Viss
Viss@mastodon.social@cR0w @neurovagrant @hrbrmstr is wsus just 'on by default' on windows server? or is it something you have to enable first so that it can be exploited over the internet?
αxel simon ↙︎↙︎↙︎
axx@mstdn.fr@neurovagrant Someone at an APT nearby is having a bad day.
There goes that reliable exploit they've used to coast through their career for the past 13 years!
Viss
Viss@mastodon.social@neurovagrant @cR0w @hrbrmstr i just went and piddled. looks like if a windows box has 8530/8531 open and that is in fact wsus, then its game on
B'ad Samurai 🐐🇺🇦
badsamurai@infosec.exchange@neurovagrant @Viss @cR0w @hrbrmstr
Good thing no one is using WSUS anymore right. R I G H T?
Mark Koek
mkoek@mastodon.nl@Viss @cR0w @neurovagrant @hrbrmstr Not on by default if I rtfa correctly. But I do love critical vulns in services I’ve recommended to a gazillion clients over the years…
Viss
Viss@mastodon.social@badsamurai @neurovagrant @cR0w @hrbrmstr well its not like, insane..
Viss
Viss@mastodon.social@neurovagrant @mkoek @cR0w @hrbrmstr thisll be one of those privesc kinda deals huh
Viss
Viss@mastodon.social@neurovagrant @mkoek @cR0w @hrbrmstr i wonder if someone non admin can twiddle windows server to enable wsus, then exploit it to get system
buherator
buheratorFritz Adalis
FritzAdalis@infosec.exchange@Viss @badsamurai @neurovagrant @cR0w @hrbrmstr
Oh it's only vulnerable if 8530/8531 is exposed? That'll help.
Viss
Viss@mastodon.social@FritzAdalis @badsamurai @neurovagrant @cR0w @hrbrmstr looks like wsus is just a webapp that runs as system under iis on a funny port
Mark Koek
mkoek@mastodon.nl@Viss @neurovagrant @cR0w @hrbrmstr apparently a lot of these ports are open, even on the internet :(
Mark Koek
mkoek@mastodon.nl@neurovagrant @Viss @cR0w @hrbrmstr no need, you can push malicious updates to the rest of the network from that box
Viss
Viss@mastodon.social@mkoek @neurovagrant @cR0w @hrbrmstr yup, once you own wsus, you own the thing that pushes the updates
Fritz Adalis
FritzAdalis@infosec.exchange@Viss @badsamurai @neurovagrant @cR0w @hrbrmstr
More or less, yeah. Thanks!
Viss
Viss@mastodon.social@mkoek @neurovagrant @cR0w @hrbrmstr if you didnt have domain admin by then, you DEFINITELY DO NOW
Maxime Thiebaut
0xThiebaut@infosec.exchange@Viss @badsamurai @neurovagrant @cR0w @hrbrmstr 30 honeypots go brrrr
Viss
Viss@mastodon.social@0xThiebaut @badsamurai @neurovagrant @cR0w @hrbrmstr heh, 900,000 of em gonna spin up today too, surely
hrbrmstr 🇺🇦 🇬🇱 🇨🇦
hrbrmstr@mastodon.social@neurovagrant @mkoek @Viss @cR0w We just modified a sensor profile to expose WSUS in various locales. Will keep y'all posted.
Viss
Viss@mastodon.social@hrbrmstr @neurovagrant @mkoek @cR0w where did i leave that threatbutt log script...
Viss
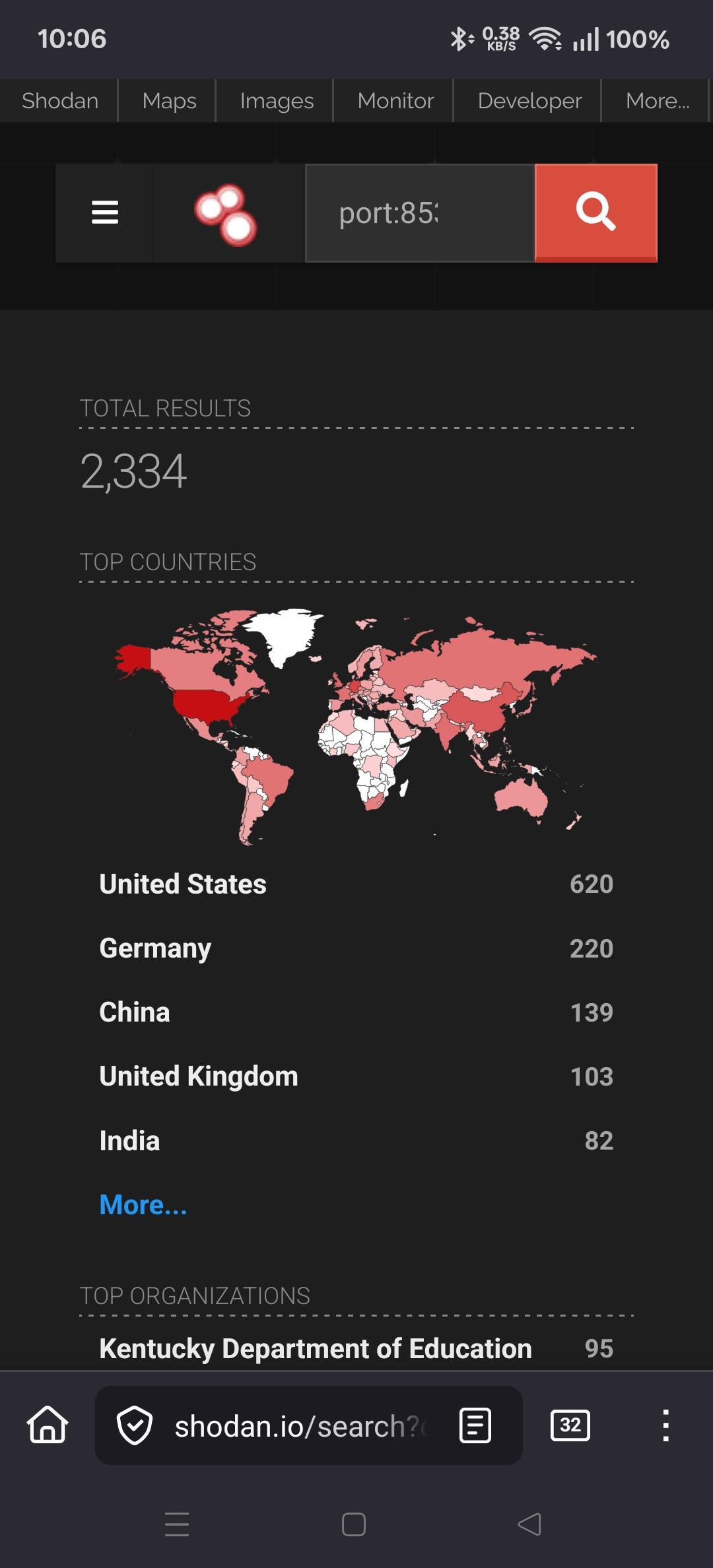
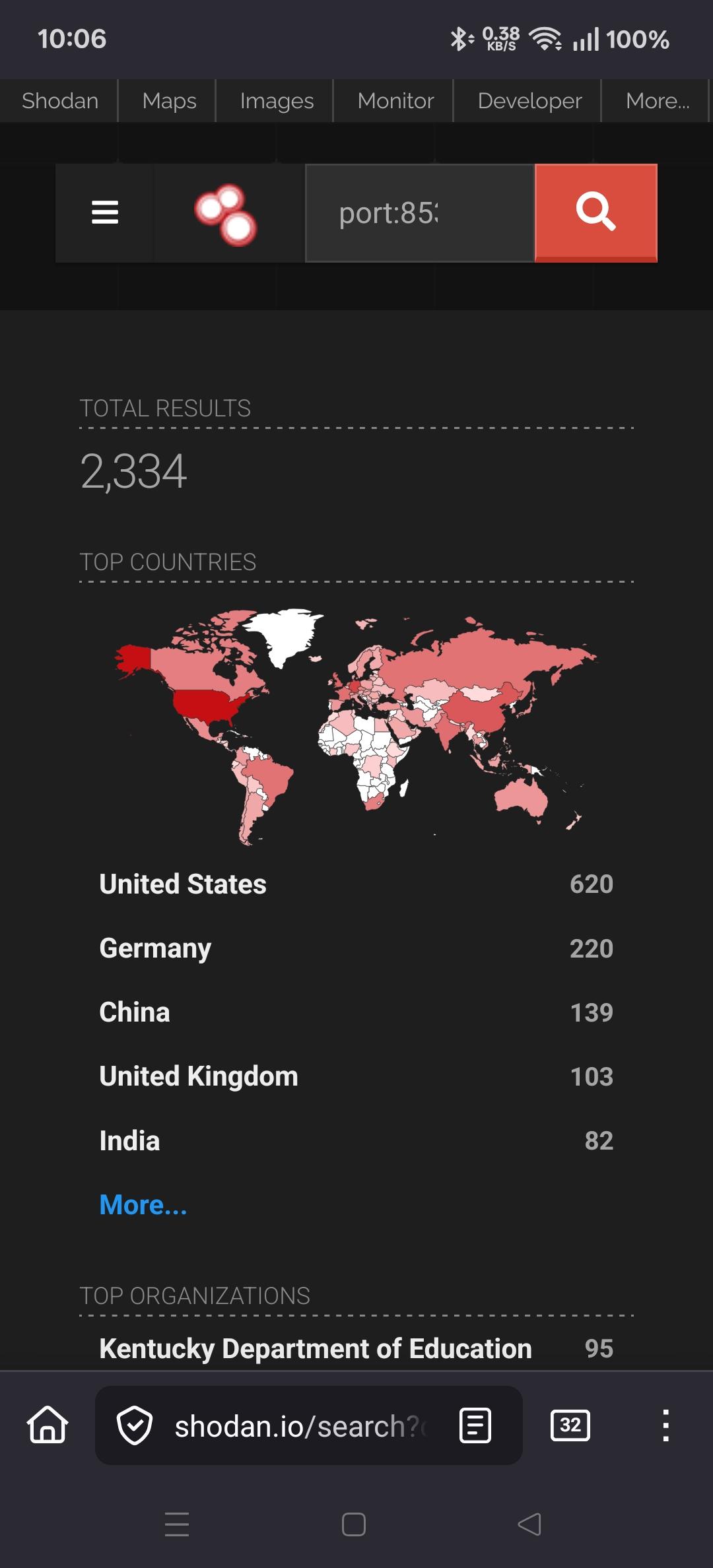
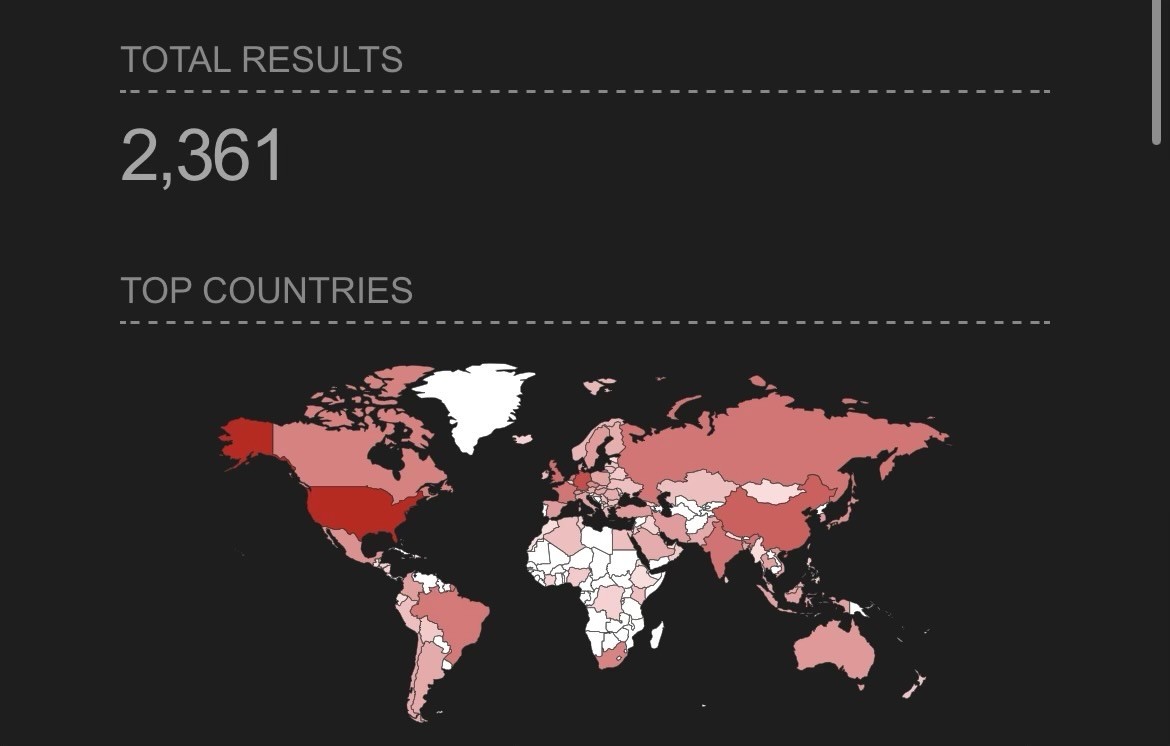
Viss@mastodon.social@neurovagrant @hrbrmstr @mkoek @cR0w @0xThiebaut eh, shodan doesnt show many directly exposed, but i bet therell be malware that suddenly starts scanning lans for 8350
Viss
Viss@mastodon.social@neurovagrant @hrbrmstr @mkoek @cR0w @0xThiebaut its amazing how well 'the fucked up shit isnt on by default' helps in terms of limiting blast radius
WinterKnight 
winterknight1337@infosec.exchange
@neurovagrant @Viss @mkoek @cR0w @hrbrmstr
Man I wish I was on an internal op this week 😭
Viss
Viss@mastodon.social@winterknight1337 @neurovagrant @mkoek @cR0w @hrbrmstr theres a chance i may be able to use this before it gets fully patched out, but it would mean someone suddenly got REAL EXCITED about signing a gig
Aprazeth has moved
aprazeth@mastodon.social@Viss @FritzAdalis @badsamurai @neurovagrant @cR0w @hrbrmstr correct, not installed by default (but easy to do) It also came/comes with a MSDE install in case you didn't have a SQL server
Also, self-signed certificates - if at all.
... Ugh, so many memories coming back having to install and operate it on SBS (Small Business Server) amongst other places
nyanbinary
nyanbinary@infosec.exchange@cR0w @neurovagrant @hrbrmstr @mkoek @Viss @0xThiebaut just give me the password, I'll do it for you 
Aprazeth has moved
aprazeth@mastodon.social@Viss @FritzAdalis @badsamurai @neurovagrant @cR0w @hrbrmstr sorry, but I just remembered something: doesn't/didn't SCCM also use or cannibalise WSUS for its update distribution points? If so, wouldn't those also be affected? 
And the reporting/collection servers (I forgot what they were exactly called but basically the servers you could designate as the ones receiving the telemetry back - so you could split that and the actual distribution across servers)
Fritz Adalis
FritzAdalis@infosec.exchangeAprazeth has moved
aprazeth@mastodon.social@Viss @FritzAdalis @badsamurai @neurovagrant @cR0w @hrbrmstr Ah, I remembered correctly:
"When you use a software update point on a server other than the site server, install the WSUS Administration Console on the site server."
Might be of interest to confirm if the spicy stuff also works on those servers
K, I'll shut up now :)
Fritz Adalis
FritzAdalis@infosec.exchange@aprazeth @Viss @badsamurai @neurovagrant @cR0w @hrbrmstr
The admin console is just an MMC, so probably not.
B'ad Samurai 🐐🇺🇦
badsamurai@infosec.exchangeGood thing everyone has 100% deployment of 802.1x, right? R I G H T?
Viss
Viss@mastodon.social@badsamurai @aprazeth @FritzAdalis @neurovagrant @cR0w @hrbrmstr
i've been doing this shit a very long time
and the thing i can tell you with great certainty is:
the people who read logs
and the people who ignore logs
are great ways to define 'how an org do'. You typically do not need to look further than that to understand their security chops
Viss
Viss@mastodon.social@neurovagrant @badsamurai @aprazeth @FritzAdalis @cR0w @hrbrmstr ive had literally people swear at me in the past because i have a habit of ctail -f /var/log/apache2/*log
Viss
Viss@mastodon.social@neurovagrant @badsamurai @aprazeth @FritzAdalis @cR0w @hrbrmstr also if you dont know about ctail yet, i highly recommend
Fritz Adalis
FritzAdalis@infosec.exchange@Viss @neurovagrant @badsamurai @aprazeth @cR0w @hrbrmstr
Multitail is also good. I used to use it for sendmail logs.
Fritz Adalis
FritzAdalis@infosec.exchange@Viss @badsamurai @aprazeth @neurovagrant @cR0w @hrbrmstr
It's also fun when it dawns on someone that they should be reading logs.
B'ad Samurai 🐐🇺🇦
badsamurai@infosec.exchangeSamesies. But we need a worst log contest. This one I used to parse for fleet telematics combined syslog, json and XML into the same file. ¿Por qué?
cakepop demon hunter
h2onolan@infosec.exchange@neurovagrant
I would make a little nest of syslog to nap in, if i could
Viss
Viss@mastodon.social@neurovagrant @h2onolan its absolutely fucking bonkers to me that people pay for shit like splunk first without even considering a centralized syslog server with some kinda opensource gui to process stuff
cakepop demon hunter
h2onolan@infosec.exchangeNerdfession: i run a vps with elastic for the sole purpose of pointing random shit at it and inspecting log entries.
Viss
Viss@mastodon.social@h2onolan @neurovagrant
[fumbles to setup a troll syslog client to squirt bullshit across the internet]
Viss
Viss@mastodon.social@neurovagrant @h2onolan heh, youd think the solutions that are straightforward, with copious documentation and a community surrounding them would be the things folks go for, citing things like "operational and business continuity" and "transferability", but no - they go with sap and some custom oracle bullshit that two guys know, who you keep finding in pro-nazi forum dump/leaks
Viss
Viss@mastodon.social@neurovagrant @h2onolan @cR0w @catsalad
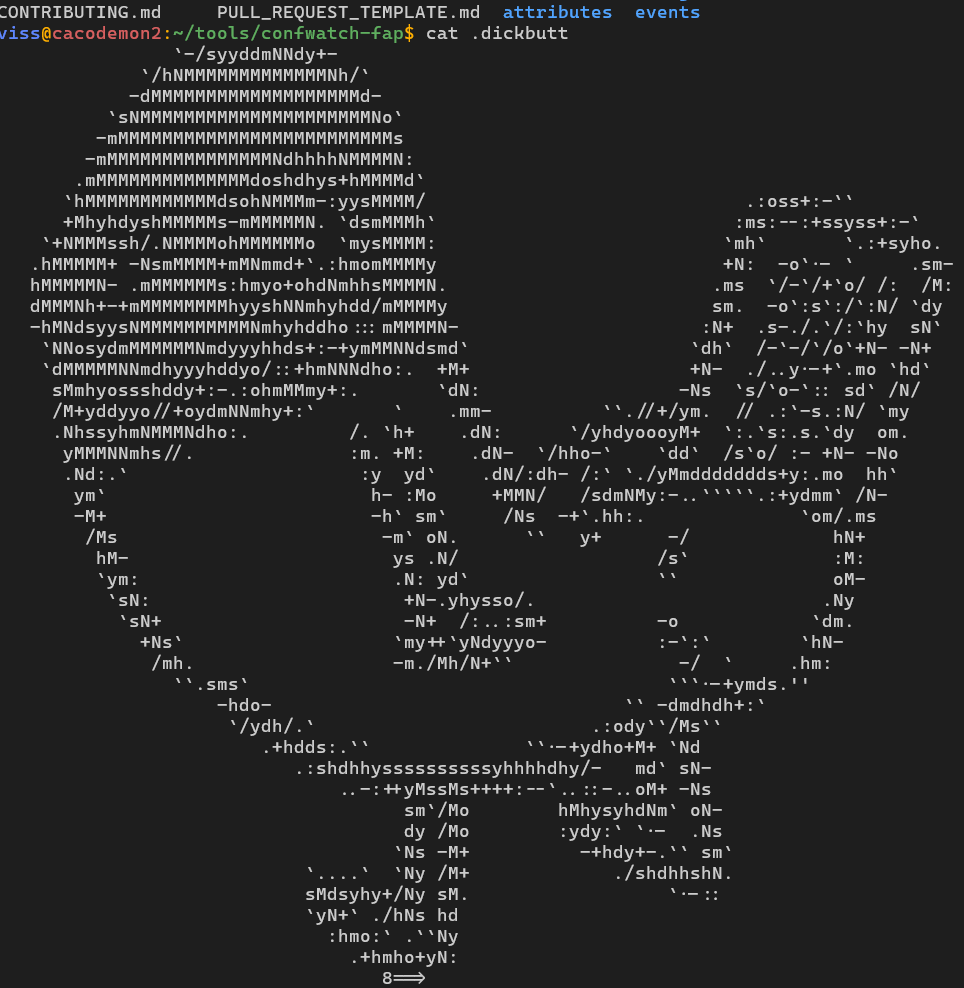
goddammit. i need to go fetch that logpush thing i wrote when i pushed threatbutt ascii art into @da_667's logs a few years ago.
cakepop demon hunter
h2onolan@infosec.exchange@Viss @neurovagrant @cR0w @catsalad @da_667 glory!
Viss
Viss@mastodon.social@h2onolan @neurovagrant @cR0w @catsalad @da_667 okay. well..
i found the ascii art .. but not the script. so i guess im writing some kinda wrapper to take stuff like this and schlorp it into logs and be able to parse whitespace correctly...
(i have no idea wtf that path is. i dunno why its there. this is super weird. wtf, past me, were you thinking?)