404 Media
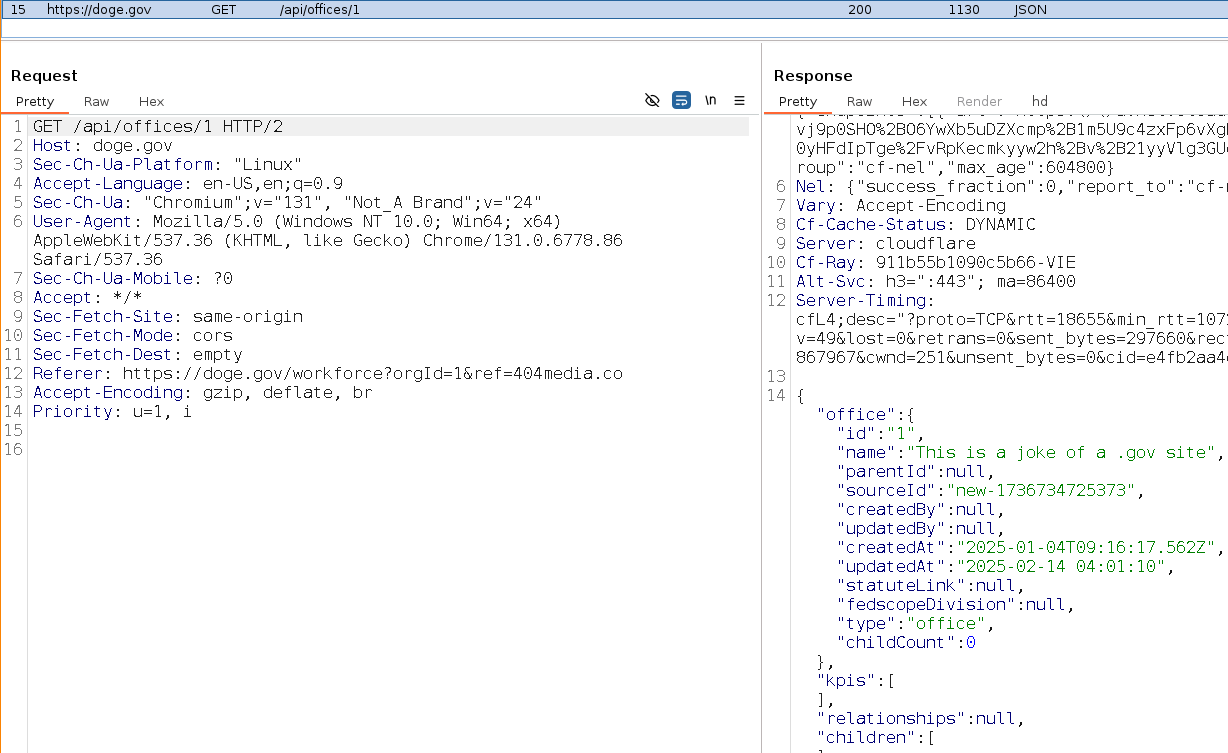
404mediaco@mastodon.socialScoop: The databases powering doge. gov are insecure, and people outside the government have already pushed their own updates to the site to prove it:
https://www.404media.co/anyone-can-push-updates-to-the-doge-gov-website-2/
@404mediaco the 20 year old hitler youths recruited from the exploding car company and the monkey trepanning company aren't actually good at computers? SurprisedPikachu.jpg
buherator
buherator
Dave "Wear A Goddamn Mask" Cochran 
dave_cochran@infosec.exchange
@404mediaco I expect every single one of you to act appropriately.
Natalie
cainaru@mastodon.social@404mediaco this has made me cackle and howl from laughter so hard that I just startled my cat.
b̴̨h̷̢̨s̴̡̡̕͡ù̢á̴͘͠r͘͝e̛͠z̨̀
bh@suarez.social@buherator @404mediaco doesn’t #cloudflare have a responsibility to secure this or do they just go 🤷 ?
buherator
buheratorb̴̨h̷̢̨s̴̡̡̕͡ù̢á̴͘͠r͘͝e̛͠z̨̀
bh@suarez.social@404mediaco @buherator they’re using Cloudflare Pages
b̴̨h̷̢̨s̴̡̡̕͡ù̢á̴͘͠r͘͝e̛͠z̨̀
bh@suarez.socialbuherator
buheratorb̴̨h̷̢̨s̴̡̡̕͡ù̢á̴͘͠r͘͝e̛͠z̨̀
bh@suarez.social@404mediaco @buherator so if I’m understanding correctly, Cloudflare can be used to deploy an unsecured government database and there is nothing wrong with that? I get the user provides implementation but DOGE is not really following the law…
buherator
buheratorb̴̨h̷̢̨s̴̡̡̕͡ù̢á̴͘͠r͘͝e̛͠z̨̀
bh@suarez.social@buherator @404mediaco sure, but they made the deliberate choice to use Cloudflare instead of a “mainframe” elsewhere. If you ‘dig a doge.gov’ both A records point to Cloudflare so how are they not relevant here?
b̴̨h̷̢̨s̴̡̡̕͡ù̢á̴͘͠r͘͝e̛͠z̨̀
bh@suarez.social@buherator @404mediaco then you do ‘dig a irs.gov’ and you can whois the IP and it’s owned by ‘Internal Revenue Service’ — not Cloudflare
b̴̨h̷̢̨s̴̡̡̕͡ù̢á̴͘͠r͘͝e̛͠z̨̀
bh@suarez.social@404mediaco @buherator bug or not this is horribly bad deployment practices and Cloudflare could cut them off if they wanted to but they haven’t
buherator
buheratorb̴̨h̷̢̨s̴̡̡̕͡ù̢á̴͘͠r͘͝e̛͠z̨̀
bh@suarez.social@404mediaco @buherator ok but my CPU isn’t on someone else’s computer
b̴̨h̷̢̨s̴̡̡̕͡ù̢á̴͘͠r͘͝e̛͠z̨̀
bh@suarez.social@buherator @404mediaco also malware doesn’t infect a CPU it infects an operating system…?