Posts
3037Following
703Followers
1550TROOPERS Conference
WEareTROOPERS@infosec.exchange📢 Next week is #TROOPERS24 week! We will celebrate 15 years of making the world a safer place and are looking forward to all of you. See you in #Heidelberg. 🥳
Jason Scott
textfiles@mastodon.archive.orgA few years ago, a kid mourning his dad handed me over 300 DVDs his dad had made of local bands in his London Suburb in the 2010s before passing on. He didn't know what do with them. I did. All of them are up at Internet Archive, hundreds of hours of cover bands playing in a bar, and now, thanks to a volunteer, Ducky, we have them all with dates and descriptions, where known. Enjoy.
Binary Ninja
binaryninja@infosec.exchangeOur Program Analysis for Vulnerability Research class is filling up, if you were planning on attending Recon in a few weeks and were hoping to grab one of the last seats, you move quickly!
https://recon.cx/2024/trainingprogramanalysisforvulnerabilityresearch.html
Trail of Bits
trailofbits@infosec.exchangeFuzzing can do more than find memory corruption vulnerabilities. With the right invariants, it can catch runtime errors and logical issues, as demonstrated by our custom testing harness for Fuel Labs. https://blog.trailofbits.com/2024/06/17/finding-mispriced-opcodes-with-fuzzing/
Slashdot 
slashdot@mastodon.cloud
ASUS Releases Firmware Update for Critical Remote Authentication Bypass Affecting Seven Routers https://mobile.slashdot.org/story/24/06/17/0237229/asus-releases-firmware-update-for-critical-remote-authentication-bypass-affecting-seven-routers?utm_source=rss1.0mainlinkanon
pancake 
pancake@infosec.exchange
IBM vs LzLabs. On reverse engineering zOS / mainframe software and big corpo lawsuits https://mainframeupdate.blogspot.com/2024/06/ibm-versus-lzlabs.html
/r/netsec
_r_netsec@infosec.exchangeAbusing title reporting and tmux integration in iTerm2 for code execution (CVE-2024-38396) https://vin01.github.io/piptagole/escape-sequences/iterm2/rce/2024/06/16/iterm2-rce-window-title-tmux-integration.html
Chris Gioran 💔
chrisg@fosstodon.orgThe year is 2030.
Computers boot directly into the browser. IDEs are just a web app now, running in the GPU. No one knows why. Or how.
All programs run in 4 nested containers on top of a hypervisor abstracting over the 5 major computational clouds. The last time a branch was predicted correctly, in any CPU anywhere, was 4 years ago.
Cloud costs are withdrawn directly from your retirement fund.
Ext7 just came out, it's written in Javascript and uses AI to guess what the file may contain.
bitsavers.org
bitsavers@oldbytes.spacethe famous mariner fortran bug
https://arstechnica.com/civis/threads/mariner-1-fortran-bug.862715/
TIL this turns out to be wrong
http://spiff.rit.edu/classes/phys317/lectures/boom/fortran.txt
Frederik
fre@infosec.exchangeI've done it! After literal months of work, I've finally finished my (rather long) blog post about how AES-GCM works and how it's security guarantees can be completely broken when a nonce is reused:
It includes more than 10 interactive widgets for you to try out AES-GCM, GHASH and the nonce reuse attack right in your browser! (Powered by #RustLang and #WASM )
If you're interested in #cryptography , #math (or #maths ) or #infosec you might find it interesting.
If you do read it, I'm all ears for feedback and criticism!
Filippo Valsorda
filippo@abyssdomain.expertJust published age v1.2.0 ✨
Minor release:
• binaries built with Go 1.22.4
• plugin client API
• CLI edge case fixes
• RecipientWithLabels to make auth'd or post-quantum recipients
Very happy about the last point, it was the last hardcoded thing about scrypt recipients.
screaminggoat
screaminggoat@infosec.exchangeProof of concept for CVE-2024-26229 (7.8 high, disclosed 09 April 2024 by Microsoft) Windows CSC Service Elevation of Privilege Vulnerability is allegedly available: https://github.com/varwara/CVE-2024-26229
@hexnomad can you confirm that the CWE is actually CWE-781: Improper Address Validation in IOCTL with METHOD_NEITHER I/O Control Code?
#CVE_2024_26229 #proofofconcept #CVE #vulnerability #Microsoft #MSRC
0xor0ne
0xor0ne@infosec.exchangeExcellent guide to page cache, memory management, mmap and cgroups in Linux kernel
https://biriukov.dev/docs/page-cache/0-linux-page-cache-for-sre/
Credits @brk0v
Hacker News 100
hn100@social.lansky.nameGoogle, Cloudflare and Cisco will poison DNS to stop piracy block circumvention
Link: https://torrentfreak.com/google-cloudflare-cisco-will-poison-dns-to-stop-piracy-block-circumvention-240613/
Discussion: https://news.ycombinator.com/item?id=40693451
raptor 
raptor@infosec.exchange
#ManageEngine #ADAudit - Reverse engineering #Windows #RPC to find CVEs
raptor 
raptor@infosec.exchange
Post- #Exploiting an #F5 Big-IP: root, and now what?
https://offsec.almond.consulting/post-exploiting-f5-BIG-IP.html
Deep diving into F5 Secure Vault
https://offsec.almond.consulting/deep-diving-f5-secure-vault.html
Frederik Braun �
freddy@security.plumbingLook at that! I got a new domain name.
My latest blog post shares the story of how I got the domain name, including my nerdy teenage dreams, failed OSINT, the "Miniatur Wunderland", and my aunt!
Nina Kalinina
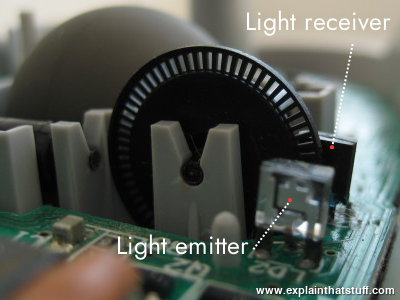
nina_kali_nina@tech.lgbtFinally, my favourite part of this computer: ball mouse. It is ingenious.
This ball mouse literally uses only two component-less round PCBs and six bent wires to convert the movement of the ball into coordinates. It has zero active components.
The ball's movement is transferred onto two bars/rods, vertical and horizontal. Each bar has a round circuit board at the end, with radial slightly bent strips of metal (see the top bar disassembled as an example) and three spring wires that touch the strips at the different distance from the center.
The linear speed of contacts on the round PCB relative to the springy contacts is different depending on the distance from the center of the round PCB, and due to the difference in the position of the contacts, we can not only infer the direction of the movement, but also the speed of the movement by counting how many "clicks" the contact has moved through in a fixed time interval.
petersuber
petersuber@fediscience.orgKudos to #Mozilla for defying #Russia's ban on #Firefox extensions that help Russian users bypass Russian #censorship.
https://www.theregister.com/2024/06/14/mozilla_firefox_russia/