Posts
2472Following
662Followers
1487Clément Labro
itm4n@infosec.exchangeInterestingly enough, MS disabled the "Use my Windows user account" checkbox when connecting to Wi-Fi on the lock screen to address CVE-2024-38143 in the August Patch Tuesday.
This change completely remediates the "Airstrike" attack as well. 🤯
buherator
buheratorI guess I have to change my lifestyle a bit if I want to know the details...
(or hack some gov DB, which I would never ever do ofc!)
DNA Lounge Update, Wherein we negotiate with the mob
https://www.dnalounge.com/backstage/log/2024/12/03.html
The V Programming Language
vlang@mas.toThe Advent of Code for V has started, uncovering a new challenge every day! Check them out!
The V Programming Language
vlang@mas.toUnused functions are now skipped by default. This reduces generated C dramatically. Give it a try! if you have issues, use v -no-skip-unused ... and report them.
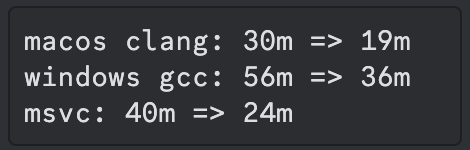
After making this option by default, CI times went down significantly:
Seth Larson
sethmlarson@fosstodon.orgI've noticed a concerning trend of "slop security reports" being sent to open source projects. Here are thoughts about what platforms, reporters, and maintainers can do to push back:
https://sethmlarson.dev/slop-security-reports?utm_campaign=mastodon
buherator
buheratorhttps://www.mdsec.co.uk/2024/12/extracting-account-connectivity-credentials-accs-from-symantec-management-agent-aka-altiris/
kajer
kajer@infosec.exchangeFucking PaloAltoNetworks...
two major CVEs come out, guidance says X version is fine and unaffected. I upgrade everything to that version.
PaloAlto then changes the CVE details to say that ""LOL version Y is good, X sucks.""
I don't want to have to keep checking CVE pages for changes.... 
screaminggoat
screaminggoat@infosec.exchangeCISA: CISA Adds Three Known Exploited Vulnerabilities to Catalog
Hot off the press!
- CVE-2024-11667 (7.5 high) Zyxel Multiple Firewalls Path Traversal Vulnerability
- CVE-2024-11680 (9.8 critical) ProjectSend Improper Authentication Vulnerability
- CVE-2023-45727 (7.5 high) North Grid Proself Improper Restriction of XML External Entity (XEE) Reference Vulnerability
#CVE #CVE_2024_11667 #Zyxel #ProjectSend #CVE_2024_11680 #proself #CVE_2023_45727 #cisa #kev #cisakev #knownexploitedvulnerabilitiescatalog #vulnerability #eitw #activeexploitation #infosec #cybersecurity
Advanced Fuzzing League
aflplusplus@infosec.exchangeWe just released AFL++ v4.30c - deprecate afl-gcc/clang, fast resume support, lots of improvements. https://github.com/AFLplusplus/AFLplusplus/releases/tag/v4.30c #afl #fuzzer #fuzzing
Fesshole 🧻
fesshole@mastodon.socialI work in IT and hate friends/family asking me to fix their home computers, now everytime I fix someones computer and hand it back I whisper "Dirty bastard!" and the look of pure horror on their face gets me everytime. Nobody asks now so it worked a treat.
Michael Schneider
misc@infosec.exchangeMy team college @rame found the CVE-2024-8001 vulnerability in VIWIS LMS 9.11. Congrats! 🥳 https://vuldb.com/?id.284352
BOFH Excuses
bofh_excuses@botsin.space#BOFH excuse #281:
The co-locator cannot verify the frame-relay gateway to the ISDN server.
cryptax
cryptax@mastodon.socialOne thing I find difficult in Radare2 is its advanced syntax. Not sure where it's documented + the naming logic.
For example: db $in:5 @ main - in yesterday's Advent of Radare (https://radare.org/advent/02.html). Where does $in come from?
Or ?$? ... ouch!
Or $$+10
or @10!20
or @@10 ...
Any good pointers to read?
cc: @radareorg
buherator
buheratorhttps://github.com/AFLplusplus/LibAFL/releases/tag/0.14.1
#frombsky
Alex Plaskett
alexjplaskett@bird.makeupAMD Disables Zen 4's Loop Buffer
https://chipsandcheese.com/p/amd-disables-zen-4s-loop-buffer
bert hubert 🇺🇦🇪🇺🇺🇦
bert_hubert@fosstodon.orgIn an interview with the BBC in 2021, the British head of intelligence, Sir Richard Moore, MI6, describes the dangers of digital dependencies. The Foreign Intelligence Service speaks of a “data trap”: “If you allow another country to gain access to really critical data about your society, it will over time undermine your sovereignty, as you no longer have control over this data.” - https://gi.de/themen/beitrag/alarmzeichen-deutschland-demnaechst-im-goldenen-microsoft-kaefig
buherator
buheratorhttps://devblogs.microsoft.com/oldnewthing/20241202-00/?p=110595