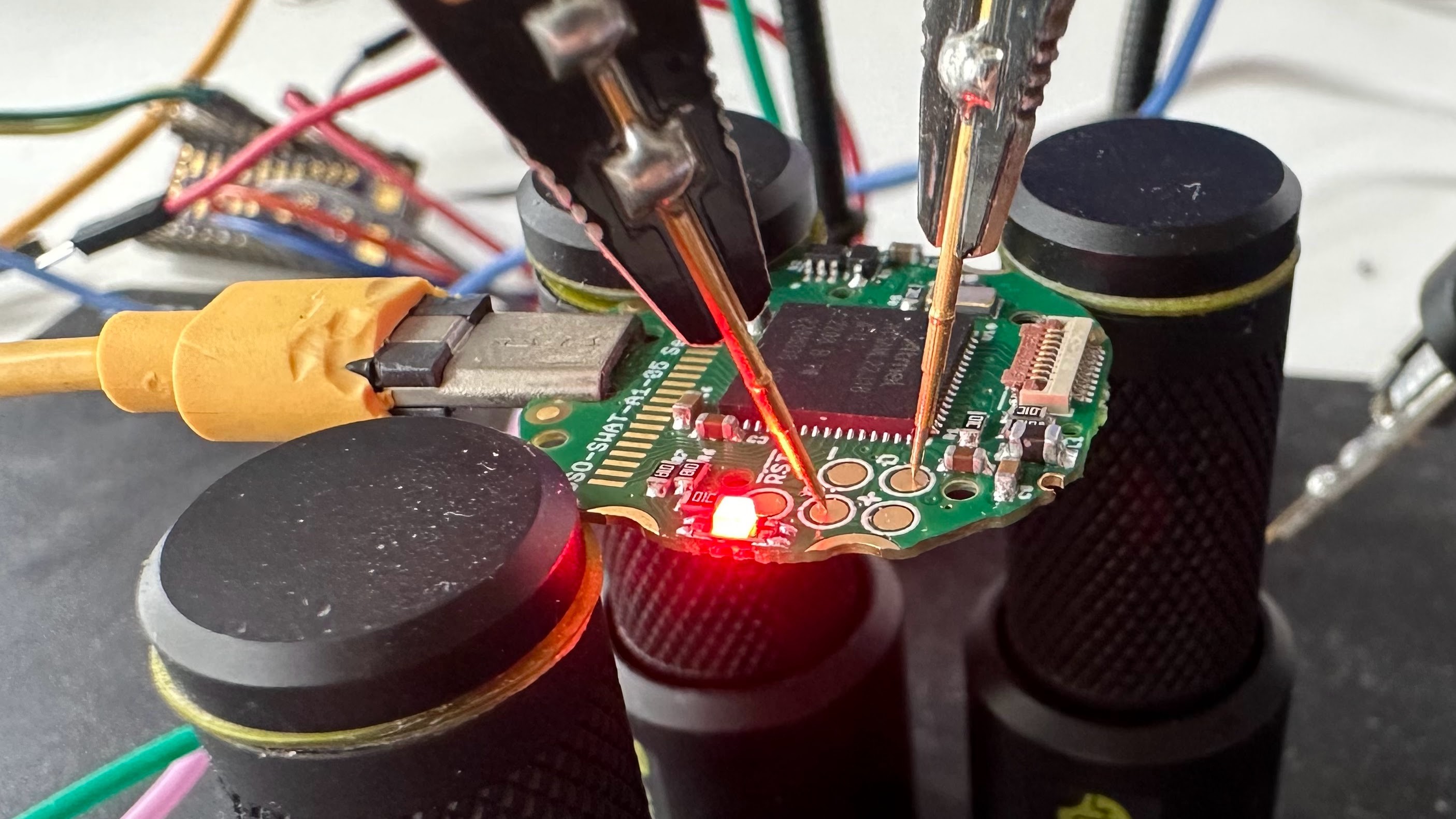
th@v.stFor #CircuitPythonDay2024 I'm porting Micropython to the SensorWatch SAML22J18 that fits in the classic Casio FT-91W. https://www.sensorwatch.net/
It's the Freya's day today so let's run another #nakeddiefriday why don't we.
Today I got a #French classic form 1983, one of the very first chip cards. The micromodule is a very characteristic shape of those designed by Bull.
On the die itself, the EEPROM array is in the very center, with the address counter to the right, drivers above and the data multiplexer below.
Note the designer initials, C.B. and Y.G.
Hi-res: https://siliconpr0n.org/archive/doku.php?id=infosecdj:bull:et1001
Linuxiac
linuxiac@mastodon.socialClamAV Antivirus 1.4 ends 32-bit Linux support, introduces ARM64 packages for Windows, improves ALZ and LHA archive handling, and more.
https://linuxiac.com/clamav-antivirus-1-4-ends-32-bit-linux-support/
CERT-EU
cert_eu@infosec.exchangeZabbix Server Critical Arbitrary Code Execution Vulnerability (CERT-EU Security Advisory 2024-082)
On August 13, 2024, a critical vulnerability, CVE-2024-22116, was disclosed in Zabbix Server, allowing attackers with restricted administrative permissions to execute arbitrary code. The flaw, identified in the Ping script execution within the Monitoring Hosts section, can compromise the entire infrastructure. The vulnerability carries a CVSS score of 9.9.
https://www.cert.europa.eu/publications/security-advisories/2024-082/
Hacker News
hkrn@mstdn.socialCartoon Network's Website Was Deleted. That Should Scare You All
L: https://slate.com/technology/2024/08/david-zaslav-warner-bros-discovery-culture-deleting-movies-tv-shows.html
C: https://news.ycombinator.com/item?id=41262878
posted on 2024.08.15 at 23:25:16 (c=0, p=5)
Elizabeth K. Joseph
pleia2@floss.social@mainframed767 @fennix IBM Z Xplore is also nice because it exposes you to a bunch of different concepts and areas of basic mainframe tech, so if something sparks your interest you can then seek out specific training for those components, some of which are also free
stacksmashing
stacksmashing@infosec.exchangeWhen I got started with hardware hacking etc @travisgoodspeed was (and is) one of my heroes.
Now there’s a chapter in his new (awesome) book on a vuln I found. Feels awesome.
Thanks Travis for all your contributions to our community.
Also, you should buy his book!
kaoudis
kaoudis@infosec.exchangehttps://www.usenix.org/conference/usenixsecurity24/presentation/cao-leo I am excited about anything that wants to make OAuth less terrible, and this not only seems to do that but has a nice clear threat model!
kaoudis
kaoudis@infosec.exchangehttps://www.usenix.org/conference/usenixsecurity24/presentation/schilling this looks like if viable for real world use, something that could make binary-only target thread sanitization checks possible. I love how accessible sanitizers are; they’re the gateway drug of llvm instrumentation. I am also looking forward to reading this~
kaoudis
kaoudis@infosec.exchangehttps://www.usenix.org/conference/usenixsecurity24/presentation/feng-siyue taint analysis across traces to see how well patches did at fixing vulns, but with a fancy Bloom filter to see if a particular code path has been hit before (I look forward to reading this)
kaoudis
kaoudis@infosec.exchangehttps://www.usenix.org/conference/usenixsecurity24/presentation/bulekov this hypervisor emulation and fuzzing tool also looks really interesting and I’m looking forward to trying it out
kaoudis
kaoudis@infosec.exchangehttps://www.usenix.org/conference/usenixsecurity24/presentation/qi System-level emulation and instrumentation is generally slow, but there’s a neat insight into when instrumentation *isn’t* necessary and what basic blocks to not instrument for QEMU-based system-level concolic execution in this work!
kaoudis
kaoudis@infosec.exchangehttps://www.usenix.org/conference/usenixsecurity24/presentation/schl%C3%BCter the threat model (not the written out one in the paper, which is seemingly to me at least somewhat disjoint from what I understand from what I am hearing) that underlies this work is interesting; it points out that blindly trusting the hypervisor as part of trusting the cloud provider may not be in the best interest of operators of a VM (or a confidential VM using a TEE)
Guy Dupont
gvy_dvpont@mastodon.socialTired of using your own tongue to test 9V batteries???
👅👅👅🔋🔋🔋 ouch!
Honored and humbled to announce my latest product:
/r/netsec
_r_netsec@infosec.exchangeMSI motherboards susceptible to code execution & firmware implant - analysis of CVE-2024-36877 https://jjensn.com/at-home-in-your-firmware
Enjoy the old sch00l lulz:
Fuck You Ilfak - A IDA Pro 9.0 Beta 2 macOS x86 Fix Loader
TrendAI Zero Day Initiative
thezdi@infosec.exchangeMicrosoft fixed CVE-2024-38213 last Tuesday. It was discovered in the wild by ZDI threat hunter @gothburz. Today, he makes the details of the vulnerability and how it's being used by threat actors. https://www.zerodayinitiative.com/blog/2024/8/14/cve-2024-38213-copy2pwn-exploit-evades-windows-web-protections
Trail of Bits
trailofbits@infosec.exchangeTwo days ago, NIST finalized three post-quantum cryptography standards. Today, we are announcing an open-source Rust implementation of one of these standards, SLH-DSA, now available in RustCrypto! https://blog.trailofbits.com/2024/08/15/we-wrote-the-code-and-the-code-won/
screaminggoat
screaminggoat@infosec.exchangeCISA: CISA Adds One Known Exploited Vulnerability to Catalog
Hot off the press! CISA adds CVE-2024-28986 (9.8 critical, disclosed 13 August 2024 by SolarWinds) SolarWinds Web Help Desk Java Deserialization Remote Code Execution Vulnerability to the Known Exploited Vulnerabilities Catalog.
Note: There was no indication that CVE-2024-28986 was being exploited in the wild in the security advisory.
cc: @campuscodi h/t: @hrbrmstr
#CVE_2024_28986 #SolarWinds #vulnerability #eitw #activeexploitation #cisa #kev #KnownExploitedVulnerabilitiesCatalog