Posts
2408Following
469Followers
1120Heretek of Silent Signal
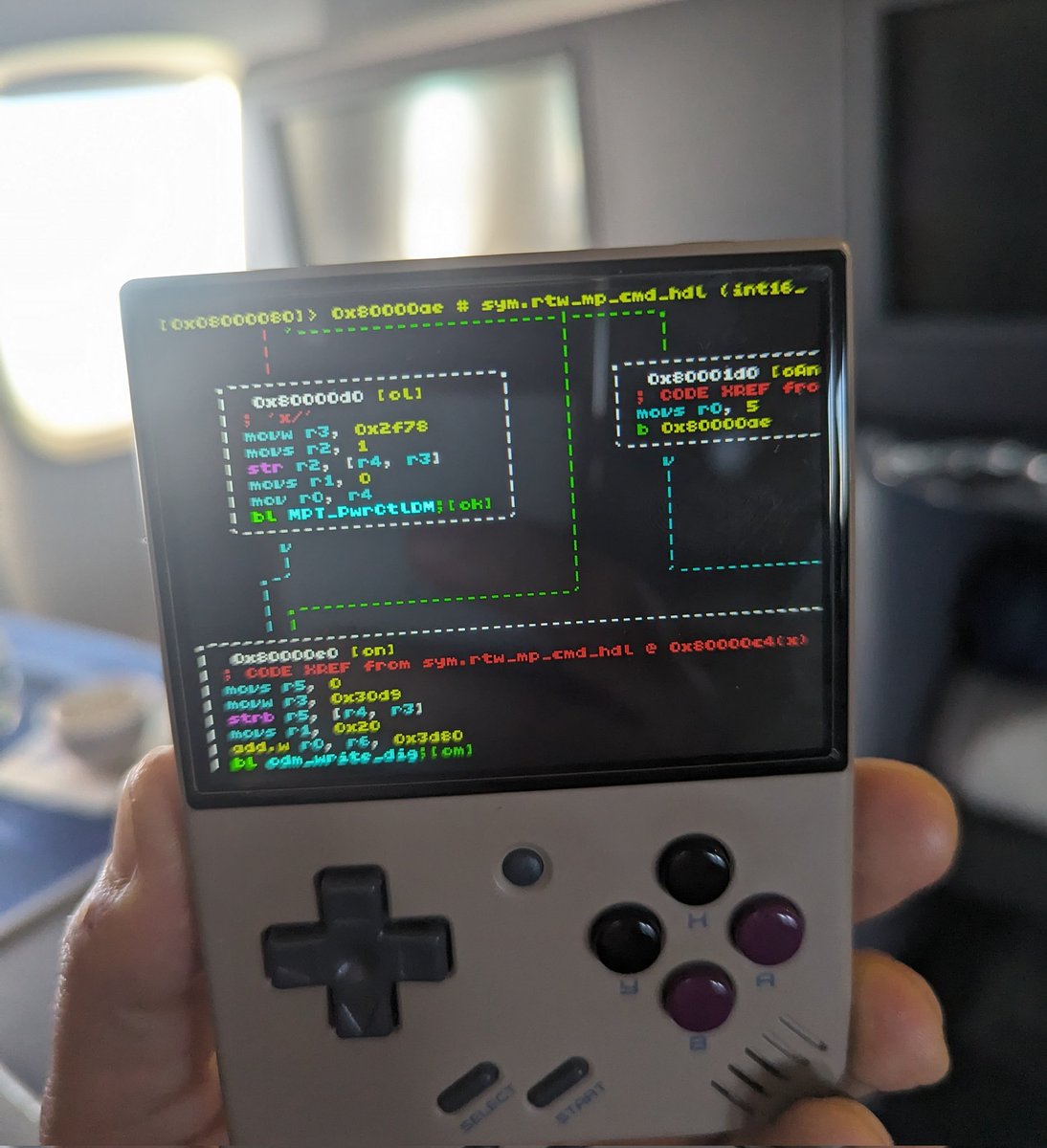
hackaday
hackaday@hackaday.socialIn his Supercon 2023 talk, Nathan Jones explains what the "Voja4" badge has to offer for those looking to explore bare-metal programming.
https://hackaday.com/2024/05/20/supercon-2023-exploring-the-elegance-of-the-voja4/
mycorrhiza
mycorrhiza@post.lurk.orgI’m not an Arch user, but the Arch Wiki has become the best place to figure out how to do some random thing in Linux. Nice work Arch people — thank you.
rev.ng
revng@infosec.exchange😎 We're going to REcon 2024! 😎
This will be the first talk in which we introduce the decompiler since the open source release.
It will be very much an hands on talk. Don't miss it.
See you in June in Montreal! ⚜️🌹☘️
buherator
buheratorhttps://git.sr.ht/~alip/syd/tree/main/item/doc/toctou-or-gtfo.md
Not Simon 🐐
screaminggoat@infosec.exchangeHorizon3: CVE-2023-34992: Fortinet FortiSIEM Command Injection Deep-Dive
Horizon3 provides a vulnerability analysis and proof of concept for CVE-2023-34992 (9.8 critical, disclosed 23 October 2023 by Fortinet) OS Command injection vulnerability in FortiSIEM supervisor due to improper neutralization of special elements.
Sidenote: This is the same 23 October 2023 security advisory that Fortinet buried two additional vulnerabilities (CVE-2024-23108 and CVE-2024-23109 have a perfect score of 10.0 cc: @cR0w) on 06 February 2024. When @serghei of Bleeping Computer asked about it, "Fortinet told me these two are duplicates of the original CVE-2023-34992. Fortinet says they got accidentally added and pushed to NVD automatically because of an API issue they're investigating."
Zach Hanley (who submitted all of these vulnerabilities and Horizon3's blog post) disputed what Fortinet said, posting a Twitter screenshot showing email communication between him and PSIRT Ticketing* System showing confirmation for CVE-2024-23108 and CVE-2024-23109: "Lol not sure whats going on over there, but they're real were a bypass of the 2023 CVE it got added to."
Fortinet then updated the security advisory sometime around 08-09 February 2024, crediting Zach Hanley/Horizon3 and backdating the update to 31 January 2024.
as @catsalad said in a previous toot, recommend temporary fix is to "Just pull the power"
#CVE_2023_34992 #proofofconcept #CVE #Fortinet #vulnerability #fortisiem
buherator
buheratorAn electronic toothbrush that doesn't tip over when you look at it.
Between this Times article on tween boys obsessing about designer colognes and this Bloomberg article about an MLM scheme hawking "stock trading" tips to teens, I really get the feeling that we're failing the youth, but not in the way megachurch pastors might normally say.
It's not too much pornography and a lack of good family values. It's too much capitalism and marketers taking advantage of kids to turn a quick buck.
cynicalsecurity 
cynicalsecurity@bsd.network
Read @bert_hubert ‘s blog post¹ on the state of security or, more precisely, the dire state of technical knowledge across Europe (and not only) making it impossible to actually maintain the infrastructure we have.
It is, as they rightly point out, a mixture of pointless complexity for the sake of complexity (they use a moveable bridge over a canal, I think just pointing at Word is enough), complacency, shortsightedness and, in a well-placed quip, the techies opting out of the meeting outsourcing their job because these meetings are boring.
It pains me that “we built these networks, we’ll take them back” is now describing a bunch of 50+ techies wanting to stop suffering from looking at the current infrastructure.
For all of Bert’s influence there is only so much influence they can have and the rest of us have either been kept carefully far from the action or have decided not to participate.
My only hope is to eventually be the equivalent of the 75yr old Siemens pensioner being called by the bright and young at CERN ‘cos nobody knew how to fix the granite flywheel…
__
¹ https://berthub.eu/articles/posts/cyber-security-pre-war-reality-check/
yomna ♥ يمنى
rival_elf@infosec.exchange(1/3) News about what I've been working on for the last ~3 years to improve cellular security @ Android!
Android now newly supports notifications if your phone connects to a network without encryption, or if your IMSI/IMEI/SUCI are disclosed in the clear (can help detect IMSI-catcher attacks).
https://security.googleblog.com/2024/05/io-2024-whats-new-in-android-security.html
Nicole Express
nicole@bitbang.socialNew blog post! I take a look at the Yamaha MDP-10, a boombox that plays floppy disks, and my computer crashes while trying to play Sonic and Knuckles. Connection? You'll have to read it to find out https://nicole.express/2024/elementary-midi-watson.html
buherator
buheratorhttps://youtu.be/xCGKPRiJp84?si=M8o4zBlHh_YueCr_&t=1553
[1] https://berthub.eu/articles/posts/cyber-security-pre-war-reality-check/
[2] https://bsd.network/@cynicalsecurity/112468795879743909
[3] https://infosec.place/notice/Ai3X2gievLP2m9YRns
Forbearance
Forbearance@mastodon.xyzwe have trained on
the messages
that were in
the Slack
and which
you were probably
keeping
confidential
forgive me
they were delicious
to our new
AI model
AttackerKB
attackerkbTopic description: "NETIS SYSTEMS MW5360 V1.0.1.3031 was discovered to contain a command injection vulnerability via the password parameter on the login page. ..."
"[metadata only] ..."
Link: https://attackerkb.com/assessments/1671c0a1-d996-4224-8034-3782acdb3bad
Michael W Lucas¹ 
mwl@io.mwl.io
36 hours until "Run Your Own Mail Server" launches on Kickstarter.
Control your communications. Never surrender the protocols.
#ryoms #sysadmin
https://www.kickstarter.com/projects/mwlucas/run-your-own-mail-server
VNC Resolver
vncresolver@fedi.computernewb.comIP Address: 95.81.228.15
Port: 5900
Location: Cheboksary, Chuvash Republic 🇷🇺
ASN: AS12389 PJSC Rostelecom
Client Name: yaltch-crb-43@yaltch-mtay1.med.cap.ru
Hostname: 015.228.81.95.chtts.ru
ComputerNewb ID: 95465214
https://computernewb.com/vncresolver/browse/#id/95465214
hanno
hanno@mastodon.socialI'll be giving a talk at the miniDebConf Berlin about the Debian-OpenSSL-Bug-in-DKIM disclosure, and there is a livestream, in around 1,5 hours. https://berlin2024.mini.debconf.org/