Posts
2337Following
466Followers
1114Heretek of Silent Signal
AttackerKB
attackerkbSorry for the inconvenience!
frycos
frycos@infosec.exchangeYep, always a good idea to implement the HTTP stack from scratch.
Also: if you wanna stop me looking at your product, simply produce the most ugly code ever seen.
Kudos, both accomplished by CrushFTP.
James Forshaw 
tiraniddo@infosec.exchange
Released a new version of OleViewDotNet (v1.14) on the PowerShell gallery (https://www.powershellgallery.com/packages/OleViewDotNet/1.14). Too many features to list but a few big ones are, better support for ARM64 platforms and better source code formatting for proxies and type libraries to be as close as possible to the IDL format rather than the old pseudo C# one. In the UI you can also create a source code window and it'll automatically update when you click on things like enumerated interfaces or type library information. Here's a small video to show the feature off.
Sass, David
sassdawe@infosec.exchangeI think LinkedIn finally figured out how to organize the timeline like the bird site used to do it...
da_667
da_667@infosec.exchangeI'm not done ranting yet. I can't get over the fact that the multi-billion dollar company that can afford to buy Splunk at 28 billion can put out a report with near-zero actionable IOCs:
and that we have to rely on government entities to give us reliable details that are not secluded to binary blobs for detecting the exploit and/or backdoors.
https://www.cyber.gc.ca/en/news-events/cyber-activity-impacting-cisco-asa-vpns
buherator
buheratorhttps://blog.0patch.com/2024/04/micropatches-released-for-windows.html
buherator
buheratorhttps://www.positronsecurity.com/blog/2024-04-23-an-analysis-of-dheat-dos-against-ssh-in-cloud-environments/
remember how Naomi fucking told us this a YEAR AGO and no one wanted to believe it until the government knocked on her door and she can't post anymore?
https://www.technologyreview.com/2024/04/24/1091740/chinese-keyboard-app-security-encryption/
Kevin Beaumont
GossiTheDog@cyberplace.socialIn light of recent events, probably best to make this ASA vuln public in public interest: https://github.com/GossiTheDog/Exploits/blob/main/Cisco-CVE-2020-3259.sh
If you get <argument> back with toke inside, not vuln. If you get a memory dump back, you vuln. The dump is pretty bad as it contains a bunch of stuff.
The path exists even with webvpn disabled, it's the host checker.
Credits to person who found it, don't know if they want to be named. Edit: it’s @Naproxen
Akira and others have been living off this for a while.
yawnbox 
yawnbox@disobey.net
buherator
buherator_Veronica_
verovaleros@infosec.exchange@buherator @civilsphere @stratosphere @arstechnica
We presented in 2019 in some local conferences. And we talked about this with @eldraco at Ekoparty in 2022 (In Spanish, sorry): https://www.youtube.com/watch?v=uN0EVwWWMbs&t=32s
At some point we were keeping this list updated and we wrote some blogs but not on AVs:
https://www.civilsphereproject.org/research/mobile-applications-we-helped-improve
When we found the issues on the AVs apps, we wrote reports and send emails, and then we waited. Honestly we are a university research team and students come and go; eventually we moved on as it was too much work outside our 'core' research and teaching duties. We did it the right way, PDF reports with reproducibility and everything, and it was so much work. It was an exhausting season for us.
We still have the spreadsheet with all the issues we identified per AV.
buherator
buheratorhttps://blog.talosintelligence.com/arcanedoor-new-espionage-focused-campaign-found-targeting-perimeter-network-devices/
Note that while the vendor identified two vulnerabilities (CVE-2024-20353, CVE-2024-20359) these are related to post-exploitation, the initial access vector is still unknown.
Andy Greenberg
agreenberg@infosec.exchangeCisco warns that a group of state-sponsored hackers has exploited two zero days in its ASA security appliances to spy on government networks over the last several months. Sources close to the investigation tell us they suspect China. https://www.wired.com/story/arcanedoor-cyberspies-hacked-cisco-firewalls-to-access-government-networks/
pancake 
pancake@infosec.exchange
A 3yo presentation from @revng binary patching with high level languages https://www.youtube.com/watch?v=lLfxFVKzxwQ
buherator
buheratorbuherator
buheratorhttps://struct.github.io/auto_agents_1_day.html
PagedOut
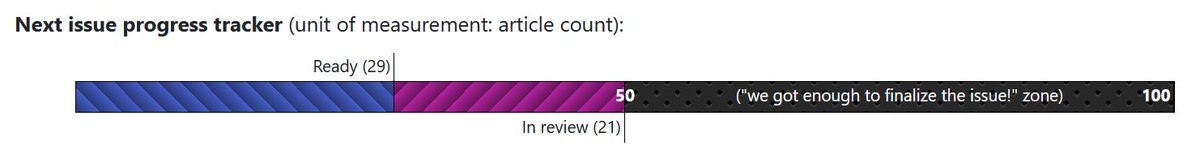
pagedout_zine@bird.makeupWe've got it! We've reached 50 articles needed to publish Issue #4. Once we're done with the reviews, it will be out!
So, if you still want to submit something for this issue, you need to hurry up :D
Do you want to place an ad in Issue #4? Visit https://pagedout.institute/?page=ads.php