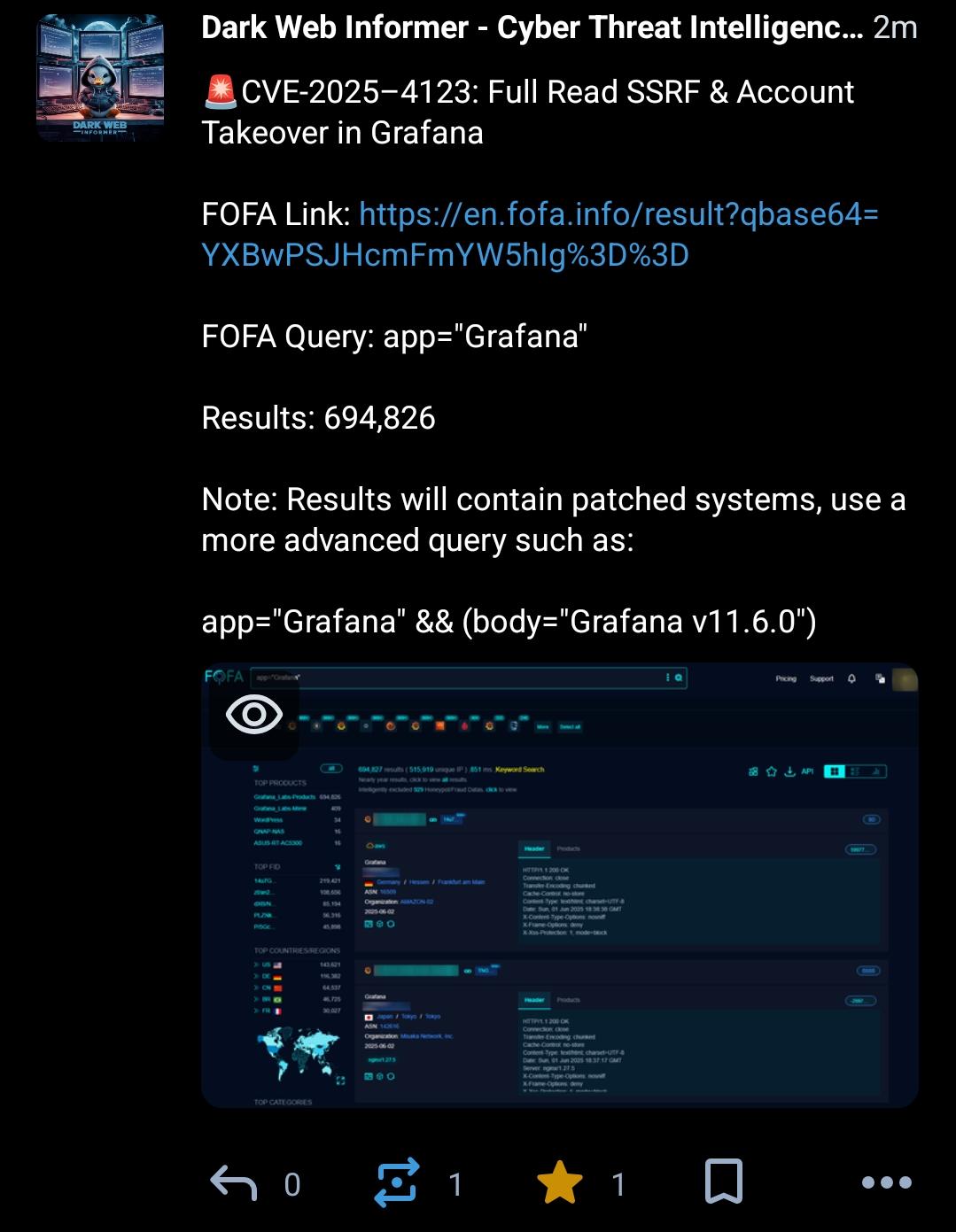
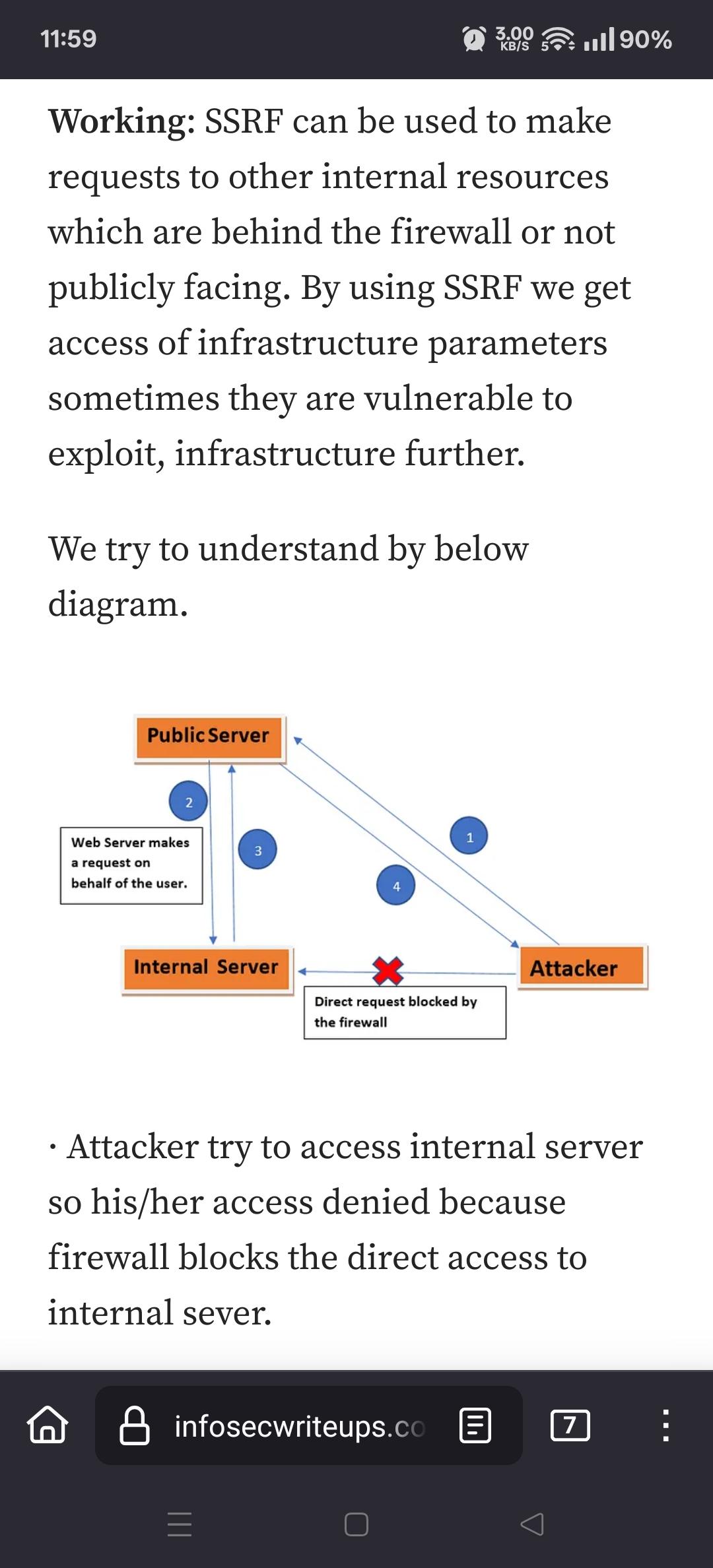
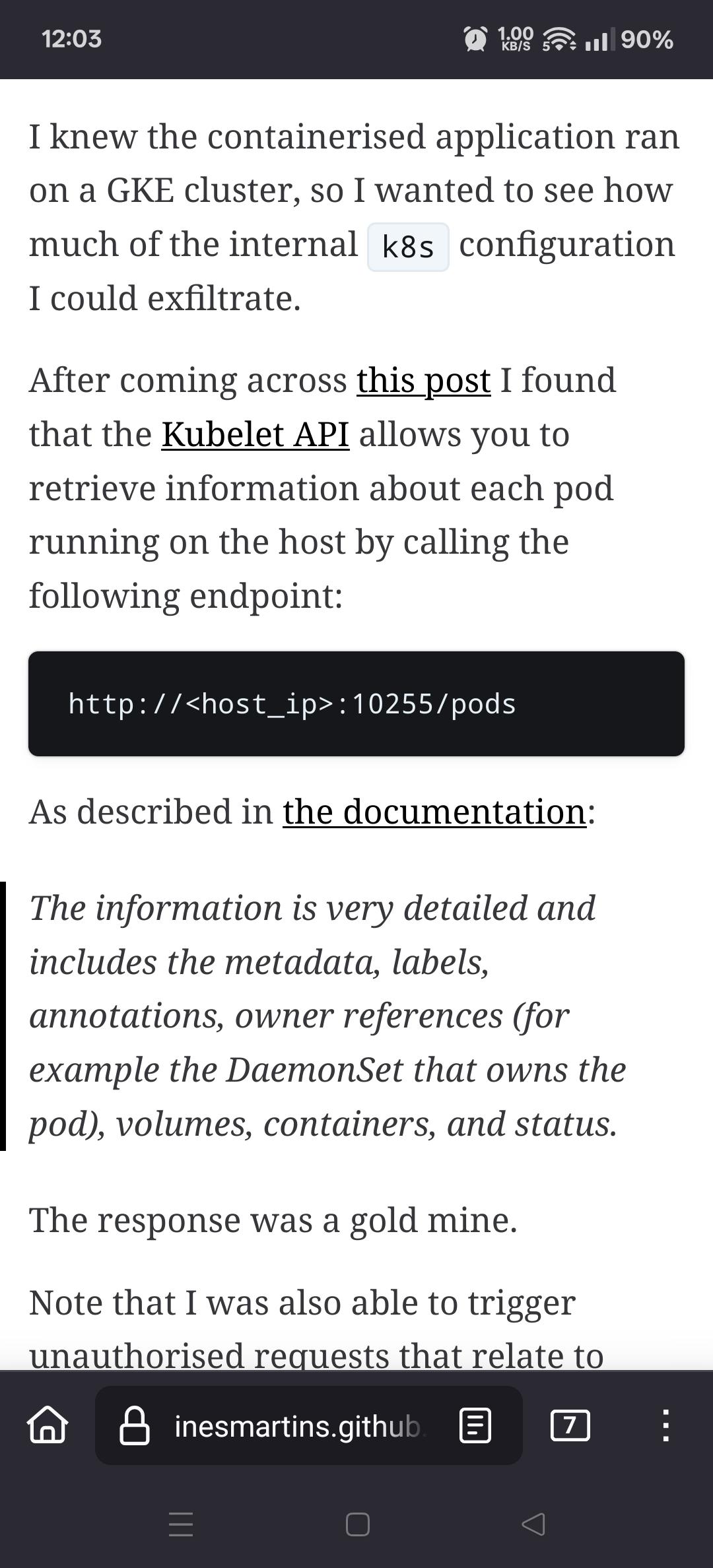
Viss
Viss@mastodon.socialshare this with your favorite pro-cloud, k8s loving, docker fanatics who openly condescend to sysadmins and security people, boasting about how they never need to do networking, sysadmin or security because they think someone else does it all for them
do not remind them that all those precious env vars in their k8s cluster that would give an attacker full control of everything are sitting in the container hosting grafana, and because they hate networking and firewalls, this is all public
buherator
buheratorschrotthaufen
schrotthaufen@mastodon.socialViss
Viss@mastodon.social@schrotthaufen @cR0w the ones ive found are either public/noauth or some kinda shared admin cred. but if you can read env vars out of the container its better than coin toss odds you can take over the whole cluster.
Viss
Viss@mastodon.social@cR0w @schrotthaufen this cve is a gateway, a one-shot silver bullet to an entire k8s cluster takeover.