Posts
2474Following
662Followers
1487bitsavers.org
bitsavers@oldbytes.spacethe famous mariner fortran bug
https://arstechnica.com/civis/threads/mariner-1-fortran-bug.862715/
TIL this turns out to be wrong
http://spiff.rit.edu/classes/phys317/lectures/boom/fortran.txt
Frederik
fre@infosec.exchangeI've done it! After literal months of work, I've finally finished my (rather long) blog post about how AES-GCM works and how it's security guarantees can be completely broken when a nonce is reused:
It includes more than 10 interactive widgets for you to try out AES-GCM, GHASH and the nonce reuse attack right in your browser! (Powered by #RustLang and #WASM )
If you're interested in #cryptography , #math (or #maths ) or #infosec you might find it interesting.
If you do read it, I'm all ears for feedback and criticism!
Filippo Valsorda
filippo@abyssdomain.expertJust published age v1.2.0 ✨
Minor release:
• binaries built with Go 1.22.4
• plugin client API
• CLI edge case fixes
• RecipientWithLabels to make auth'd or post-quantum recipients
Very happy about the last point, it was the last hardcoded thing about scrypt recipients.
screaminggoat
screaminggoat@infosec.exchangeProof of concept for CVE-2024-26229 (7.8 high, disclosed 09 April 2024 by Microsoft) Windows CSC Service Elevation of Privilege Vulnerability is allegedly available: https://github.com/varwara/CVE-2024-26229
@hexnomad can you confirm that the CWE is actually CWE-781: Improper Address Validation in IOCTL with METHOD_NEITHER I/O Control Code?
#CVE_2024_26229 #proofofconcept #CVE #vulnerability #Microsoft #MSRC
0xor0ne
0xor0ne@infosec.exchangeExcellent guide to page cache, memory management, mmap and cgroups in Linux kernel
https://biriukov.dev/docs/page-cache/0-linux-page-cache-for-sre/
Credits @brk0v
Hacker News 100
hn100@social.lansky.nameGoogle, Cloudflare and Cisco will poison DNS to stop piracy block circumvention
Link: https://torrentfreak.com/google-cloudflare-cisco-will-poison-dns-to-stop-piracy-block-circumvention-240613/
Discussion: https://news.ycombinator.com/item?id=40693451
Marco Ivaldi
raptor@infosec.exchange#ManageEngine #ADAudit - Reverse engineering #Windows #RPC to find CVEs
Marco Ivaldi
raptor@infosec.exchangePost- #Exploiting an #F5 Big-IP: root, and now what?
https://offsec.almond.consulting/post-exploiting-f5-BIG-IP.html
Deep diving into F5 Secure Vault
https://offsec.almond.consulting/deep-diving-f5-secure-vault.html
Frederik Braun �
freddy@security.plumbingLook at that! I got a new domain name.
My latest blog post shares the story of how I got the domain name, including my nerdy teenage dreams, failed OSINT, the "Miniatur Wunderland", and my aunt!
Nina Kalinina
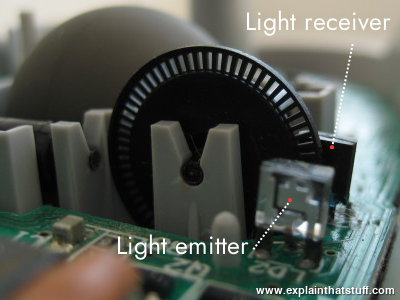
nina_kali_nina@tech.lgbtFinally, my favourite part of this computer: ball mouse. It is ingenious.
This ball mouse literally uses only two component-less round PCBs and six bent wires to convert the movement of the ball into coordinates. It has zero active components.
The ball's movement is transferred onto two bars/rods, vertical and horizontal. Each bar has a round circuit board at the end, with radial slightly bent strips of metal (see the top bar disassembled as an example) and three spring wires that touch the strips at the different distance from the center.
The linear speed of contacts on the round PCB relative to the springy contacts is different depending on the distance from the center of the round PCB, and due to the difference in the position of the contacts, we can not only infer the direction of the movement, but also the speed of the movement by counting how many "clicks" the contact has moved through in a fixed time interval.
petersuber
petersuber@fediscience.orgKudos to #Mozilla for defying #Russia's ban on #Firefox extensions that help Russian users bypass Russian #censorship.
https://www.theregister.com/2024/06/14/mozilla_firefox_russia/
Nina Kalinina
nina_kali_nina@tech.lgbt~ Let's make RAM at home, thread #1 ~
In this thread: successful experiment with factory-made ferrite core memory (1 bit for now!), a brief explanation of the experiment, and failed attempts at making a core (so you wouldn't have to try it)
🧵 go~
Nina Kalinina
nina_kali_nina@tech.lgbtI became into toy computers after I got my hands on a wonderful Sumikko Gurashi computer (and started to believe that similarly designed machines can be an answer to our cold heartless world).
I have a few vintage vTech precomputers that run BASIC and have decent IO capabilities (a serial or a parallel port at the very least), but I was curious whether newer toy computers has anything similar.
The exhibit we have here is vTech Media Desktop, a toy computer from around 2010. Its original RPP was about $100, but after a short while slashed to $25. The computer has a non-backlit ~64x48 pixel LCD, two mid-sized speakers to play high-quality digital samples and polyphonic MIDI, a membrane keyboard and a ball mouse.
There is a mini-USB port on the back that switches computer into "Sync" mode. The device presents itself as a 16MB USB stick with 512KB free, and mirrors there the contents of 512KB SPI Flash it has on board.
With the right software (which has vanished from the Internet), new apps can be added.
🧵
Mr. Bitterness
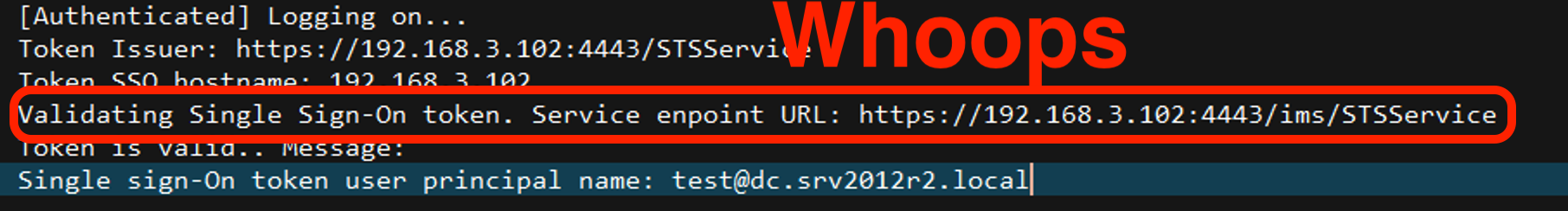
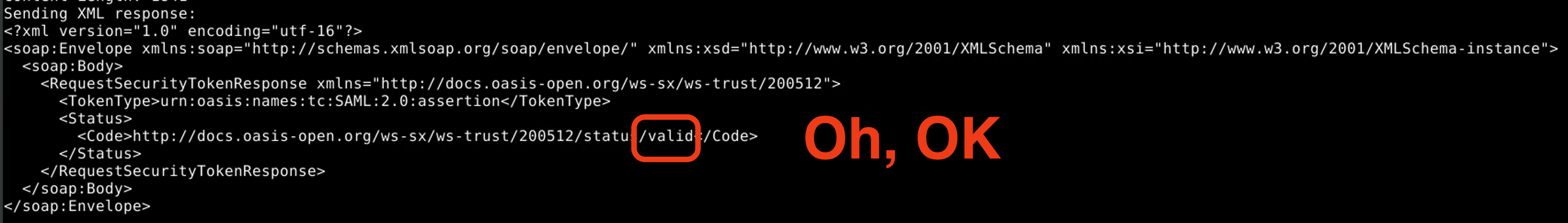
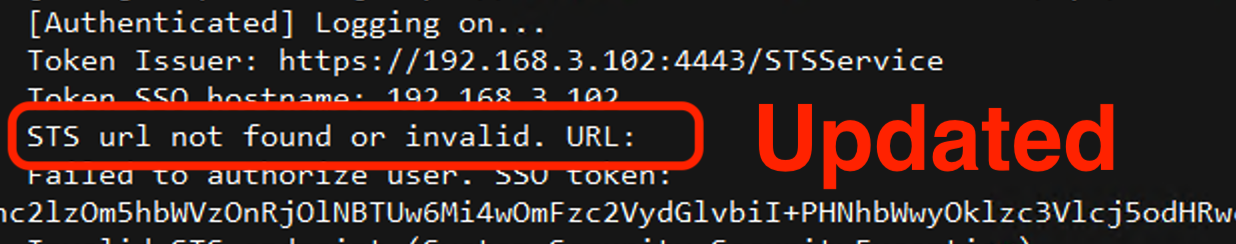
wdormann@infosec.exchangePrior to the CVE-2024-29849 update, Veeam Enterprise Manager allowed an unauthenticated API client to authenticate with the server using a client-provided Security token service (STS) endpoint to vouch for whether the client is authenticated or not.
And wouldn't you know it, the attacker-provided STS endpoint does indeed vouch that the auth request is valid.
BleepingComputer
BleepingComputer@infosec.exchangeA proof-of-concept (PoC) exploit for a critical Veeam Recovery Orchestrator authentication bypass vulnerability tracked as CVE-2024-29855 has been released, elevating the risk of being exploited in attacks.
testssl.sh 
testssl@infosec.exchange
Release of the old stable (bug-fixed only) version of testssl.sh was overdue but now happened ;-)
You can get it at https://testssl.sh/ or at https://github.com/drwetter/testssl.sh/releases .
You should better use 3.2rc3 though. It is at least as stable and has wayyy more features.
Project Gutenberg
gutenberg_org@mastodon.socialScottish physicist James Clerk Maxwell was born #OTD in 1831.
His most significant contribution is his formulation of the classical theory of electromagnetic radiation. In 1861-1862, he published a series of papers culminating in "A Dynamical Theory of the Electromagnetic Field," in which he presented Maxwell's equations. He made substantial contributions to the kinetic theory of gases as well as to the Maxwell-Boltzmann distribution
Tony Finch
fanf@mendeddrum.org2021 retro-link! https://berthub.eu/articles/posts/reed-solomon-for-programmers/ - Practical Reed-Solomon for programmers.