buherator
buheratorRoyce Williams
tychotithonus@infosec.exchange@buherator One hokey work around for YubiKeys specifically is to use their configuration program to temporarily drop support for FIDO2, leaving U2F enabled. Then register the key. Then re-enable FIDO2.
buherator
buherator(This is fucking ridiculous btw.)
Dan Goodin
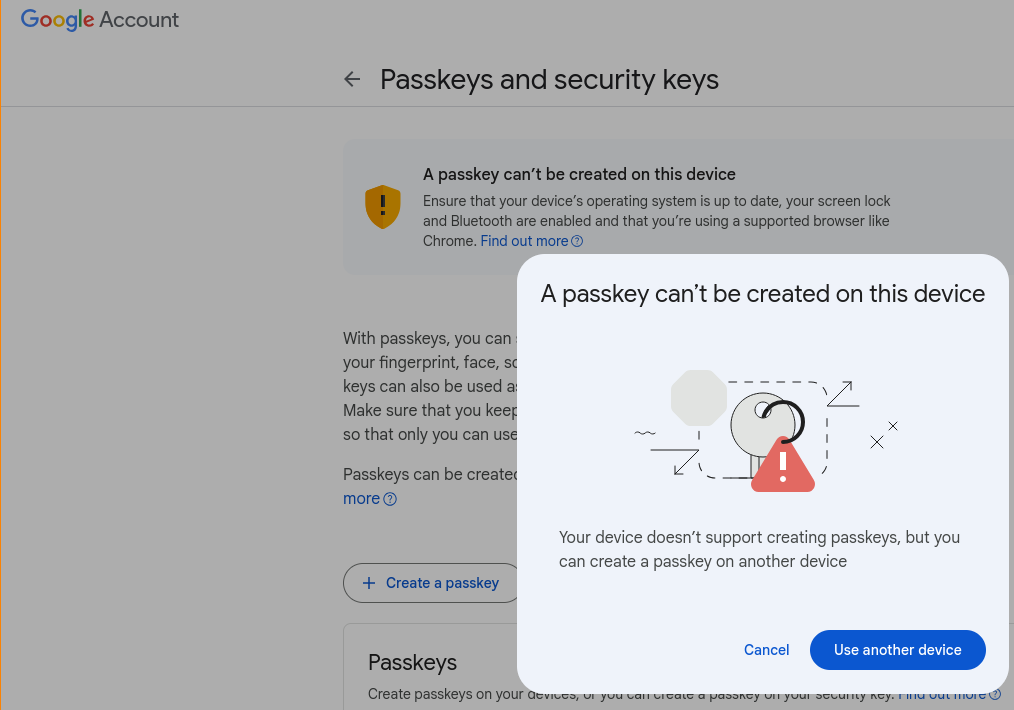
dangoodin@infosec.exchangeGoogle Account > Security > Passkeys and Security keys > + create a passkey. Google et al. seem to use "passkey" and "security key" interchangably. Yes, this is confusing, but clicking + create a passkey lets you create as many security keys as your heart desires.
buherator
buheratorMatt Franz
mdfranz@infosec.exchange@buherator @dangoodin @tychotithonus Wait until you try Passkeys with GCP 
buherator
buheratorRoyce Williams
tychotithonus@infosec.exchangeYep, that's what I interpreted the OP as meaning. If you take this path, unless it's already a U2F-only device, it's just created a passkey on the security key:
Royce Williams
tychotithonus@infosec.exchangeThat dialog is shown for passkey creation locally, rather than the "Use another device" option (which does work on Linux, but still ends up creating a passkey on that other device (security key))
buherator
buheratorThis is actually a major push to kill my Google account: it's the key to a lot of places, but because of BS like this I can't secure it properly.
Royce Williams
tychotithonus@infosec.exchangeYTMMV (Your Threat Model May Vary)!
One more note: when it's been done successfully, there's a warning attached to any key registered that way: "This key can only be used with a password" (which is, for you personally, a feature rather than a bug).
The first key shown was forced to U2F temporarily (no passkey). The second key was not (so it has a passkey on it). Note also the difference in icons.