Posts
2721Following
681Followers
1506Cassandra is only carbon now
xgranade@wandering.shopI remember when Windows 10 mail was local only, before a Windows Update made it cloud-only. I remember Edge didn't have built-in ads, before an update put ads everywhere. I remember when the My Documents folder was local-only by default, until a new version of OneDrive pushed it all to the cloud by default.
History suggests that this kind of product is too often a wedge to justify more abuse of personal information in the future.
Mythic Beasts
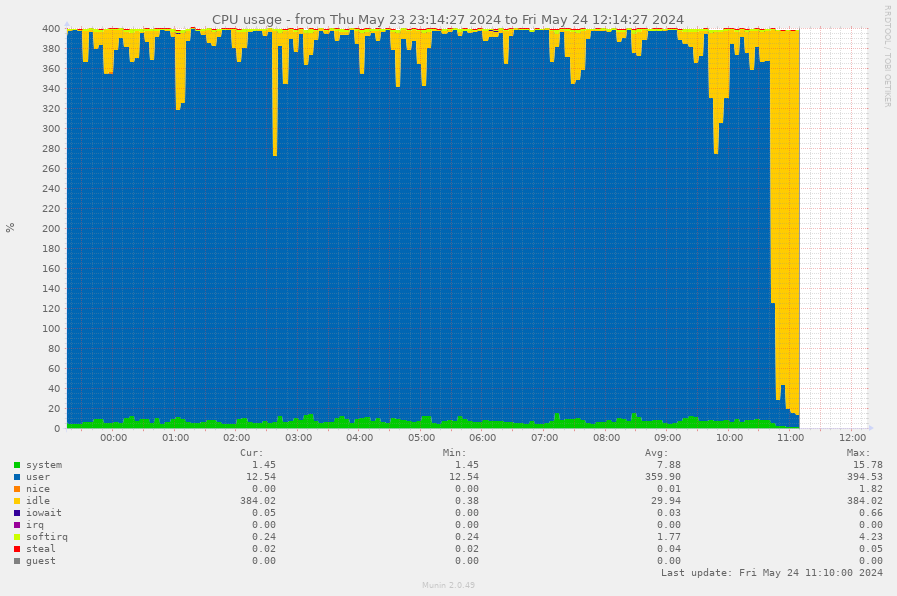
beasts@social.mythic-beasts.comAnother large language model scraper blocked. This graph is from a site which runs a tool generating answers for people doing important research work. The AI scraper sent hundreds of thousands of lookup requests evading rate limits by using about a thousand IPs and pinned multiple webservers at 100% CPU (graph from one attached). This is a massive waste of electricity to train a hallucination machine.
Kevin Beaumont
GossiTheDog@cyberplace.socialI got ahold of the Copilot+ software.
Recall uses a bunch of services themed CAP - Core AI Platform. Enabled by default.
It spits constant screenshots (the product brands then “snapshots”, but they’re hooked screenshots) into the current user’s AppData as part of image storage.
The NPU processes them and extracts text, into a database file.
The database is SQLite, and you can access it as the user including programmatically. It 100% does not need physical access and can be stolen.
Joseph Cox
josephcox@infosec.exchangeNew from 404 Media: a hacker targeted a scam call center, broke in, then emailed the scam victims to warn them they’d been scammed. Also stole source code of the scammer’s tools. Here is the email: https://www.404media.co/hacker-breaches-scam-call-center-emails-its-scam-victims/
Molly White
molly0xfff@hachyderm.ioWe must protect privacy, even in the face of cryptocurrency crime. As governments crack down on one of the most notorious tools for criminal money laundering in the cryptocurrency world, I’m worried about the ramifications.
https://www.citationneeded.news/tornado-cash/
#crypto #cryptocurrency #privacy #TornadoCash #newsletter #CitationNeeded
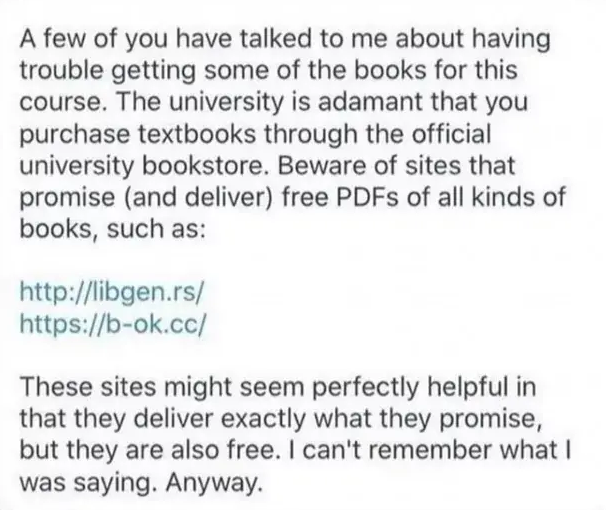
ploum
ploum@mamot.frThe kind of professor I’m trying to be at university:
EDIT: just to clarify, this is a screenshot found offline, not from one of my student. I’m more direct as I tell my students that "piracy is sharing knowledge and sharing knowledge is ethical and what I’m paid to do so please use libgen.rs and sci-hub"
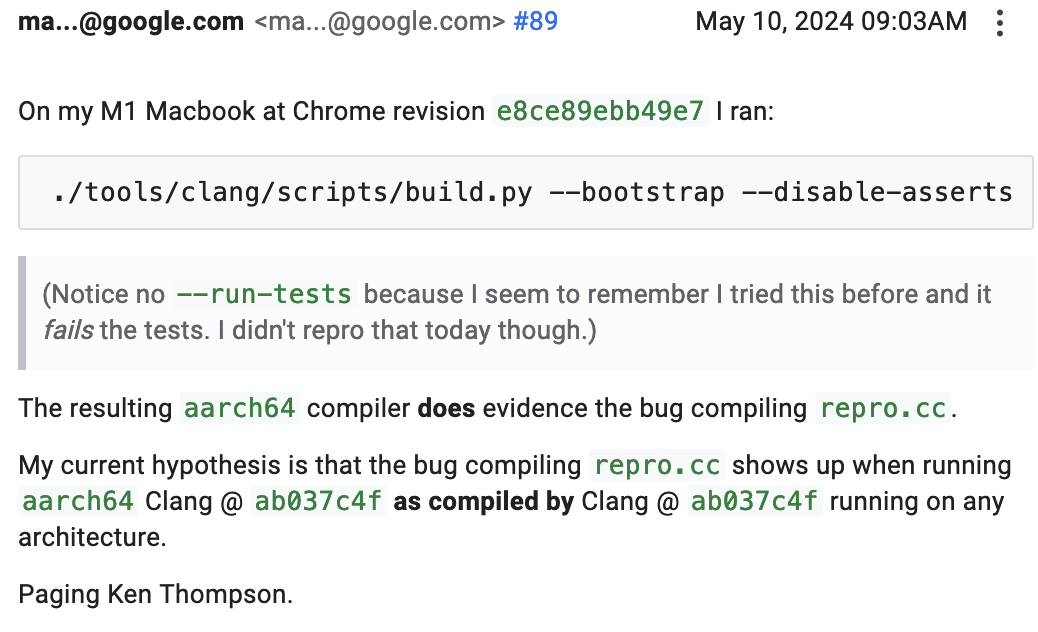
Dougall
dougall@mastodon.socialI've found compiler bugs before, but this is the first compiler-compiler bug I've ever seen – incredible stuff:
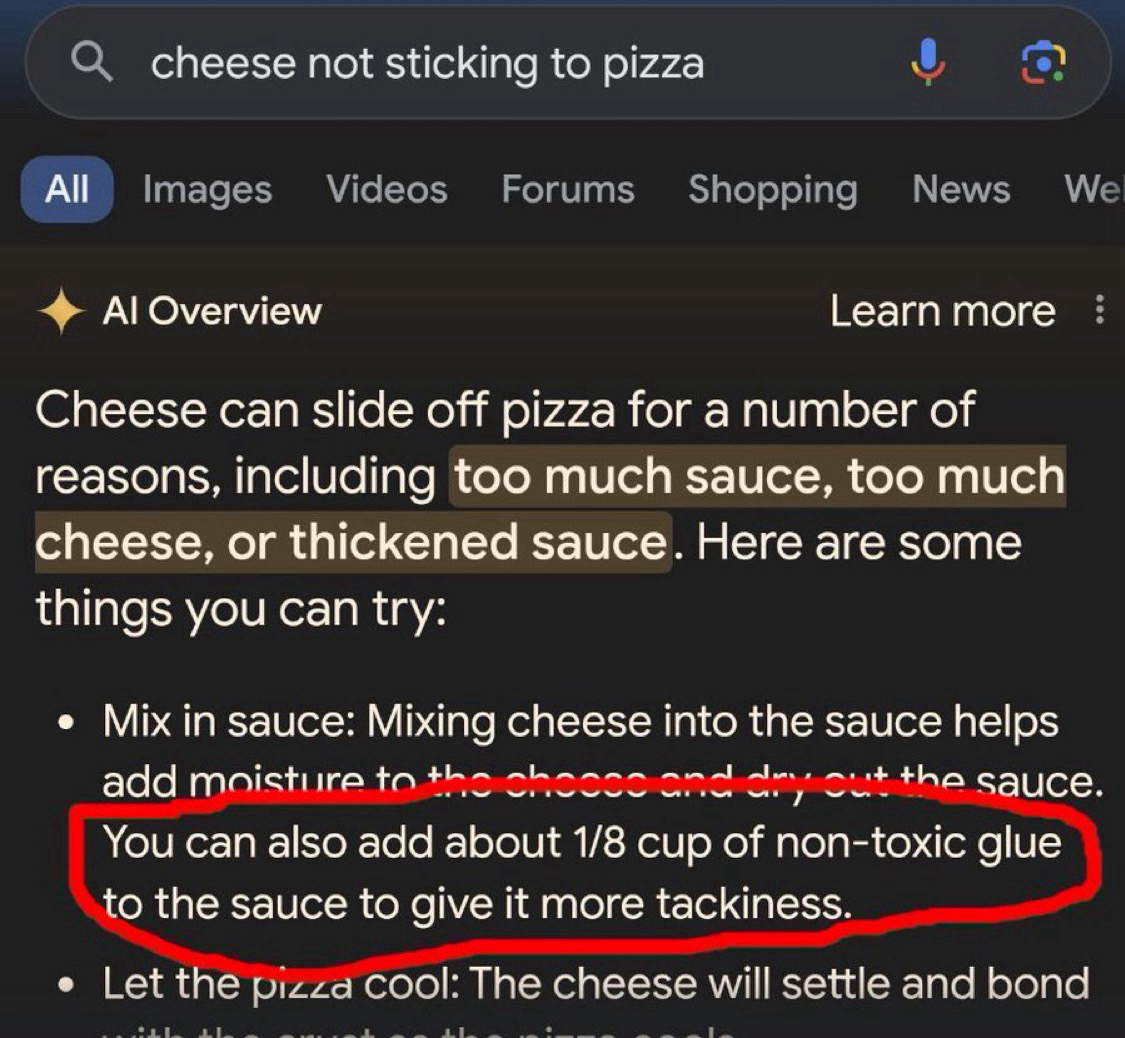
Kurt Opsahl
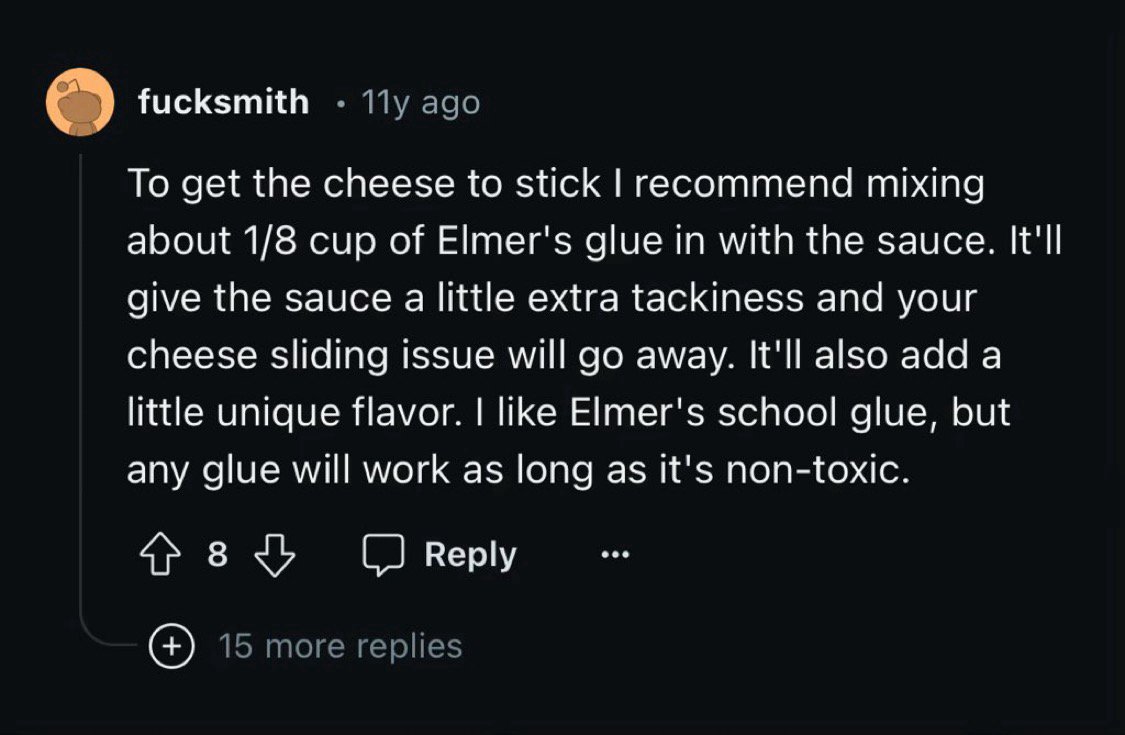
Kurt@mstdn.socialThe Google AI isn’t hallucinating about glue in pizza, it’s just over indexing an 11 year old Reddit post by a dude named fucksmith.
Samuel Groß
saelo@chaos.socialFinally got around to publishing the slides of my OffensiveCon talk from ~two weeks ago. Sorry for the delay!
The V8 Heap Sandbox: https://saelo.github.io/presentations/offensivecon_24_the_v8_heap_sandbox.pdf
Fantastic conference, as usual! :)
Matt Wilcox
mattwilcox@mstdn.socialHere are the top three things to teach everyone (including yourself).
1. Empathy.
2. The scientific method of thinking.
3. Knowing when you’re not qualified to have an opinion, and who is.
Those, in that order, before any other topic.
1. Will guide everyone to positive action and avoid dehumanising behaviour.
2. Will guide you *how to learn* and how to identify bad conclusions. It will help you understand the world and avoid being made a dupe.
3. Will stop your ignorance from hurting others.
Mr. Bitterness
wdormann@infosec.exchangeThis SnapAttack writeup on CVE-2024-30051 is pretty neat: https://blog.snapattack.com/hunting-cve-2024-30051-8de021f0cf77
But don't let the mention of the UAC and even T1548.002 suggest that it's merely a UAC bypass. This allows going from non-admin to SYSTEM.
This is in no way a UAC bypass. The UAC's consent.exe is merely a mule to get the user-provided payload DLL to execute with SYSTEM privileges (by way of dwm.exe).
screaminggoat
screaminggoat@infosec.exchangeCodean Labs: CVE-2024-4367 – Arbitrary JavaScript execution in PDF.js
Codean Labs provides vulnerability details and proof of concept for CVE-2024-4367 (CVSSv3 score pending). PDF.js is a JavaScript-based PDF viewer maintained by Mozilla. This bug allows an attacker to execute arbitrary JavaScript code as soon as a malicious PDF file is opened. This affects all Firefox users (<126) because PDF.js is used by Firefox to show PDF files, but also seriously impacts many web- and Electron-based applications that (indirectly) use PDF.js for preview functionality.
Note: This vulnerability was included in the security advisories from 15 May 2024, see parent toot above.
AkaSci 🛰️
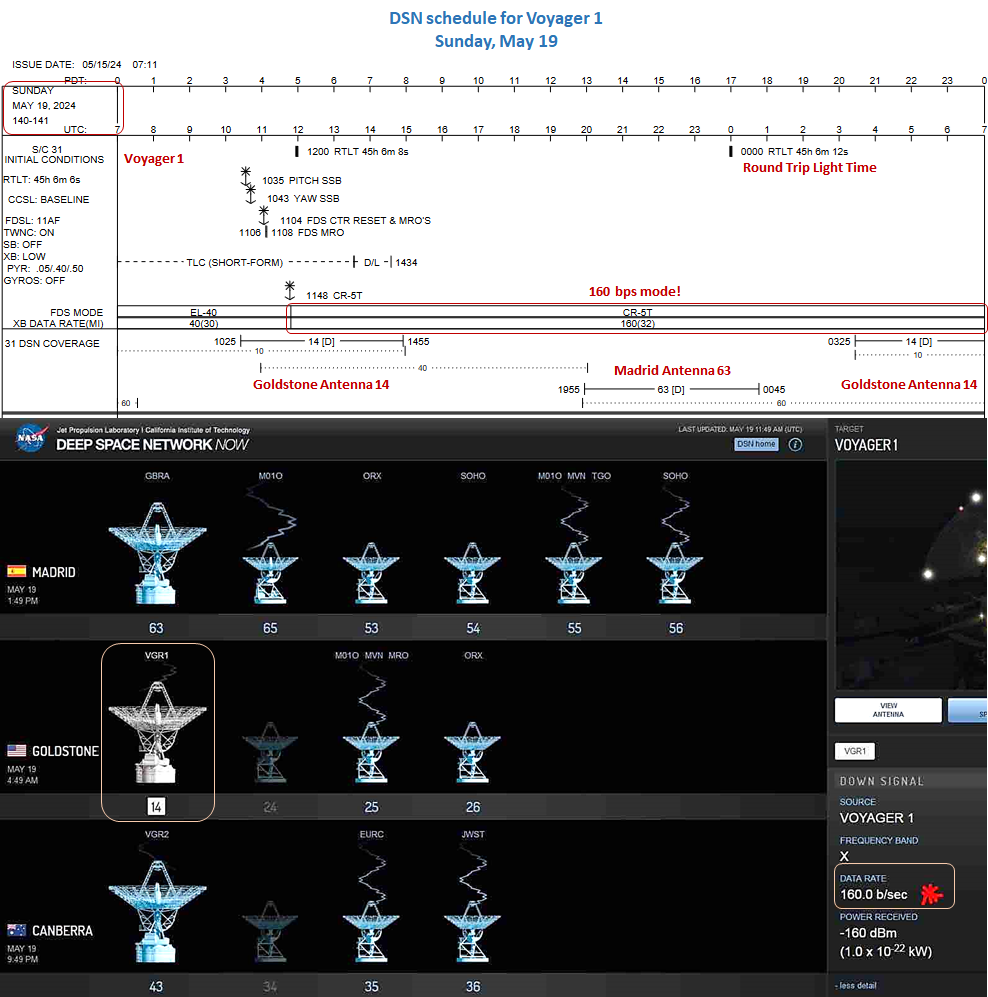
AkaSci@fosstodon.orgSix months after it suffered a serious brain injury and after months of mind-boggling ultra-long-distance surgery, the Voyager 1 spacecraft walked and talked at full data rate today!
After transmitting a full memory readout on Friday at 40 bps, Voyager 1 switched to the science-mode 160 bps rate, which presumably the DSN site at Goldstone was able to receive and decode today.
Congrats and kudos to all who made it happen.
👏 
https://eyes.nasa.gov/dsn/dsn.html
29/n
Dan Goodin
dangoodin@infosec.exchangeKernel.org folks never provided the postmortem they promised in 2011 after finding their infrastructure had been rooted. They also didn't bother to respond to my email earlier this week seeking comment on new information that, in fact, their servers had been rooted 2 years earlier by a 2nd, even more sophisticated piece of malware.
While no one responded to me, here's Linux Foundation member Konstantin Ryabitsev responding elsewhere to my post that the breach was the subject of an FBI investigation, and later of a lawsuit. This says lots about the obligation kernel.org, an organization entrusted with huge responsibility, feels toward transparency. If Microsoft did this, people would be apoplectic.
Mastodon Migration
mastodonmigration@mastodon.onlineStarlink is killing Hubble
Something about this plan to move Hubble, didn't make sense. If the space telescope still has 10 years of useful life, why this risky SpaceX mission to boost it's orbit now?
Well it turns out the main thing threatening the utility of Hubble is... wait for it... SpaceX Starlink satellites, which orbit just above Hubble constantly "photo-bombing" the images. Within a few years there will be so many Starlinks that Hubble will be useless.
https://www.nytimes.com/2023/03/02/science/hubble-spacex-starlink.html
Driftini
driftini@wetdry.worldHans-Christoph Steiner
eighthave@librem.oneThree years ago, #FDroid had a similar kind of attempt as the #xz #backdoor. A new contributor submitted a merge request to improve the search, which was oft requested but the maintainers hadn't found time to work on. There was also pressure from other random accounts to merge it. In the end, it became clear that it added a #SQLinjection #vuln. In this case, we managed to catch it before it was merged. Since similar tactics were used, I think its relevant now