Posts
2510Following
649Followers
1466HyperDbg
hyperdbg@infosec.exchangeHappy to announce @hyperdbg v0.10! 🎉🎊✨
This version comes with numerous bug fixes and stability improvements, plus new features like running assembly code directly in the events (VMX root-mode) and two new commands.
Check out the latest version: https://github.com/HyperDbg/HyperDbg/releases
For more information,
Assembly codes in conditions:
- https://docs.hyperdbg.org/using-hyperdbg/prerequisites/how-to-create-a-condition
Assembly codes in code sections:
- https://docs.hyperdbg.org/using-hyperdbg/prerequisites/how-to-create-an-action
Assemble virtual address:
- https://docs.hyperdbg.org/commands/debugging-commands/a
Assemble physical address:
- https://docs.hyperdbg.org/commands/extension-commands/a
buherator
buherator
cynicalsecurity 
cynicalsecurity@bsd.network
On the  there is a narrative whereby a Cobalt Strike¹ update "forced" #CrowdStrike to push out an update which caused the Falcon crash² .
there is a narrative whereby a Cobalt Strike¹ update "forced" #CrowdStrike to push out an update which caused the Falcon crash² .
Inevitably the usual crowd came out and we have statements such as:
> So, it’s Cobalt Strike’s success and popularity with threat actors that prompted CrowdStrike to rush out a signature for their agents, resulting in crashes on thousands of systems.
>
> Can someone add this to the balance sheet of damage caused by popular C2 frameworks?³
We therefore justify the complete lack of QA by blaming a C2 framework from a commercial company which, as many others, is used by baddies too.
The best bit is that Florian had to tell people it was said in jest (follow-up xeet) but… too late. He was quoting a xeet by Constantin Raiu but it was taken seriously.
We have just given #CrowdStrike something to blame in their narrative: "we were doing it to save the world from Cobalt Strike, they should not be allowed to exist!"

__
¹ https://www.cobaltstrike.com
² https://x.com/craiu/status/1814566308056318381
³ https://x.com/cyb3rops/status/1814944503498678678
cynicalsecurity 
cynicalsecurity@bsd.network
A #CrowdSstrike offensive summary (update):
* we know Flacon updates are not verified prior to being enabled
* we know that they don't do staged updates
* we know a lot of large customer names
* we know the DR plans (or lack thereof) of said large customers
* we know the systemic reactivity
Learned opinion: it does not look good.
For those involved with the darker side of cybersecurity this is a monstrously useful set of data points.
Dave Anderson
danderson@hachyderm.ioIt's quite funny that in the midst of the crowdstrike thing yesterday, someone tweeted - afaict as a shitpost - that Southwest Airlines were unaffected due to running windows 3.1. Then digitaltrends published that claim using the tweet as a source, and are now being quoted themselves as a source.
AFAICT, it's entirely bollocks. Same with the claim they still run Windows 95, that's from the same lazy digitaltrends article, misquoting another misquote from 2 years ago.
buherator
buheratorI mean, shut up and take my vote?
https://x.com/pmarca/status/1809340920287916286
buherator
buheratorhttps://threadreaderapp.com/thread/1814733681849667734.html
buherator
buheratorhttps://threadreaderapp.com/thread/1814762302337654829.html
buherator
buheratorbuherator
buheratorApp whitelisting and sandboxing (mobile apps, Win S) seem to point in the right direction, but I'd be interested in your take, esp. about if/how the proposed distributed model would help with this.
Nicolas SAPA 
nico@ublog.byme.at
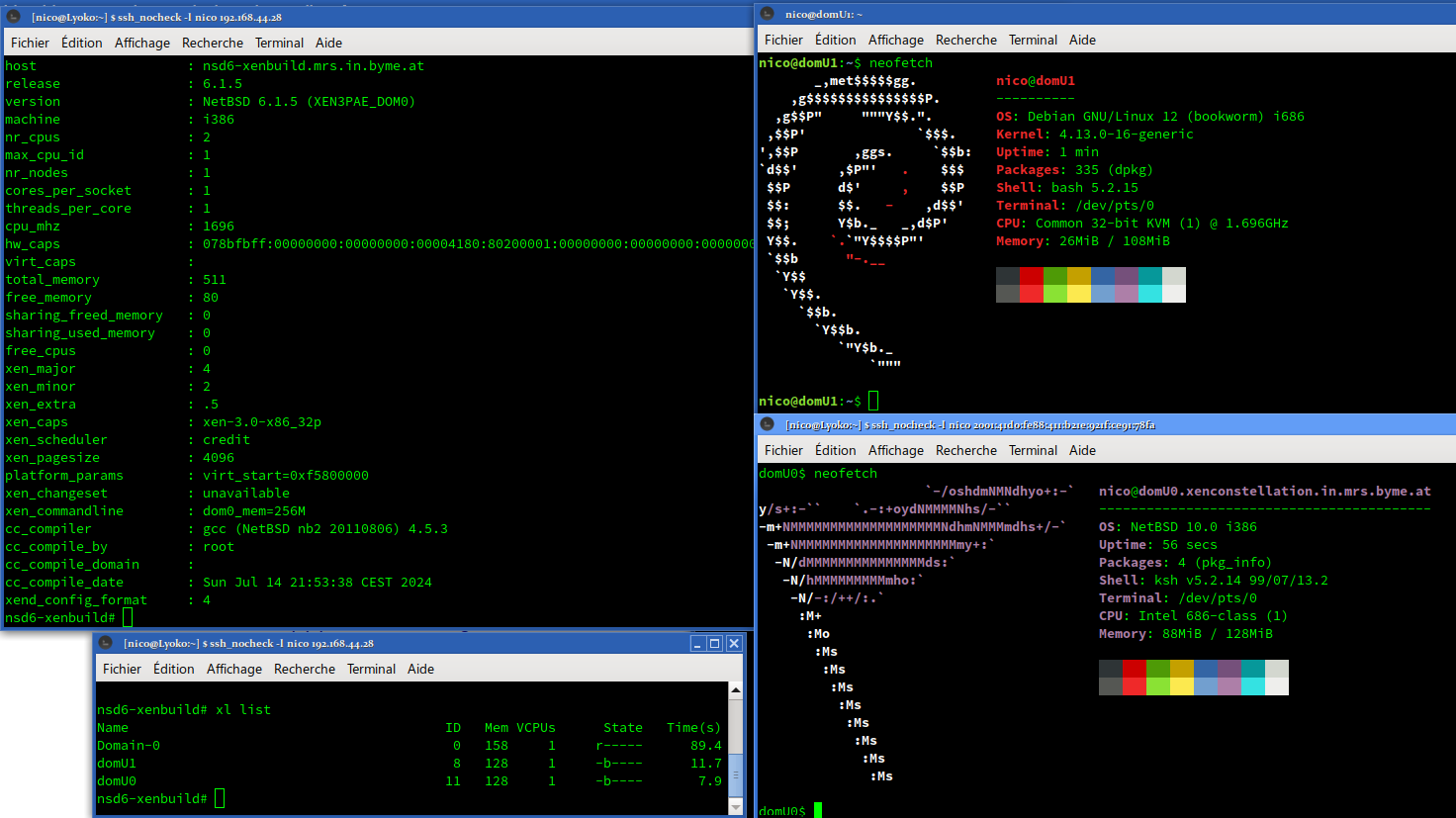
I am able to confirm that #NetBSD 10 and #Linux 4.13 are able to run as domU PV.
The journey was very long:
#pkgsrc 2018Q3 provided a lot of help and sometime tiny annoyances.
I had to build 3 compilers: gcc 4.4, gcc 4.8 and gcc 6.4.
I had to downgrade #ocaml to version 4.00.1, rewriting xentools42 Makefile to use my downgrade and kill xen' ocaml binding (because file not found in pkg install).
I had to force some version of GCC to build some packages - pkgsrc helped there.
Recent version of Linux doesn't seem to boot, the ramdisk/initrd for old Linux is broken, the xm stack seem more broken than the xl stack.
But I was able to run 2 domU PV on i386!
Björkus "No time_t to Die" Dorkus
thephd@pony.socialA lot of people think I'm being sarcastic here, which is fair because I only went toe-to-toe against people on Twitter and didn't do much here, so I'll state my full opinion below anyhow:
I would agree with anyone about not wanting to replace C (or C++). But, C has been alive for 50 years (or just 35 from C89) and Rust has been alive for just barely under 10 (since Rust 1.0). Even if you measure the last 10 years of Rust versus the last 10 years of C or C++, one of these languages is making leaps and bounds ahead in providing people better primitives to do good work.
SafeInt secured pretty much all of Microsoft Office from some of the hardest bugs back in, around, 2005. C++ still lacks safe integer primitives; C only just got 3 functions to do overflow-checked math in C23, after David Svoboda campaigned for years. Rust just... has them baked into the standard library, for all the types you care about, too.
Similarly, people have been having memory issues in C and C++ for a while too. Most of the way to get better has been clamping down on static analysis and doing more testing, but we're still getting these errors. Meanwhile, teams writing Rust have been making way less errors on this in all the openly-published data from corporations like Google, and privately we are hearing a lot more about people taking complex financial and parsing code and turning it into Rust and having a fraction of the issues.
Even if I want to see C doing better, I have to acknowledge we were (a) too slow and not brave enough to do the things that could fix these portions of the language; (b) have fundamental design issues in the language itself that make ownership impossible to integrate as part of the language without breaking a ton of code; (c) do not provide good in-language tools and keep depending on vendors to "do the right thing" (i.e. adding or expanding U.B. and then just saying "vendors will check it" rather than taking responsibility with our language design); (d) are moving monumentally too slow to address the needs of the industry that many people -- especially security people -- have been yelling about since the mid 90s.
As much as I just want to pretend that I can write off every developer with "haha lole skill issue test better sanitize better IDIOT", if the root cause on this bug is "there was some C and/or C++ code that looked nominally correct but did batshit insanity in production", we absolutely will have problems to answer for. This doesn't absolve CrowdStrike for cutting 100s of workers and playing fast and loose, this doesn't excuse the fact that hospitals went down and people likely dead from lack of access to care, this doesn't change that it's abhorrent to have unmitigated hardware access in Ring0 just for a "security product", which has been the trend of every app wanting to plug in its own RootKit-like tool just for the sake of "app security" lately (League, NProtect, School Exam Spyware, etc.). There's a LOT of levels of "what the fuck have we let happen?" in play here, but I don't control those other levels.
I'm responsible for C, so I'm gonna look at the C bit. Other people responsible for the other parts of this stack should, hopefully, take sincere responsibility for those parts. (I doubt it, though, lmao.)
cynicalsecurity 
cynicalsecurity@bsd.network
#crowdstrike T&Cs¹, paragraph 8.6 (HT: @JdeBP ), as usual the bit in caps is the best one:
TO THE MAXIMUM EXTENT PERMITTED UNDER APPLICABLE LAW, CROWDSTRIKE AND ITS AFFILIATES AND SUPPLIERS SPECIFICALLY DISCLAIM ALL IMPLIED WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE, TITLE, AND NON-INFRINGEMENT WITH RESPECT TO THE OFFERINGS AND CROWDSTRIKE TOOLS. THERE IS NO WARRANTY THAT THE OFFERINGS OR CROWDSTRIKE TOOLS WILL BE ERROR FREE, OR THAT THEY WILL OPERATE WITHOUT INTERRUPTION OR WILL FULFILL ANY OF CUSTOMER’S PARTICULAR PURPOSES OR NEEDS. THE OFFERINGS AND CROWDSTRIKE TOOLS ARE NOT FAULT-TOLERANT AND ARE NOT DESIGNED OR INTENDED FOR USE IN ANY HAZARDOUS ENVIRONMENT REQUIRING FAIL-SAFE PERFORMANCE OR OPERATION. NEITHER THE OFFERINGS NOR CROWDSTRIKE TOOLS ARE FOR USE IN THE OPERATION OF AIRCRAFT NAVIGATION, NUCLEAR FACILITIES, COMMUNICATION SYSTEMS, WEAPONS SYSTEMS, DIRECT OR INDIRECT LIFE-SUPPORT SYSTEMS, AIR TRAFFIC CONTROL, OR ANY APPLICATION OR INSTALLATION WHERE FAILURE COULD RESULT IN DEATH, SEVERE PHYSICAL INJURY, OR PROPERTY DAMAGE.
So very sorry for airports, airlines, hospitals and many other victims covered by the above… it says you shouldn't have used it even if we sold it to you.

Adrian Sanabria
sawaba@infosec.exchangeSome absolute legend figured iut how to automate the Crowdstrike fix with a combo of WinPE and PXE
 radare
radare 
radareorg@infosec.exchange
Need some more info to manage your calendar?
r2con2024 will happen in Barcelona on November 8, 9.
There will be two days of competitions, workshops and presentations. Get ready to share knowledge and have fun with friends!
We can’t spoil the location yet, so stay tuned for further updates!
Martin Seeger
masek@infosec.exchangeConcerning CrowdStrike:
We are now at t+26h. Please compare how much we knew about the xz-attack after less than a day with what we know about the chain of events of giant outage yesterday.
If something similar had been caused by an OSS component, we would see congress discussing a ban on open software in critical infrastructure already.
Jonas Wisser
jwisser@wandering.shopAs a manager, one of the most valuable things you can do is to model asking "dumb" questions—that is, questions that show ignorance about things you "should" know.
"Better to remain silent and be thought a fool than to speak and remove all doubt" may be all well and good in a social context, but in a professional context you have to be willing to ask questions that unlock information you need—even if you feel self-conscious about your current ignorance.