Posts
2473Following
662Followers
1487Trail of Bits
trailofbits@infosec.exchangeIntroducing Decree by @trailofbits: A new tool that helps devs define, enforce, and understand their Fiat-Shamir transcripts. Check it out!
https://buff.ly/3KUnALC
robbje
robbje@infosec.exchangeWhen building a x86 lifter, the first 1000 instructions are the hardest. After that all that's left is another 1000 or so SSE instructions.
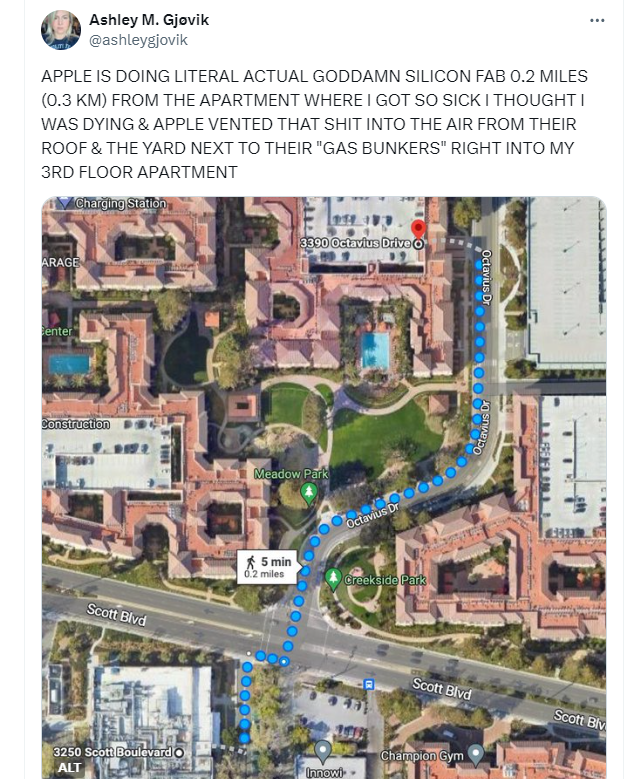
Ashley M. Gjøvik, JD
ashleygjovik@mastodon.social🧵 In 2020, I nearly died from mysterious industrial chemical exposure at my apartment. Later, in 2023, I discovered my employer was dumping toxic waste into the apartment windows from their Skunkworks semiconductor fab next-door. I tipped off the US EPA, who sent their env cops to raid Apple's plant in Aug of 2023. The US EPA finally released the report of their enforcement inspections & sent me a copy on Friday. 💀 ⬇️
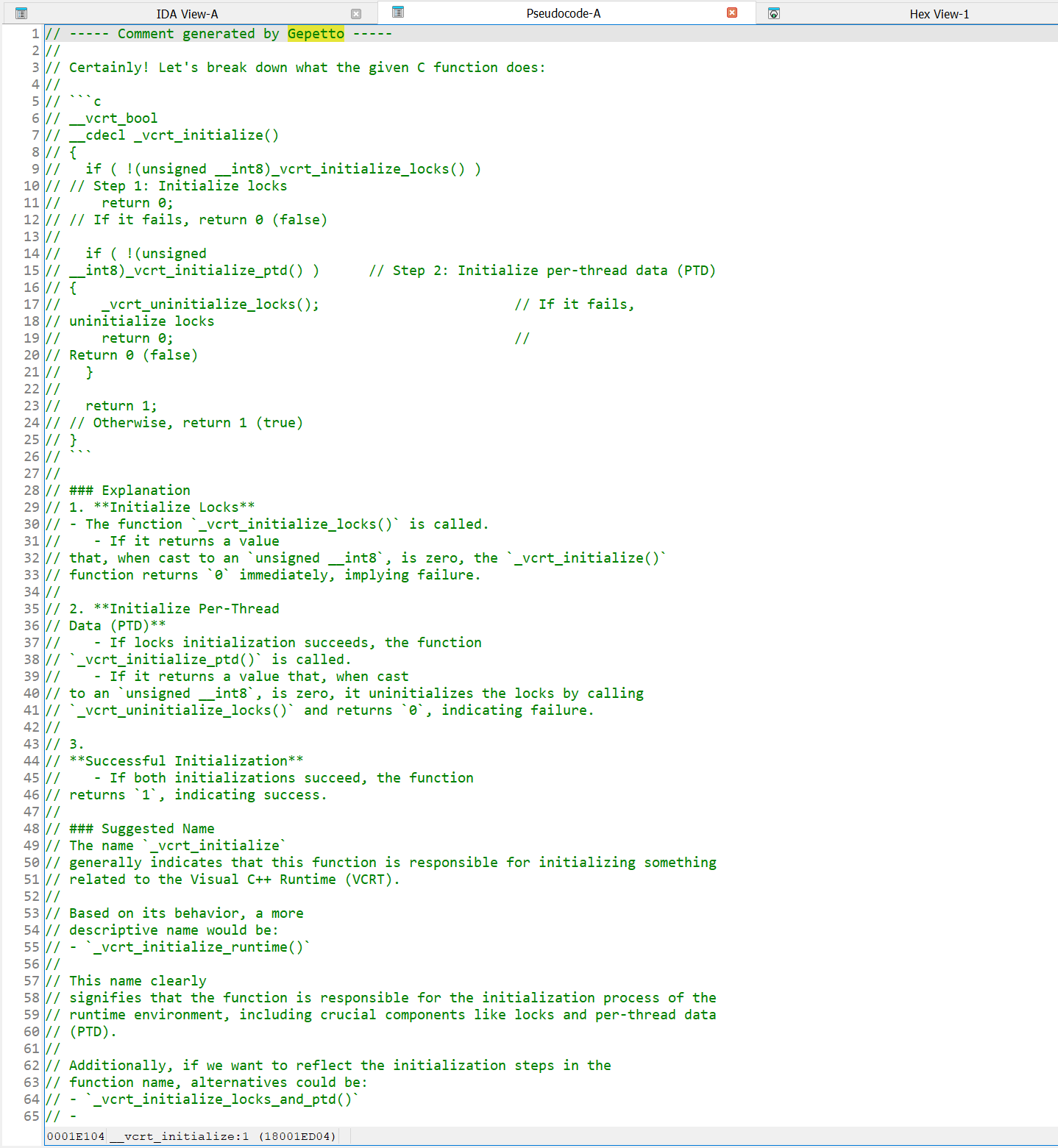
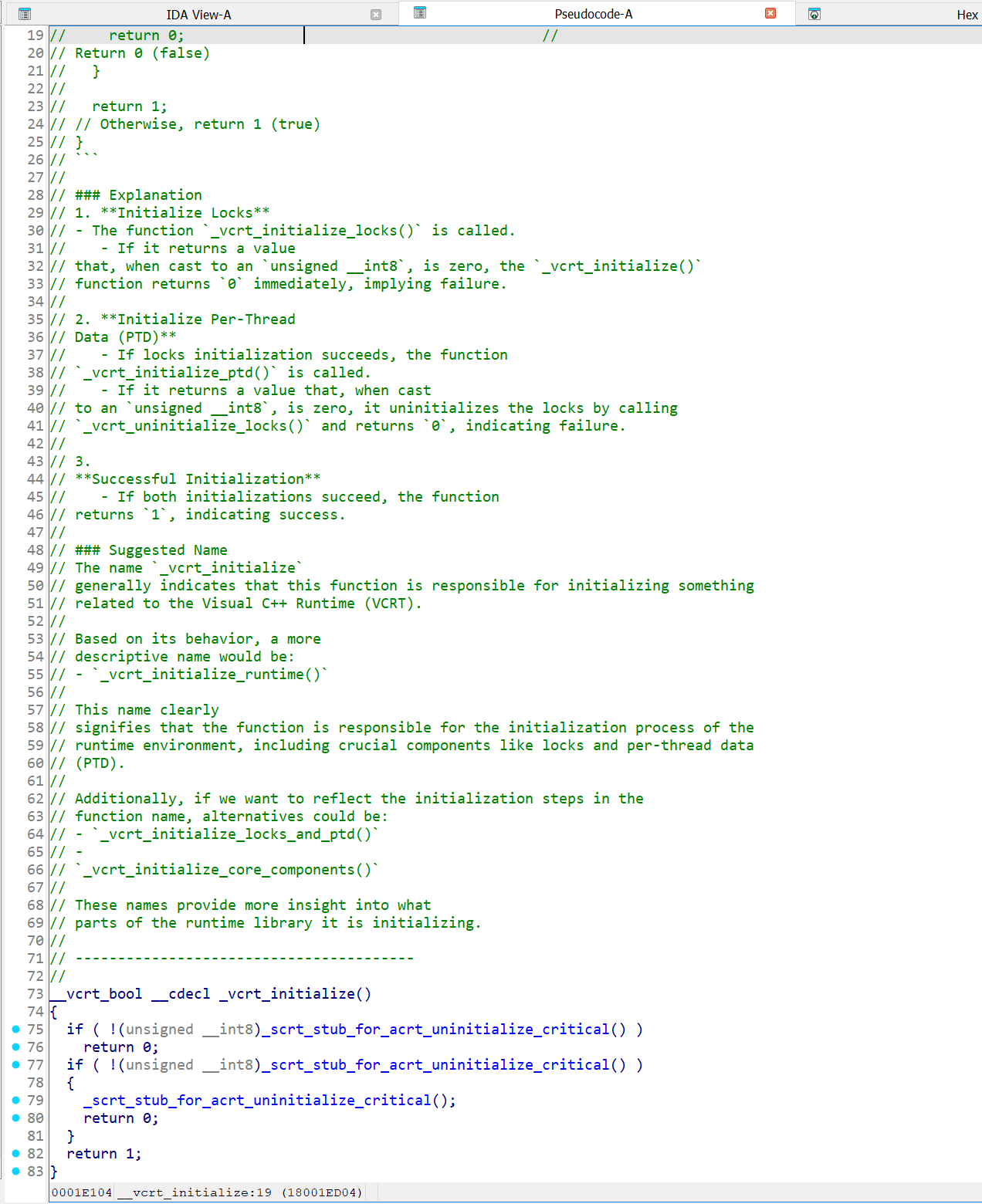
Joxean Koret (@matalaz)
joxean@mastodon.socialSo, summary:
* There was no need to explain a well known MSVC runtime function that is 14 assembly instructions long and only calls a single function.
* The model wrote a 72 lines bullshit explanation for a 14 assembly lines long function.
* The model hallucinated a different function and explained what it hallucinated.
* Someone just polluted IDA's Lumina Server with bullshit AI shit.
Joxean Koret (@matalaz)
joxean@mastodon.socialI have just discovered that a function's comment added to a MSVC well known runtime function added by IDA's Lumina Server was generated using an AI tool for IDA.
Please don't. I fucking hate it.
BTW: The code for the function that the LLM model is trying to explain *is hallucinated* and does not even correspond to the real function.
Tube Time
tubetime@mastodon.socialfun fact: the landing zone on a hard disk platter has a special surface texture that reduces stiction. the rest of the surface is so smooth the head would get stuck if it landed on it.
Attack & Defense (Old Account)
attackanddefense@mozilla.socialAs of today, Firefox Nightly ships with "HTTPS First". So, all new tabs, all links will try HTTPS🔒 regardless of the written URL scheme. When HTTPS fails, Firefox will fall back to using http.
This is thanks to the tireless work of our intern @mjurgens 👏👏👏.
lcamtuf 


lcamtuf@infosec.exchange
Random objects: Intel Edison, or a look at the misadventures of x86 in the IoT space - https://lcamtuf.substack.com/p/random-objects-intel-edison
Nick Selby 
fuzztech@infosec.exchange
If you are still doing this to your customers, you're not understanding what has happened in the world of technology since 2004 and you are part of the problem.
Jan Wildeboer 😷
jwildeboer@social.wildeboer.net
The wonderful world of #OpenSource and #Mastodon! https://tech.lgbt/@nina_kali_nina/112659983582469484 where Nina asks a question, I answer with a partial solution based on a little project by @vadim which is missing a specific feature. Vadim sits down, codes that missing feature, commits it, I pull his updates, build a new container and now we all have an even better way to turn Mastodon threads into copy/pasteable #Markdown.
That all happened in less than 5 hours!
Nahum Shalman
nahumshalman@hachyderm.ioI have rebased the #illumos / #solaris port of #Tailscale onto 1.68.1
https://github.com/nshalman/tailscale/releases/tag/v1.68.1-sunos
Thom, 🧨
thomholwerda@exquisite.socialAnd here's my occasional Fedi outreach about my dream retrocomputer - does anyone have a Sun Ultra 45 they are willing to part with? I'm just a sad, pathetic person living in Arctic Sweden who has been trying for more than two decades (!!) to get his hands on one.
Boosts are definitely love.
lcamtuf 


lcamtuf@infosec.exchange
Frankly, I'm appalled by the prospect of LLMs taking offensive security research jobs from honest, hard-working fuzzers
Alex Plaskett
alexjplaskett@bird.makeup✍️ When Samsung Meets Mediatek - The story of a small bug chain by @max_r_b @pwissenlit Raphaël Neveu
screaminggoat
screaminggoat@infosec.exchangeRobel Campbell of Blackpoint Cyber performed patch diffing and root cause analysis on the Microsoft Outlook Remote Code Execution Vulnerability CVE-2024-30103 (see parent toot for links) and stated the following:
- It requires valid credentials of the target user to exploit. This is important to know because there is a lot of posting calling this a 'zero-click' exploit and while it might be true to an extent, you still need to be able to create a Form in the target users Outlook client, which requires authorization.
- It's a bypass for a previously patched vulnerability (CVE-2024-21378)
- Indicators of exploitation may include a suspicious DLL loaded in the Outlook.exe process, suspicious outbound connections from Outlook.exe and spawned child processes.
- Exploitation is less likely at a large scale given that an attacker would need a user's credentials to set the attack up. Applying the latest patches is the best way to defend against this exploit.
View the original message at the bad site: https://twitter.com/RobelCampbell/status/1804171069558755624 cc: @GossiTheDog
#CVE_2024_30103 #CVE_2024_21378 #Outlook #vulnerability #CVE #Microsoft
Rairii (bootloader unlocked, MSR_LE set)
Rairii@social.nano.lgbtso with the recent news i’ll ask again
does anybody have a uefi firmware image that includes kaspersky antivirus for uefi?
Urda
urda@urda.social“For this you keep a lab notebook. Everything gets written down, formally, so that you know at all times where you are, where you've been, where you're going and where you want to get. In scientific work and electronics technology this is necessary because otherwise the problems get so complex you get lost in them and confused and forget what you know and what you don't know and have to give up.”
- Robert Pirsig, Zen and the Art of Motorcycle Maintenance
Lorenzo Franceschi-Bicchierai
lorenzofb@infosec.exchangeNEW: The U.S. government has sanctioned 12 executives and senior leaders of Russian cybersecurity giant Kaspersky.
Notably, Eugene Kaspersky and company itself are not on the sanctions list.
These sanctions come a day after the U.S. government banned the sale of Kaspersky software in the United States.
https://techcrunch.com/2024/06/21/u-s-government-sanctions-kaspersky-executives/