Kevin Beaumont
GossiTheDog@cyberplace.socialMerry Christmas to everybody, except that dude who works for Elastic, who decided to drop an unauthenticated exploit for MongoDB on Christmas Day, that leaks memory and automates harvesting secrets (e.g. database passwords)
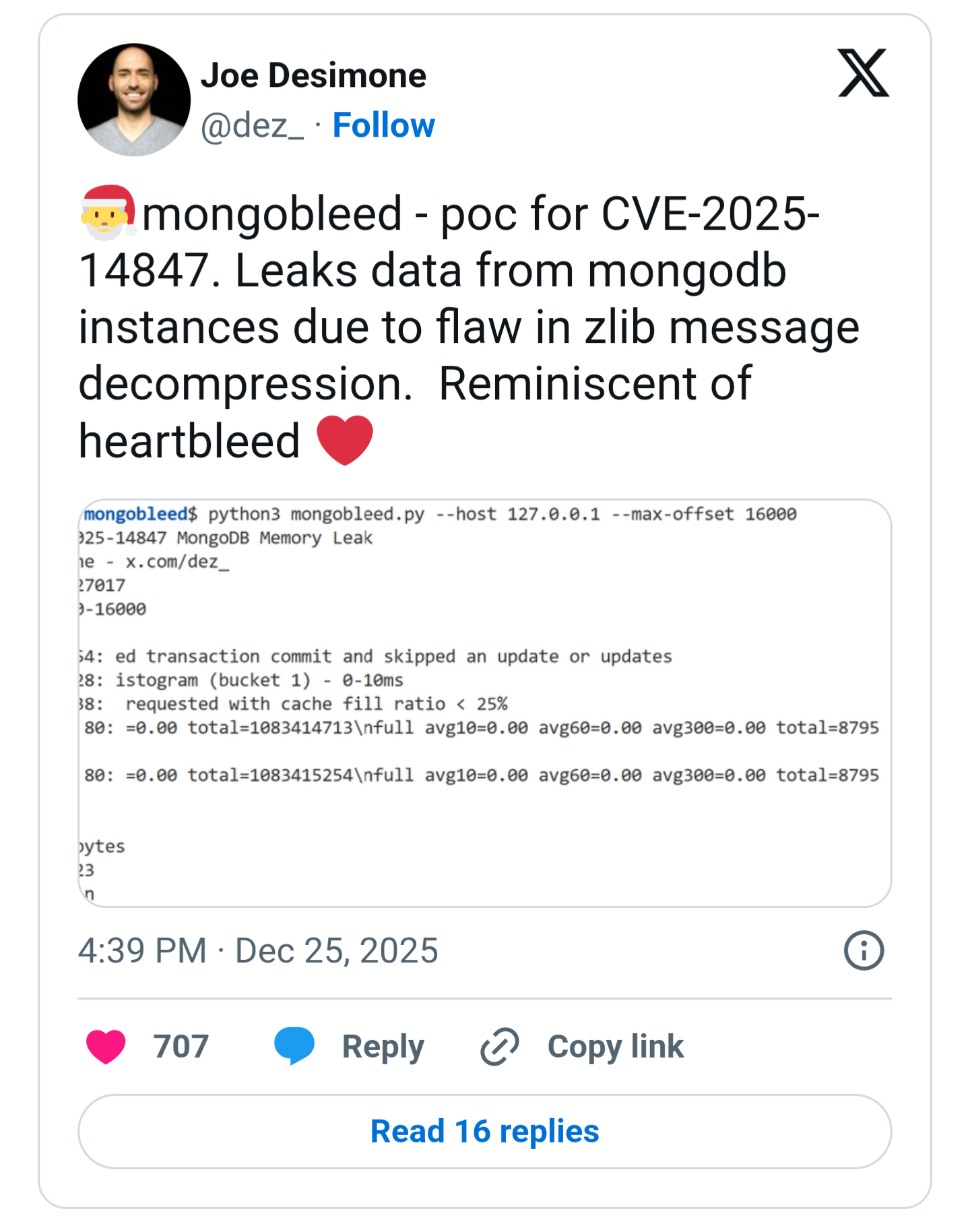
CVE-2025-14847 aka MongoBleed
Exp: https://github.com/joe-desimone/mongobleed/blob/main/mongobleed.py
This one is incredibly widely internet facing and will very likely see mass exploitation and impactful incidents
Impacts every MongoDB version going back a decade.
Shodan dork: product:"MongoDB"
Graham Sutherland / Polynomial
gsuberland@chaos.social@GossiTheDog oh for fuck's sake, what an asshole time to drop that one
Kevin Beaumont
GossiTheDog@cyberplace.socialThe exploit is real and works, you can just run it and target specific offsets and/or keep running it until you get AWS secrets and such.
Alan Miller  🇺🇦
🇺🇦
fencepost@infosec.exchange
@GossiTheDog crappy timing but looks like it was a bit earlier than that. https://jira.mongodb.org/browse/SERVER-115508
Kevin Beaumont
GossiTheDog@cyberplace.socialI did a quick write up: https://doublepulsar.com/merry-christmas-day-have-a-mongodb-security-incident-9537f54289eb
buherator
buherator@GossiTheDog .oO( Surely nobody exposes mongodb towards the inter-| OMGWTFBBQsrsly?
T1- Push The Button
Just_Patch_It@cyberplace.social@GossiTheDog who the fuck exposes a DB directly to the internet?
raspberryswirl
raspberryswirl@chaos.social@nblr @GossiTheDog ofc not, I bet on aistartups and governments :3
All information should be FREE!
Except the personal one ;-)
icco
icco@merveilles.town@GossiTheDog https://www.mongodb.com/community/forums/t/important-mongodb-patch-available/332977 all of mongodbs hosted servers are patched for folks running on atlas.
Jonathan Kamens 86 47
jik@federate.social@GossiTheDog I am having a bit of trouble getting worked up about this.
The bug went public six days before Christmas. This means, frankly, that the folks who get paid to be bad actors, of which there are rather many nowadays, have had six days to figure out how to exploit it. I'm sure several of them had already figured it out before the Eclipse dude dropped the exploit.
By making the urgency of patching this issue clear, he has arguably done a public service.
@GossiTheDog Publishing an exploit on Christmas Day and not providing any info on how to detect exploitation is just the most stupid thing for a security vendor to do...
yopp
alex@yopp.me@GossiTheDog it would be great to add note that you don’t have to upgrade right now.
Disabling zlib for network compression in enough to mitigate
Either:
a) Restart mongod/mongos with option --networkMessageCompressors=snappy,zstd
(omit zstd on 3.6 and 4.0)
b) Disable in mongod.conf and restart
net:
compression:
# (omit `zstd` on 3.6 and 4.0)
compressors: snappy,zstd
And then plan upgrade after holidays
HD Moore
hdm@infosec.exchange@GossiTheDog doesn't seem far to blame the PoC author? the exploit trigger was in the original diff as a unit test
HD Moore
hdm@infosec.exchange@gsuberland @GossiTheDog the exploit was included as a unit test in the original patch, wiring that into a python script isn't slowing down attackers (but surely made the defenders take notice)
Drew Scott Daniels
drewdaniels@mastodon.online@GossiTheDog https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-14847 is a 404. I guess they assign a different CVE if one of their products based on MongoDB is affected?
Kevin Beaumont
GossiTheDog@cyberplace.socialThere’s a great blog on detecting MongoBleed exploitation via Velociraptor https://blog.ecapuano.com/p/hunting-mongobleed-cve-2025-14847
Kevin Beaumont
GossiTheDog@cyberplace.socialI set up a honeypot for MongoBleed on a legit MongoDB instance, yolo and all that.
Cassandrich
dalias@hachyderm.io@alex @GossiTheDog Thank you. This is how all vuln announcements should look. Simple instructions for disabling the vector.
Kevin Beaumont
GossiTheDog@cyberplace.socialJust checked in on my MongoDB honeypot, it's had a few hundred MongoBleed attempts from 7 IPs so far.
Kevin Beaumont
GossiTheDog@cyberplace.socialOne of the IPs in the honeypot is a ransomware/extortion group, they are blasting the internet. I have a capture of the traffic, it's an exact match to the mongobleed.py exploit by joe (it doesn't match a normal connect as it's invalidly formatted session).
DJGummikuh
DJGummikuh@mastodon.social@GossiTheDog I am sincerely surprised you can trace back an IP to a ransomware group, I'd expect them to be more careful to protect their Identity when trying out a new exploit. I mean, essentially they're giving away their game, especially when they are iterating, since their IPs are (as can be seen) scrutinized more than other's
VessOnSecurity
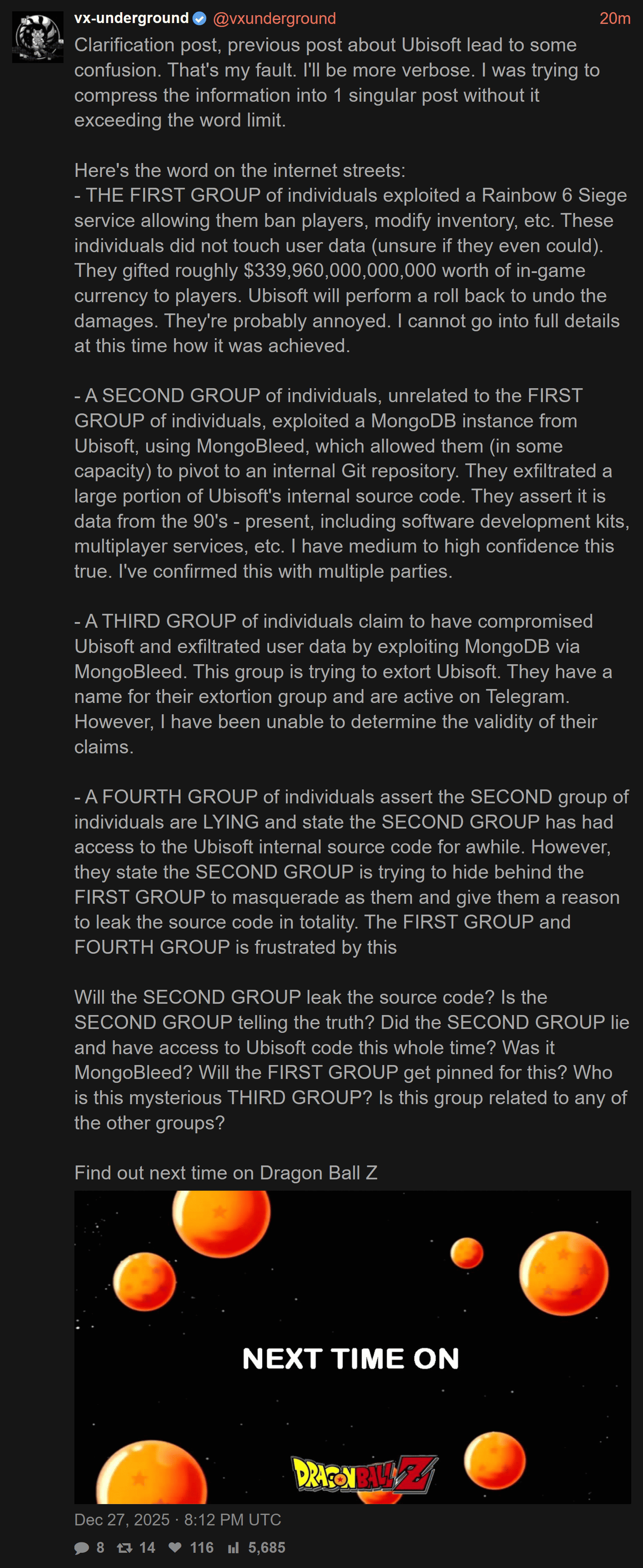
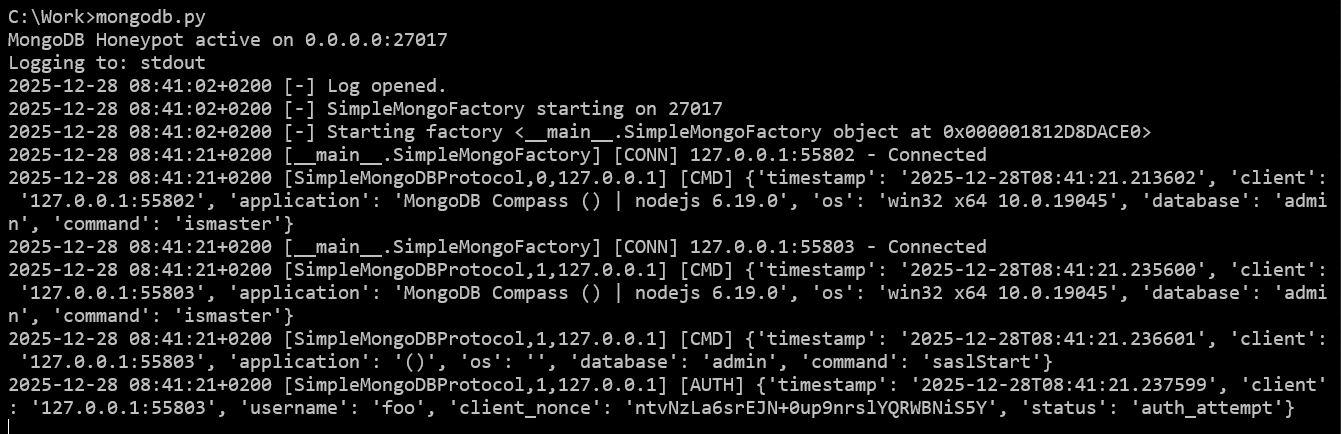
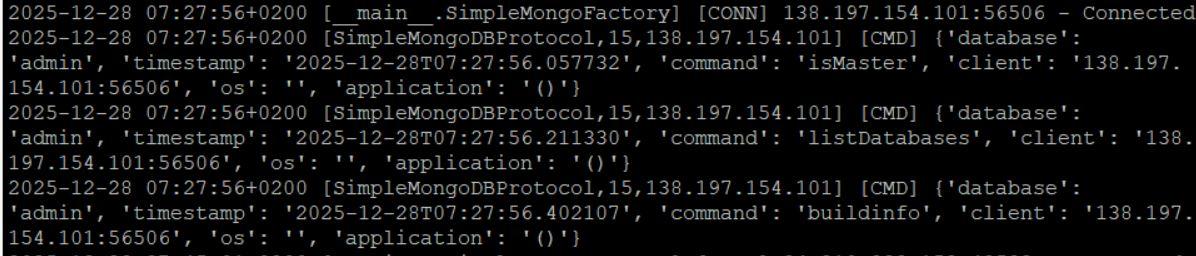
bontchev@infosec.exchange@GossiTheDog None here. (If I understand correctly, using the exploit would generate many connections and nothing else.) Not even authentication attempts. Just a few IPs running commands (buildinfo, listDatabases, ismaster, etc.) without prior authentication.
They seem to be looking for databases exposed to the Internet and not protected in any way? Unless something's wrong with the honeypot...
VessOnSecurity
bontchev@infosec.exchange@GossiTheDog It simulates the login process of MongoDB 8.0.9, rejecting any credentials the attacker tries.
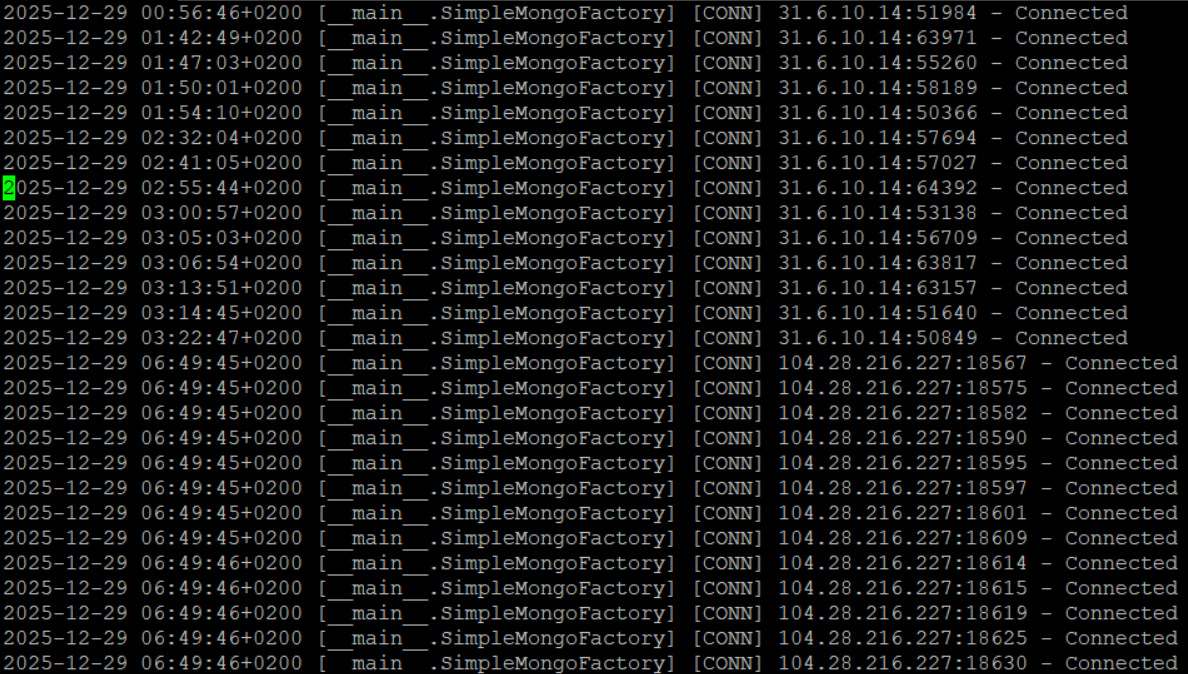
A normal attacker would connect, get information about the login method, then try to authenticate (first image).
Somebody exploiting this vulnerability would try to connect many times and nothing else (second image).
Instead, I am observing the attacker connecting once, then using some commands without attempting to authenticate (third image).
Drew Scott Daniels
drewdaniels@mastodon.online@GossiTheDog any advice if I find any publicly exposed Azure managed MongoDB databases like cosmos db? I asked support (went to a 3rd party v- address), and they’re doing the usual delay stuff, asking for information they don’t need.
Kevin Beaumont
GossiTheDog@cyberplace.socialSo @cyb3rops has made a MongoBleed log detection tool https://github.com/Neo23x0/mongobleed-detector
I’ve tried it and it works on a pwned server.
VessOnSecurity
bontchev@infosec.exchange@GossiTheDog Aha! I'm finally getting exploitation attempts at the MongoDB honeypot. Not many, though (only these 2) - yet it's been up for 2 days already.
Kevin Beaumont
GossiTheDog@cyberplace.socialA Christmas lesson:
Cyber people probably shouldn't post full chain exploits which automate stealing secrets on Christmas Day for new vulns in direct competitor products.
I mean, people can post whatever they want.. it would just be nice to have a holiday with family and all, rather than arming teenagers.
VessOnSecurity
bontchev@infosec.exchange@kevred @GossiTheDog Maxim #13. Full stop at the end, not elipsis.
https://schlockmercenary.fandom.com/wiki/The_Seventy_Maxims_of_Maximally_Effective_Mercenaries
Kevin Beaumont
GossiTheDog@cyberplace.socialMongoBleed’s been added to CISA KEV. https://mastodon.social/@cisakevtracker/115804868181877648
Kevin Beaumont
GossiTheDog@cyberplace.socialIf anybody is wondering on honeypot activity, lots.
More worrying is the real world incidents, two at large orgs I know of so far where attackers have gained access to internal DevOps systems using stolen creds used on MongoDB systems. In both cases it’s Advanced Persistent Teenagers.
VessOnSecurity
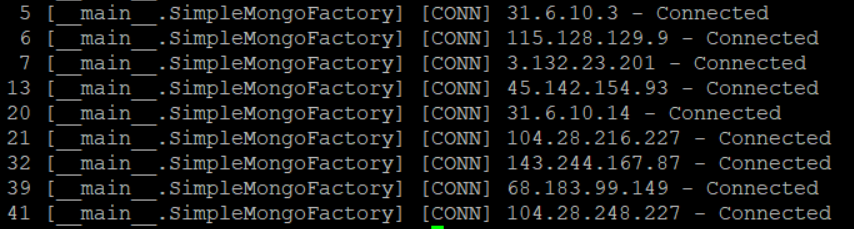
bontchev@infosec.exchange@GossiTheDog Only 9 attempts observed by my honeypot so far, with one of them giving up after only 5 consecutive connections (another tried 41 times - the maximum so far):
Kevin Beaumont
GossiTheDog@cyberplace.socialMongoDB have a blog out about #MongoBleed
Notably:
- Internal find at MongoDB
- they notified customers of the issue and patch availability on December 23rd
- A security vendor published technical details on December 24th, Christmas Eve
- Somebody at Elastic, a direct competitor, published an exploit with full secret extraction feature on December 25th, Christmas Day
That was an impossible situation for orgs - the security industry poured fire on them and set their own customers on fire.
Arazil
arazil@elvenstar.cafe@GossiTheDog With security vendors like that, who needs enemies? 🙄 
Marius (windsheep)
windsheep@infosec.exchange@GossiTheDog If this is internal, why were they unable to wait until mid January?
Matt Palmer
womble@infosec.exchange@GossiTheDog I feel like there's enough data on what happens as soon as a patch drops, from what has happened every previous time, that the consequences of Mongo dropping a patch on the 23rd were pretty easy to predict.
Skjie
Skjie@infosec.exchange@GossiTheDog @windsheep so it's their first day on the internet then? This was extremely predictable, and both Mongodb and elastic look very poorly.
Matt Palmer
womble@infosec.exchange@GossiTheDog that seems like a very difficult claim to prove - CVEs don't usually come with sufficient information to be able to detect exploitation at a distance.
In any event, the vast majority of CVEs don't have this degree of impact and ease of exploitation. The moment that this kind of vuln - pre-auth information disclosure - is known to exist, it's basically inevitable that many actors, for a variety of reasons, will seek to develop an exploit for it.
I love this, so I
jpm@aus.social@GossiTheDog and this right here is why I left IT security - security vendors dropping trou and taking a massive steaming shit on their competitors products while screaming LOOK AT ME IM DOING A SECURITY!!!
RootWyrm 🇺🇦
rootwyrm@weird.autos
> Somebody at Elastic, a direct competitor, published an exploit with full secret extraction feature on December 25th, Christmas Day
Which means if you're doing business with Elastic, you're doing business with someone who will intentionally and deliberately risk or outright destroy their own customers for completely imagined gains.
But as we have seen, having anything resembling ethics, morals, or a conscience is treated as a 'weakness.'
Fennix
fennix@infosec.spaceFrom firsthand knowledge as an internal pentester whose team published > 2000 CVEs over about a decade or so, every single vulnerability we reported had an exploit but were never published.
Published is really what matters here. From details like "XSS in >software<" it's not really obvious or likely to become a working exploit 90% of the time unless someone is highly motivated. Especially factoring in the break they probably figured nobody would be that much of an asshole even if they did figure it out.
RootWyrm 🇺🇦
rootwyrm@weird.autos
@badsamurai @GossiTheDog and hey! Why are we not surprised that he's only active on the site that protects Nazis (but pretends not to promote them!)
If I was an Elastic customer, my sales rep would've gotten a 1AM call from the lawyers demanding a very large settlement to cover costs of responding to a security incident they INTENTIONALLY caused, along with notice that the breach of contract suit will be right behind it.
B'ad Samurai 🐐🇺🇦
badsamurai@infosec.exchangeHah! And their sales will ignore you in the same key stroke they post what Mongo Bleed2Bleed sales taught them with creepy holiday pictures of their Ar*an family on LinkedIn.
@nieldk @GossiTheDog no reason to have posted that in such detail on Xmas eve. Other than wanting to be first.
MongoDB had no choice but to release patch ASAP but Ox and _Dez should have waited given the time of year