Posts
2525Following
647Followers
1460So some fun stuff was just presented at 37C3, and... I bet I have some answers.
https://securelist.com/operation-triangulation-the-last-hardware-mystery/111669/
First, yeah, the dbgwrap stuff makes perfect sense. I knew about it for the main CPUs, makes perfect sense it'd exist for the ASCs too. Someone had a lightbulb moment. We might even be able to use some of those tricks for debugging stuff ourselves :)
Second, that "hash" is almost certainly not a hash. It's an ECC code**. I bet this is a cache RAM debug register, and it's writing directly to the raw cache memory array, including the ECC bits, so it has to manually calculate them (yes, caches in Apple SoCs have ECC, I know at least AMCC does and there's no reason to think GPU/ASC caches wouldn't too). The "sbox" is just the order of the input bits to the ECC generator, and the algorithm is a textbook ECC code. I don't know why it's somewhat interestingly shuffled like that, but I bet there's a hardware reason (I think for some of these things they'll even let the hardware synthesis shuffle the bits to whatever happens to be physically optimal, and that's why you won't find the same table anywhere else).
This explains the behavior where writing to KTEXT works "sometimes" and panics AMCC others. There is a vulnerability in the SoCs that *I* discovered and reported where cache snooping bypasses CTRR at the AMCC level. You can "write" to read only memory ranges and, as long as those writes remain in snoopable cache, they are effective even though AMCC will block them and panic when they are written back. I didn't get any money for that one because the way I exploited it didn't apply to normal macOS (I used it to patch DCP code from m1n1), but now a nation state figured out how to use it for a real exploit chain. "Whoops".
So what was being observed there was that writing to kernel text "worked" *as long as that cache line remained dirty*. Then once it got written back, AMCC panic.
This whole thing hinges on the elephant in the room that, for performance reasons, **there is no IOMMU for the GPU**. PPL security relies entirely on GFX-ASC uPLL software protection and the GPU page tables being managed properly by PPL. This fun fact got Lina a $150k bounty when she found major bugs across the stack that allowed a full takeover from userspace shaders. Now someone else figured out how to puppeteer either GFX-ASC or the GPU L2 cache* from EL2/1, bypassing PPL from the kernel. I bet this isn't the last time we're going to see fun memory bypasses that hinge on the GPU. Heck, for all we know, these attackers might've even been inspired by Lina's antics :)
The patch for this vector is trivial: you don't let the kernel map that register range via PPL. Now the question is, how long until someone else finds another fun bypass using another obscure feature or bug of the GPU or its firmware?
* Probably the GPU L2, since as far as we know the GFX-ASC L1 isn't system fabric coherent, but GPU L2 is.
** Why do I know about ECC codes? Because this is the same algorithm used for ECC on the Nintendo Wii NAND lol, I've literally written this code before.
hanno
hanno@mastodon.socialSecurity vulnerabilities in Antivirus software are no big deal, right? I mean, they never get exploited for real, right? Like this one, where Barracuda just ran a random, unaudited perl library with eval in it as part of its Antivirus, and then some malware used it. That's basically a non-issue some infosec people like to overblow because they don't like AVs. https://www.barracuda.com/company/legal/esg-vulnerability
web3 is going just great
web3isgreat@indieweb.socialTether mints itself a $1 billion Christmas present
December 25, 2023
https://web3isgoinggreat.com/?id=tether-christmas-2023-mint
✧✦Catherine✦✧
whitequark@mastodon.socialI finally did it!!!
a complete FPGA toolchain (synthesis, placement, routing, and programming) running entirely in the browser
Hacking a Philips toothbrush head to allow you to use it beyond its normal lifetime. Yes, the toothbrush _head_ is hackable. This is a fantastic tale of reverse engineering. Be sure to read the followup at the bottom of the article.
mhoye
mhoye@mastodon.socialIf you're feeling any sort of impostor syndrome, watch this presentation where the guy leading the team that's invented just-in-time optimizing-for-parallelism shell script recompilation admits at the end that after having done all that he still has to look up the bash "if then else" syntax every time.
Maybe you're not an impostor, maybe you're succeeding even though all this stuff is genuinely hard to use.
https://www.usenix.org/conference/osdi22/presentation/kallas
it's!! cassie!! time!!!
aronia@tech.lgbtkeygen chiptune is the evolution of sea shanties: music that plays while you pirate 
Very Hairy Jerry
jerry@infosec.exchangeIt sure is a good thing people chased away CISA last year. I mean, look at the propaganda they post. I’m super glad we made people stay on the other site to access this filth.
Yes, I’m having a moment of bitterness
Peter Gleick
petergleick@fediscience.orgBezos and Musk have it deeply wrong.
The problem isn't that we need a trillion people to have more Einsteins or Mozarts.
The problem is we don't nurture and protect the ones we have.
Stephen Jay Gould wrote: "I am, somehow, less interested in the weight and convolutions of Einstein's brain than in the near certainty that people of equal talent have lived and died in cotton fields and sweatshops".
Hacker News
hkrn@mstdn.socialOpen source rules engine for Magic: The Gathering
L: https://github.com/Card-Forge/forge/wiki
C: https://news.ycombinator.com/item?id=38651346
posted on 2023.12.15 at 00:40:06 (c=21, p=197)
Johnathan Norman
spoofy@infosec.exchangeNew blog just dropped. https://techcommunity.microsoft.com/t5/security-compliance-and-identity/a-new-modern-and-secure-print-experience-from-windows/ba-p/4002645 We are making massive changes to the Print System in Windows to improve security. This represents a pretty big leap forward for security in Windows. The Print System in Windows has historically been a key target for attackers and these changes make significant reductions in total attack surface.
More over, we intend for this to become the default for users in the future. No more loading 3rd party print drivers, no more high privilege services, and robust exploit mitigations enabled to protect users.
There is a lot of work to do, this first release is only a step in the direction we are taking. But I feel it is the right direction for user safety.
Adam Shostack 

adamshostack@infosec.exchange
"A security researcher uncovered a Twitter vulnerability in its link shortener. The vulnerability allowed an attacker to craft a malicious URL that, if a user clicked on it, would grant the attacker access to the user's account. The researcher reported the vulnerability to Twitter's bug bounty program, which closed the report as not worthy of a bug bounty. So the researcher published the vulnerability. Immediately Twitter takes its link shortener offline for hours while they fix it.But the press is only reporting on an hours-long X/Twitter link shortener outage, and has completely missed the security issues that led to it.Molly White's coverage of the vulnerability (sorry for the Xitter link but that's just the problem, literally no one else is covering this): https://twitter.com/molly0xFFF/status/1734965774517768471 "
Disclosure: https://x.com/shoucccc/status/1734802168723734764?s=20
(All quoting a friend on a private slack)
nixCraft 🐧
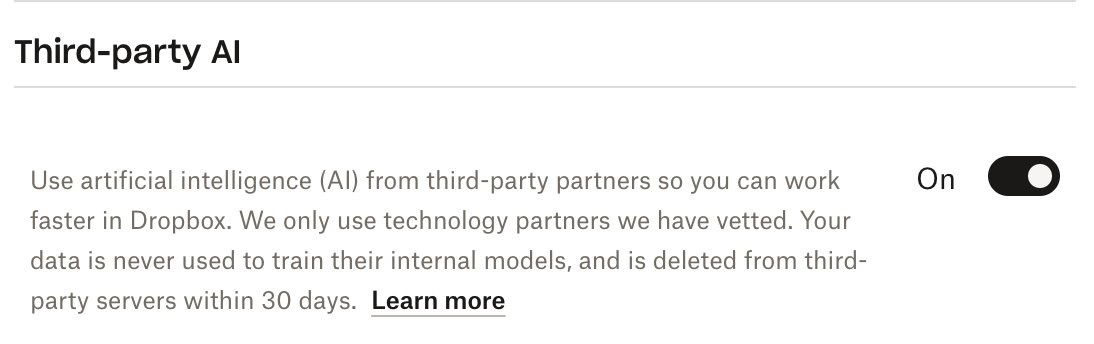
nixCraft@mastodon.socialAre you using Dropbox cloud storage? You do not want 3rd party AI technology partners to have access to your Dropbox files? Flip this switch, which is on by default. Go to web->account-> settings- 3rd party AI. Please turn it off. Please boost so everyone know how bad this move is … 😡
Siguza
siguza@infosec.exchangeGmail has once again blacklisted my mail server because of the SIX emails I have sent in the entirety of December so far, because obviously that constitutes "an unusual rate of unsolicited mail".
I set up SPF, DKIM, DMARC, first get lumped in with a bad /24 IP block, slowly build up a reputation as a non-spammy IP, etc. etc., but none of that matters.
This is nothing but a racketeering scheme to force everyone to pay for Gmail for business.
Kee Hinckley
nazgul@infosec.exchange@jerry @bhawthorne @karl This is relevant to your comment about accusations, I promise.
Once upon a time there was an urban legend that putting 0wormalert@somewhere.com in your address book would protect you from email worms. The theory (speaking of Dunning-Kruger) was that the virus would send email to everyone in the address book, and since the first address didn’t exist, it would fail to propagate.
I owned somewhere.com.
At the time I was bouncing about a million messages a day, with peaks up to 2.5 million when some new email worm came out, and needless to say, I was tracking what addresses were bouncing (like the one that was kept getting video clips from inside jewelry stores), and I noticed this one very high on the list, so I routed it to my email to see what was up.
What kind of email do people send to everyone in their address book?
Urban legends of course. And anyone who had done this little hack was probably very susceptible to believing urban legends, so there were a lot of them. And a lot of repeats.
So I set up an auto-responder, and anytime someone sent mail to the address, it sent email back explaining why what they’d done wasn’t going to work, and debunking a dozen or so of the most common urban legends.
And boy did they get pissed.
The first surprise wasn’t that they didn’t believe my explanation. We didn’t even get that far. It was that most of them denied putting the address in their address book at all. Or of even *having* it in their address book. Yet there it was in their email.
The second surprise was how many of them accused me of hacking into their computer. People threatened to call the FBI. They tried to report me to my ISP. They blamed it all on me. (In retrospect, maybe I shouldn’t have done a reply-all, but I was hoping to slow the spread, and this was before alternative facts and Q and all that stuff showed how hopeless that was.)
I did send a write-up to my college anthropology professor on the off chance a student wanted to write a paper about it, but no takers. I’ve still got all the emails though if anyone wants them. :)
Henri Sivonen
hsivonen@mastodon.socialSadly, C++ standardization leadership’s engagement with the memory safety topic is going even more embarrassingly badly than in January:
https://pony.social/@thephd/111550692413752045
The very first sentence is: “Memory safety is a very small part of security.” … Despite the result that about 70% of software vulnerabilties are memory-safety issues has been repeated at multiple organizations (Mozilla, Microsoft, parts of Google, IIRC also Apple).
…
Michael Lucas 
mwl@io.mwl.io
Computers are like onions. Everything is layers built on layers, and every layer makes you cry. #sysadmin
Ciara
CiaraNi@mastodon.greenWe need a word for real-life enshittification caused by online culture. Like being unable to find an organisation’s info because they’ve Instagram but no website. Or panicked people being sent a videolink to download to their phone when they ring for an ambulance. Or being excluded from residents' association news if you're not on Facebook. Or having cash payment refused. Or staff in the business you’re physically standing in telling you to find the answer to your question on their website.
Robert McNees
mcnees@mastodon.socialComputer science pioneer and United States Navy rear admiral Grace Hopper was born #OTD in 1906.
As far as I’m aware, she is the only person who has both a supercomputer and a US Navy destroyer named after her.
Image: Computer History Museum
Frederik Braun �
freddy@security.plumbingAnnoyed that a website is doing something custom on right-click?
Did you expect the browser's context menu (Back, Reload, Save Page As, View Source etc.)?
Just hold the ⇧Shift key while clicking and Firefox will show the built-in context menu.
Edit: I had no idea this was such a widely appreciated post. Credit where credit is due: @dveditz told me about this trick a couple of months ago.