Posts
2530Following
647Followers
1459Molly White
molly0xfff@hachyderm.io"it's not like we can put the genie back in the bottle! 🤷" – VC who stands to profit massively from the release of the genie, and who has worked tirelessly to release said genie
Mx. Moriarty 🏳️⚧️ 
jpasski@infosec.exchange
Lol looks like JFrog finally disclosed CVE-2022-0668 [1]. @matthias_kaiser and I found that around a year ago, along with CVE-2022-0573 [2]. Coupled together we could unauth RCE Artifactory 🔥
Funny how they marked the RCE as being as severe as a blind SQLi, a “High”🤪
In neither case were we told the issues were fixed… 🙈🙉🙊
1. https://www.jfrog.com/confluence/display/JFROG/CVE-2022-0668%3A+Artifactory+Authentication+Bypass
2. https://www.jfrog.com/confluence/display/JFROG/CVE-2022-0573%3A+Artifactory+Vulnerable+to+Deserialization+of+Untrusted+Data
Kevin Beaumont
GossiTheDog@cyberplace.socialI wonder if Microsoft should meaningfully strengthen HTA files (not with SmartApps)… (yes, they definitely should) HT @campuscodi
hexnomad
hexnomad@infosec.exchangeTwo vulnerabilities I disclosed to @msftsecresponse got patched today. https://msrc.microsoft.com/update-guide/vulnerability/CVE-2023-23415 and https://msrc.microsoft.com/update-guide/vulnerability/CVE-2023-23416. Both are are RCE and given critical severity. The first is a pre-auth vuln in ICMP.
From the bulletin:
How could an attacker exploit this vulnerability?
An attacker could send a low-level protocol error containing a fragmented IP packet inside another ICMP packet in its header to the target machine. To trigger the vulnerable code path, an application on the target must be bound to a raw socket.
The research fairy
researchfairy@scholar.socialOkay so everybody get ready to preemptively suspend the domain once we know what it is
> Meta is building a decentralized, text-based social network
https://www.platformer.news/p/meta-is-building-a-decentralized
> The app is codenamed P92
> The P92 app will support ActivityPub, MoneyControl reported
Mallory Knodel
mallory@techpolicy.socialMajor win for encryption.
European Data Protection Supervisor Wojciech Wiewiórowski said the indiscriminate scanning of private communications proposed by EU’s CSAM regulation “will always be illegal under the Charter of Fundamental Rights (and probably under several national constitutional laws as well),” https://www.euractiv.com/section/law-enforcement/news/eu-watchdog-online-child-abuse-draft-law-creates-illusion-of-legality/
Kevin Beaumont
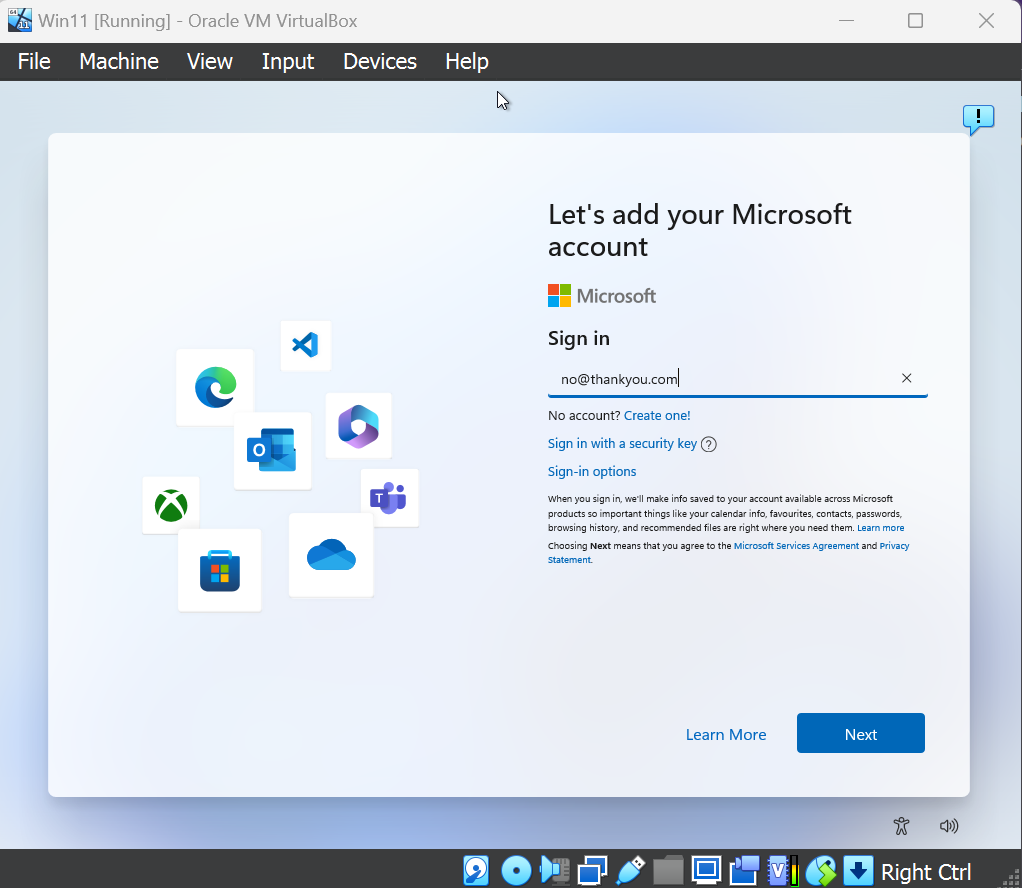
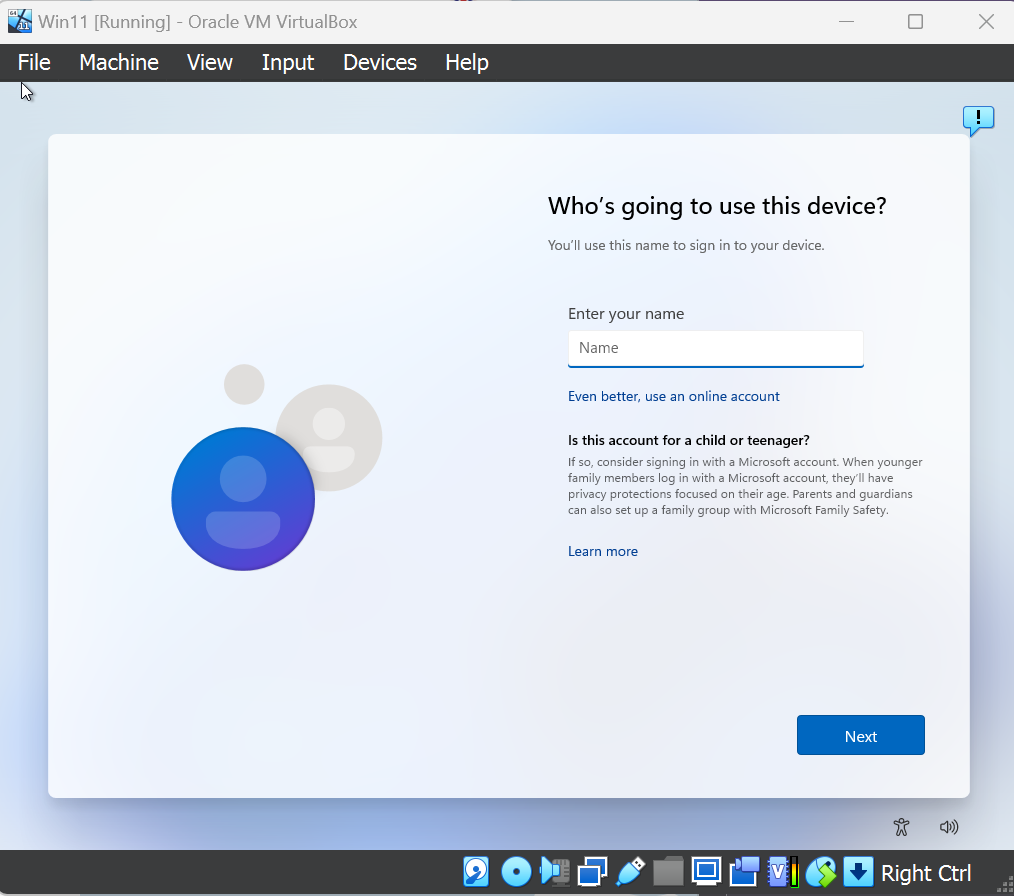
GossiTheDog@cyberplace.sociallol, a way to bypass the Microsoft account requirement in Windows 11 - type username no@thankyou.com, any password, and it bumps you to local account creation.
HalvarFlake
HalvarFlake@mastodon.socialBlackLotus Shows again: Revocation lists don't work, and Code Signing is not going to save you.
buherator
buheratorRyan Cordell
ryancordell@hcommons.socialLast night the 11yo broke down the Google Slides middle school Chatroom for me:
1. At first they used a Google doc but the infinite scroll was too chaotic
2. In the slide deck each new slide is one “post”—some all text, some images, some both—
3. They use slides’ comments feature to “reply” to each other’s “posts”
4. This allows participants to easily flip between posts using the slide thumbnail navigation, so they can find the conversations they care about easily
5. He owns the file & if anyone spams it, deletes other people’s posts, or gets nasty, he can revert the file to its previous save state & remove the spammer’s access
6. He did share the file with me on purpose, I think because he was proud & wanted me to see what he’d made
Essentially they’ve created a chatroom with moderation in Google Slides, so they can get around the school’s ban on platforms like Discord. It’s kind of brilliant
buherator
buheratorCan some native #English speakers take a look? (clarification in alt text)
Jake Williams
malwarejake@infosec.exchangeKudos to Coinbase for publishing this fantastic write-up on social engineering. Really would love to see more orgs normalizing their wins (because make no mistake about it, this IS a win).
https://www.coinbase.com/blog/social-engineering-a-coinbase-case-study
buherator
buheratorThinkst Canary
ThinkstCanary@mastodon.sdf.orgOur (free) AWS Canarytokens have always been popular.
Today, we released the Azure alternative on our canarytokens.org server¹
Attackers who find ‘em have to use ‘em (and reveal their presence).
Check out Pieter’s blog post at:
https://blog.thinkst.com/2023/02/canarytokens-org-welcomes-azure-login-certificate-token.html
__
¹ also free
frycos
frycos@infosec.exchangeattackerkb published their GoAnywhere analysis. No more reasons to hold back my blog post then, I wrote days ago.
https://frycos.github.io/vulns4free/2023/02/06/goanywhere-forgotten.html