Conversation
Juanma Fernandez
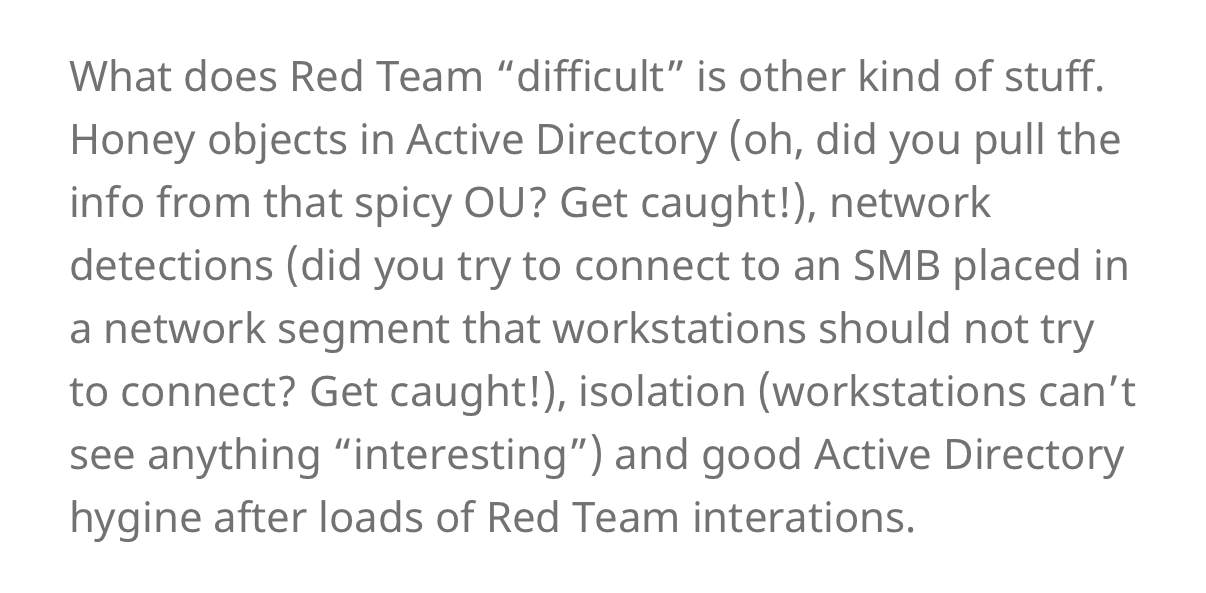
XC3LL@mastodon.socialA small rant:
The State of Art in Red Team is whatever you want to believe
buherator
buherator
@XC3LL Thanks for posting this, great to see someone has the guts to say the emperor is naked!
My 2c:
- Red Teams should be about the "difficult" things you mention at the end IMO. Spending resources on initial access is mostly pointless (from the client's perspective, finding 0d is always cool ofc) when a new blinky box exploit, leaked code signing cert, etc. is popping up every other week. IME many clients pay for (bad) initial access simulations because organizing assumed breach in-house is hard.
- A way to burst the bubbles you describe is to mandate scenarios based on real-world threat intel. But this works against intial access again, because RT's can't scale their R&D as black hats do (attack surface is clients vs the Internet).
My 2c:
- Red Teams should be about the "difficult" things you mention at the end IMO. Spending resources on initial access is mostly pointless (from the client's perspective, finding 0d is always cool ofc) when a new blinky box exploit, leaked code signing cert, etc. is popping up every other week. IME many clients pay for (bad) initial access simulations because organizing assumed breach in-house is hard.
- A way to burst the bubbles you describe is to mandate scenarios based on real-world threat intel. But this works against intial access again, because RT's can't scale their R&D as black hats do (attack surface is clients vs the Internet).
bakachu
bakachu@infosec.exchange@XC3LL i agree with your sentiments completely, and feel that it’s only getting worse. the ‘assume breach’ mode that regulatory testing likes means that tests can flail around phishing for a token amount of time and almost certainly fail, then get let in and destroy the org but management still gets to say “the perimeter is flawless keep on not caring about security”
Jake Hildreth (acorn) 
horse@infosec.exchange
@XC3LL as an assessor, I am going to slap every customer with this screenshot when they push back against recommendations.