Posts
2923Following
696Followers
1535buherator
buherator
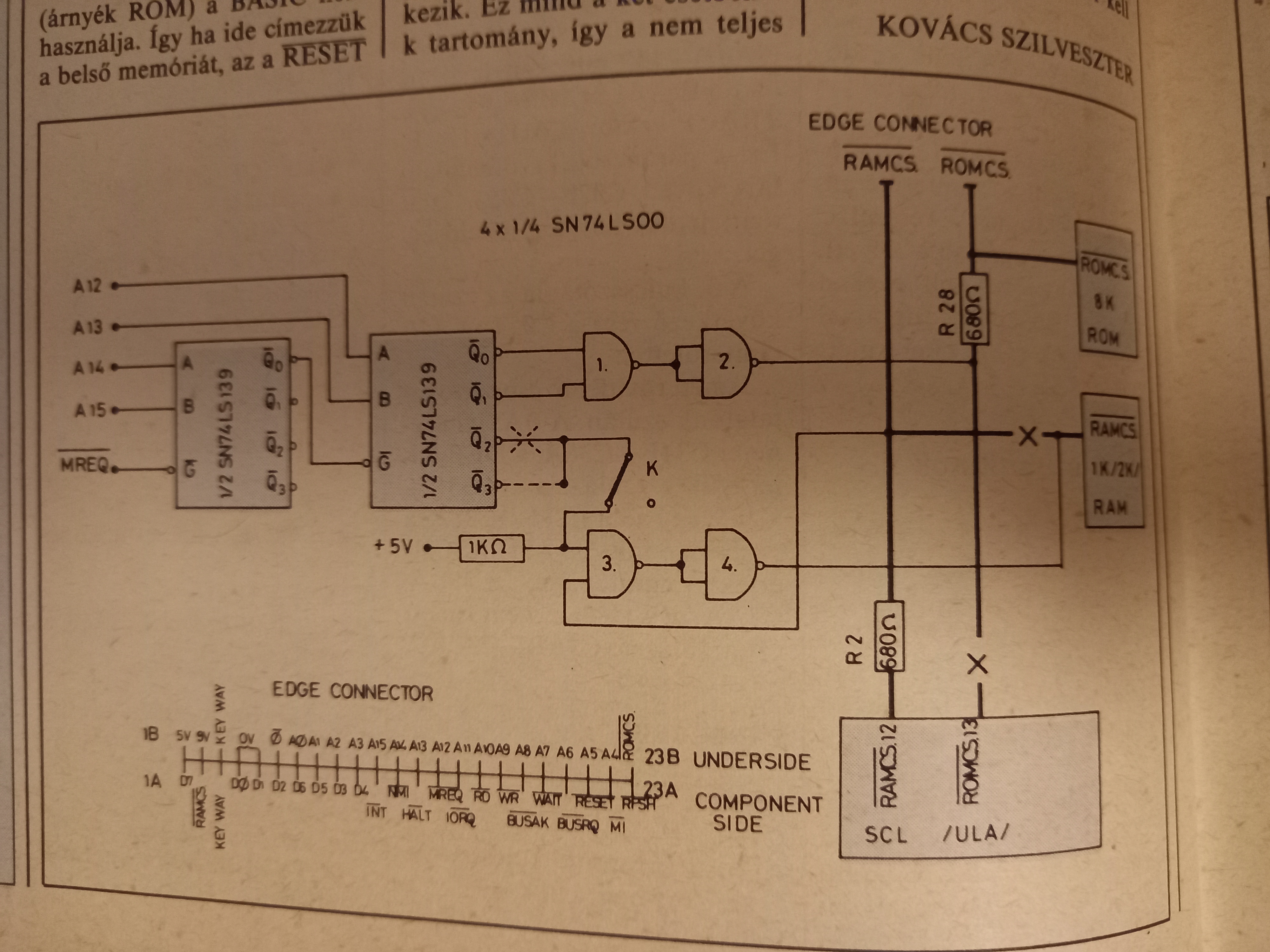
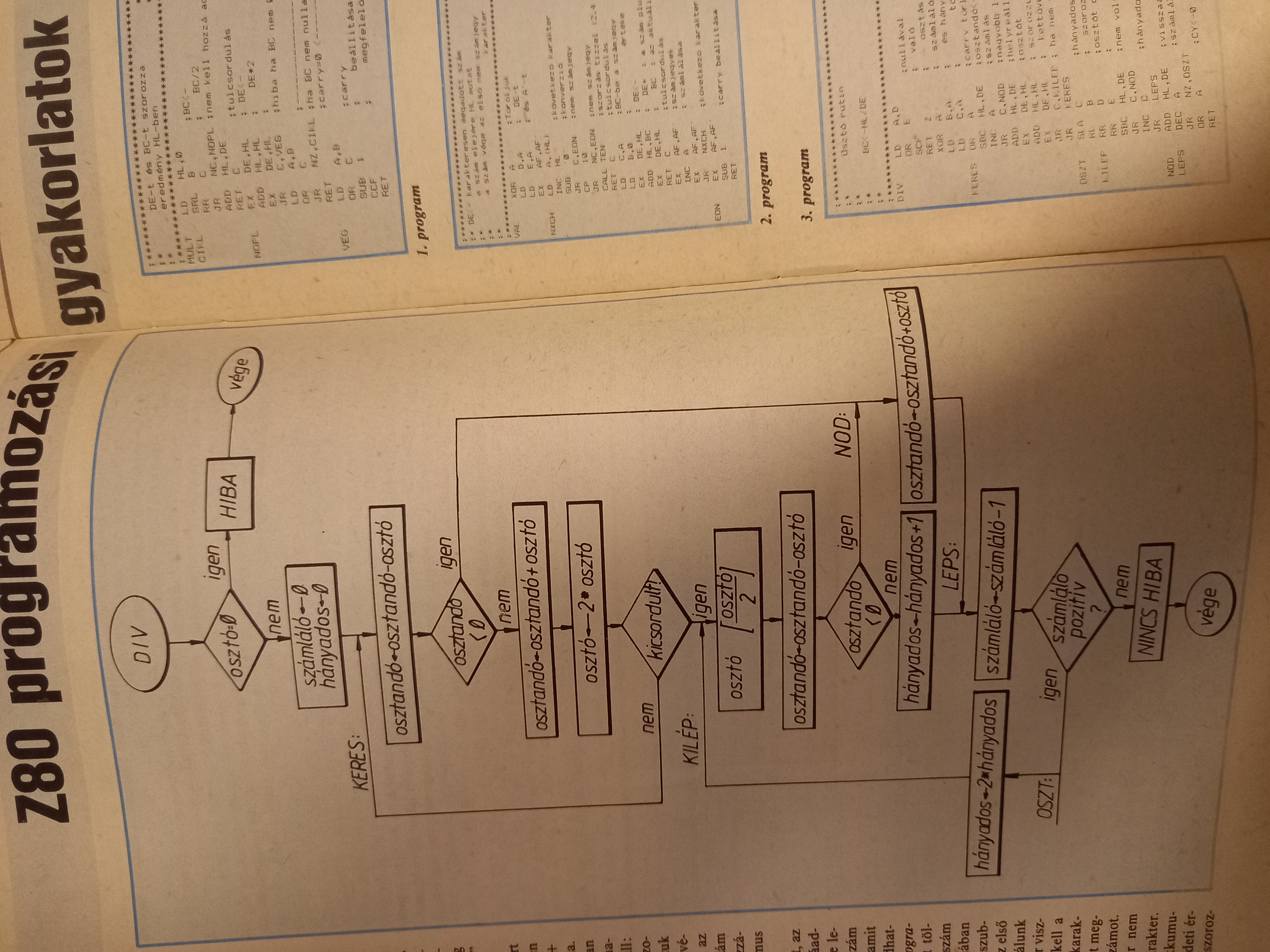
This supposed to be the listing of a text editor program for Spectrum. As I said the issue is in top condition, the typography is just bad here
buherator
buherator
In #Hungarian we don't distinguish between "safety" and "security", which leads to confusions. I made this meme, but I'm not sure it's right.
Can some native #English speakers take a look? (clarification in alt text)
Can some native #English speakers take a look? (clarification in alt text)