Posts
2704Following
681Followers
1504hrbrmstr 🇺🇦 🇬🇱 🇨🇦 🏳️🌈
hrbrmstr@mastodon.socialThe sheer volume of CrowdStrike-esque domains being registered and weaponized today is…staggering.
Michael Kleber
Log3overLog2@mathstodon.xyz@LukaszOlejnik This paper seems to be fundamentally flawed — their simulator failed to properly use an RNG, so it simulated giving people the same topics on every site. See https://github.com/yohhaan/topics_api_analysis/issues/1
This points out how great it is for published papers to post their code and data set on GitHub! It means that we can actually point to the bug in their simulator, offer the one-line fix, and immediately re-run the corrected analysis using the author's own fixed code.
Jonathan Müller
foonathan@fosstodon.orgGraham Sutherland / Polynomial
gsuberland@chaos.social@thephd there's a main kernel driver and a bunch of .sys files that contain update data. the main kernel driver parses those .sys data files. one of those data files has incorrect data in it, which causes the parser (written in C) in the main driver to crash. from what I've seen of the analysis (early days) it looks like bad pointer maths from invalid data, leading to either UAF or OOB memory access.
/r/netsec
_r_netsec@infosec.exchangeExploiting An Enterprise Backup Driver For Privilege Escalation - CVE-2023-43896 https://northwave-cybersecurity.com/exploiting-enterprise-backup-software-for-privilege-escalation-part-two
Scarlet
scarlet@chaos.socialjust ran into an incredible bug: portal 2 crashes if you happen to have a CPU with 128 threads
buttplug.io 🍑🔌
buttplugio@buttplug.zoneDear buttplug.io users:
We apologize for the current downtime.
If your butt is BSOD’ing, please try rebooting it a few times.
Kenn White
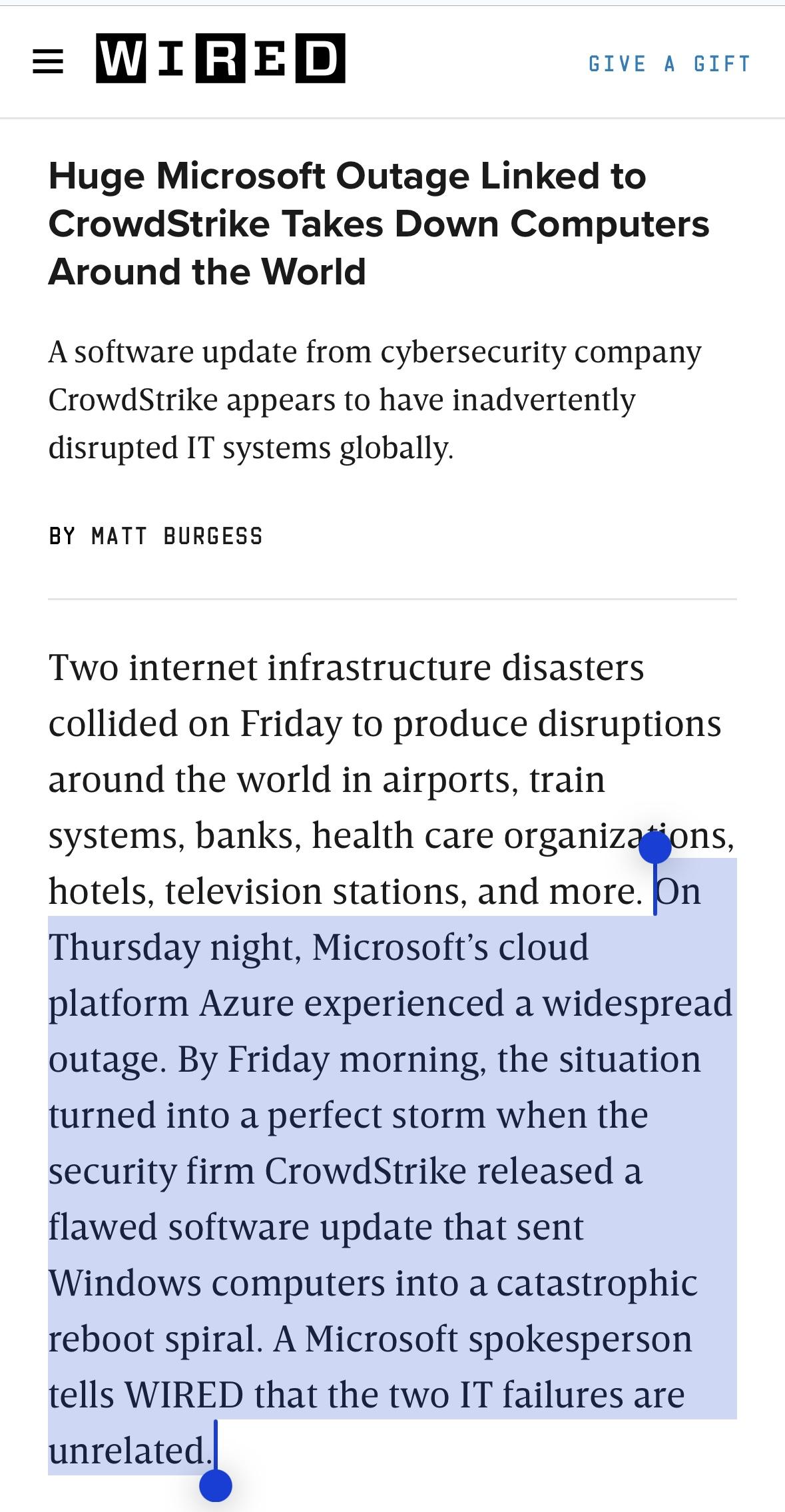
kennwhite@mastodon.socialJust reiterating, because this is getting lost in a lot of the coverage: the original Azure outage and the Crowdstrike Windows bug are NOT related. That said, a significant number of corps run Windows servers on Azure with Crowdstrike Falcon. Wired coverage has more.
https://www.wired.com/story/crowdstrike-outage-update-windows/
Haifei Li
haifeili@bird.makeupSo I just happened to read a blog discussing some PoC crashes in Office (https://code610.blogspot.com/2017/10/microsoft-outlook-2016-rwra-crash.html) & what I do? I sent them to @expmon_ immediately (https://pub.expmon.com/analysis/110243/).
ht: I've found real exploitable bugs w/ the power of EXPMON, it's not just a 0day detection system.:)
Graham Sutherland / Polynomial
gsuberland@chaos.socialpour one out for the homies who can't head to the pub tonight because they're stuck unfucking hundreds of computers
❄️☃️Merry Jerry🎄🌲
jerry@infosec.exchangeHere is a GPO that can apparently run in safe mode to automate the removal of the problematic crowdstrike driver: https://gist.github.com/whichbuffer/7830c73711589dcf9e7a5217797ca617
EDIT: despite my indication that this for running in safe mode, many people seemed to have missed that I said it is for safe mode. So, here is the clarification: IT IS FOR SAFE MODE
H/T @p4gs
@cynicalsecurity Except if made by a certain RU company, where perfect uptime is required to maximize exfil and stealthiness, and minimize chance of detection if it breaks :X
cynicalsecurity 
cynicalsecurity@bsd.network
When I said "one day my stance on EDR / AV / IPS will be vindicated" I didn't mean for half the Internet to melt down but I am soooooo enjoying this moment.
Thank you #Crowdstrike for giving me my day of glory. Now I will have a story to tell my grandchildren.
Rairii (bootloader unlocked, MSR_LE set)
Rairii@social.nano.lgbtso I happen to have a 0day downgrade attack bitlocker bypass, which would be very helpful for people dealing with the crowdstrike issue and have more than about a dozen systems with tpm+secure boot bitlocker lol
the downgrade attack part is why i never publicly documented the original issue yet
also I bet MS are very annoyed that everyone’s saying its their fault
stacksmashing
stacksmashing@infosec.exchangeExplaining to reporters that this is not a Microsoft issue but a Crowdstrike issue - interesting how different the "non tech" world looks at this
pfm 🧘 
pfm@edolas.world
I recall reading a "computer horror story", most probably around 2005-2010 but dated earlier, maybe much earlier, that involved a computer room with floor tiles and a short circuit, probably below those tiles. The story described the long process of investigating the issue and I was thrilled to read it.
It was comparable to the Unix recovery legend and to VAXen, my children, just don't belong in some places.
Please boost and if you know that story or anything that sounds at least close to it -- please share! If you help me find the one I'm looking for, you'll be my hero for at least a week!
Attacker Friction
attackerfriction@infosec.exchangeEDR bug crashes all your points of access.
Vendor investigation and Incident Response processes are started, risking the exposure of your operation.